Mar 23, 2022
Paul-Arthur
Jonville
Ransomware attacks have been on the rise these past two years. 2022 is coming, leaving us with the following question: Will the attacks slow? What we have experienced so far leaves us without much hope these first three months. Some major ransomware attacks in 2022 have already happened, and the pace is at least equal to 2021. This is why we're creating a State of the Threat report: Ransomware attacks 2022.
The factors that led to the upsurge in ransomware attacks in 2020 and 2021 are still present. A growing remote workforce, an accelerating digital transformation, and strains on supply chains create incredible opportunities for adversaries. Several critical vulnerabilities left many organizations at risk, so it is no wonder that ransomware attacks increased by 150% between 2020 and 2021.
Ransoms initially asked are also growing, with an average of above $5 million in the US. The ransomware economy evolves, making ransomware an accessible tool, although destructive. The ransomware-as-a-service (RaaS) business model sets new trends and breaks records. It lowers the entry barrier for a ransomware attack to anyone with access to cryptocurrency.
Fortunately, defenders' strategies and accessories are also evolving to keep up with the threat. Although we are to fear a continuous upsurge of the attacks or, at the minimum, persistence, we can leverage better ways and tools, such as automation and orchestration of our solutions, to strengthen our stance.
Below, we will examine the general trends of attackers and provide answers for security teams to counter them efficiently.
Attackers look for your company's details and your vulnerabilities before launching attacks
When discussing cyberattacks, one must differentiate between undifferentiated and individualized attacks. As for individualized attacks, cyberattackers are increasingly looking to gain operational and organizational knowledge to know the company's environment before launching their attacks. This knowledge includes operational and financial details, such as annual budgets, employee counts, revenue statistics, and organigrammes.
Once they gather this information, attackers can target highly profitable sectors and work under permanent urgency (e.g., just-in-time industries that cannot afford prolonged disruption, such as transport or manufacturers).
Awareness programs and cyclical training are paramount.
Of course, most of these pieces of information are publicly available on the internet. They are usually parts of legal obligations, such as financial reports, margins, or budgets. We're not advocating for secrecy around these figures. However, a company should always know that these information pieces are available and constitute precious operational knowledge for attackers. This is why you must keep up the efforts to engage your employees across your company about cybersecurity awareness. This goes by gamifying your campaigns and training to dedicate resources and proper teams.
In addition to operational knowledge of the victim's environment, attackers are increasingly looking to understand the victim's overall attack surface. Knowing your systems and their potential vulnerabilities is also a way to access your network instead of deploying resources to compromise one of your employees' credentials.
Take Microsoft Exchange Server vulnerabilities, for instance. Using CVE-2021-26855, the attacker could access your vulnerable Exchange server without more knowledge than an email—there is no need to deploy social engineering to compromise BEC. From here, your organization has to have a near real-time understanding of its assets, particularly internet-facing ones, since they can be found via vulnerability scanners triggered by almost everyone as a reconnaissance technique.
Usually, an organization's attack surface includes the following:
Internet-facing systems and services
Vulnerabilities or unpatched systems
Use of specific solutions or third-party vendors
Cloud services
The first step to creating an appropriate response to this threat is to gain awareness of your attack surface. Creating and maintaining a Configuration Management Database is one of your priorities, although challenging, given the growth of remote work and BYOD trends in many companies due to the pandemic and structural trends. Automating the CMDB Discovery is an interesting way of keeping your CMDB as close as possible to your actual attack surface.
This way, one can be fully aware of vulnerabilities potentially affecting their system in the light of new threats arising and can proactively manage the patching of their vulnerabilities.
Remote Access is a privileged way to inject payloads
The exponential growth in Remote Access Abuse is linked to the development of remote work. With the pandemic, the traditional security perimeter is obsolete. Your system is increasingly accessed from various locations, increasingly outside the physical location of your enterprise, and from an increasing number of devices: phones or laptops, from secured or unsecured local networks. In some cases, it became necessary to provide administrative functionality to an environment. This is often necessary for remote branches or with remote employees (who have recently surged).
The concern arises when an organization deploys remote access without observing minimal security configurations. Often, companies deploy remote access quickly with a weak credentials policy or a single-factor authentication.
Such remote access systems are vulnerable and easily exploited. Attackers can and have taken advantage of compromising network access, even with correct security implementations. Even though some would say that the easiest way is to remove it altogether, actual business conditions are in dire need of it.
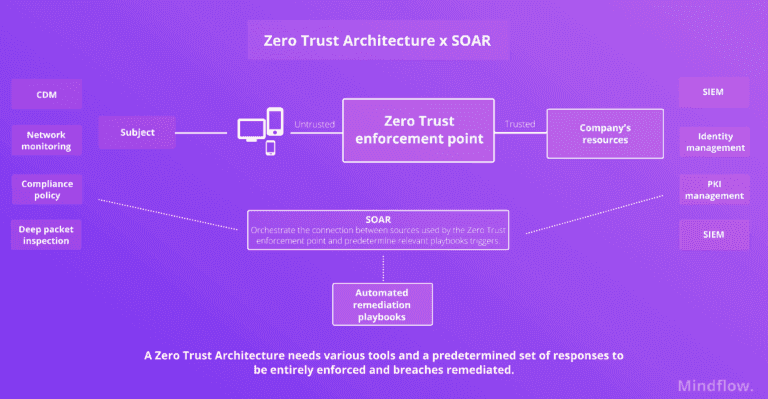
Advanced mitigation methods imply a zero-trust architecture powered by SOAR and accompanied by solid workflows of suspicious login and suspicious activity monitoring.
Vulnerabilities are Weaponized more and more quickly
With a new vulnerability out, a race often starts between attackers and defenders to exploit or patch it the fastest. The more critical the vulnerability, the more challenging the race is.
Attackers often win this race, at least momentarily, because they are often aware of the breach sooner than defenders, especially regarding zero-day exploits. But one trend is worth noticing. The pace with which attackers are weaponizing vulnerabilities is becoming quicker than before.
When looking at significant vulnerabilities of 2021, namely the Microsoft Exchange Servers vulnerabilities of March and April and the Log4j in December, adversaries moved from a vulnerable code to a working exploit in a matter of hours after the announcement of the vulnerabilities. In hours, the working proof-of-concept code (PoC) was available on the internet to install web shells on vulnerable Microsoft Exchange Servers, allowing potential attackers to quickly take advantage of vulnerable systems before relevant patches were even available.
In this case, there are two remediation ways for security teams.
The first is, of course, to wait for the patches and implement them as soon as possible. As we said above, attackers often exploit vulnerabilities quicker than defenders. Defenders must rely on network and endpoint alternatives to seek prevention, detection, and response opportunities.
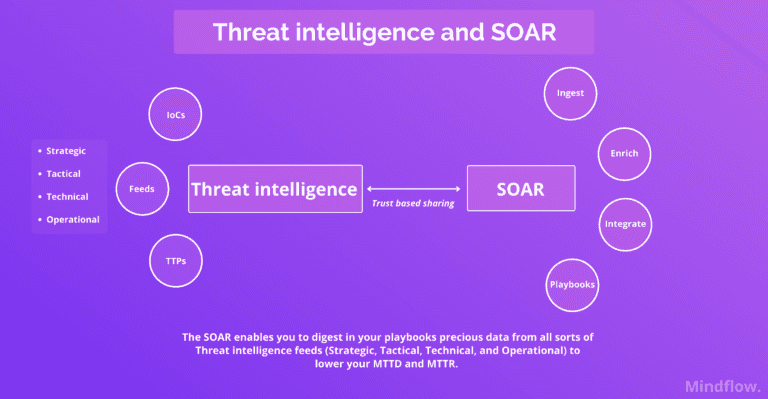
Gaining precise and accurate intelligence about the threat is paramount here. Automating IOCs and TTPs ingestion via Threat Intelligence feeds is necessary to have deep knowledge of potential attacks using these vulnerabilities in the attackers' profiles (and, therefore, TTPs). This will allow security teams to add particular network rules and endpoint signatures on top of behavioral monitoring to implement reliable defense mechanisms until patches are out and applied.
Attackers are trying to leave as little footprints as possible
Post-exploit, attackers are trying to leave as little footprint on the network and machines as possible to avoid traditional detection mechanisms based on Indicators of Compromise (IoCs) during their intrusion. To that end, they resort to fileless or malware-less attacks.
Fileless malware stores malicious code in the Windows Registry or a remote location. It leaves little to no malware on the disk, thus evading traditional file-based detections or IoCs. Fileless malware may also be memory-only. Attackers download and deploy the code directly into memory, evading file-based detections.
Attackers also use native binaries on the system to evade traditional detections and remain hidden in plain sight during an intrusion. Attackers do something different from what the binary was intended (such as using Powershell to open a web shell to maintain access). They take advantage of Living Off the Land Binaries (LOLBins), which are binaries of a non-malicious nature local to the operating system. They exploit them to camouflage their malicious activity, such as loading code into memory, downloading a file, or running a custom script.
When it comes to binaries, attackers can rely on custom scripts or exploit kits on a victim system. They use PowerShell and post-exploitation frameworks, such as Cobalt Strike, to assist in achieving their objectives. Although scripts and exploit kits leave on-disk artifacts, they also provide easy-to-use ways to compromise multiple systems and stay in memory.
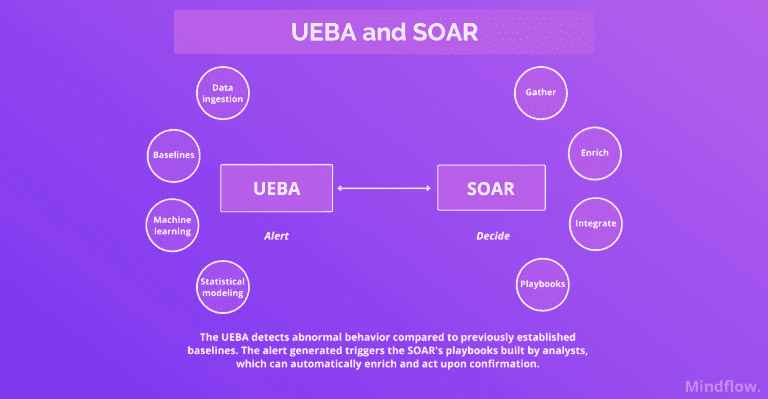
To mitigate these TTPs, organizations must rely on endpoint system memory monitoring and behavioral analysis tools. System memory monitoring can record what commands were executed on a system, regardless of the program running the piece of code.
Analysts can use tactics to flag action sequences or attempts to access memory. Based on these flags, systems can generate alerts for analysts to investigate. Memory monitoring could be set to detect activities related to a specific Microsoft Word macro that executes a PowerShell downloader, which is described as an intermediate stage in an attack.
Attackers leverage Automation to hasten lateral movements
When it comes to lateral movement within the systems, attackers are becoming increasingly quick to gain privileged access. The DFIR describes an intrusion that went from zero to domain admin control and ransomware deployment within 42 hours. Another post describes an adversary that went from zero to complete control in two hours.
Automation creates a predictable, thus detectable, sequence of events in predictable OS-based programming languages like PowerShell. As said above, security teams can use memory monitoring tools to create signatures for detection.
Furthermore, adversaries increasingly use offensive security tools, especially open-source toolkits and scripts. These tools are faster to deploy, but they leave footprints that an organization can easily track.
Ransomware attacks 2022: Security Automation and Orchestration
Attackers use automation to speed up parts of their attacks and infrastructure. Security teams should also use automation to harness its benefits: automated repetitive tasks, faster workflows, reduced errors, and more time for more complex tasks.
Countering ransomware attacks requires many tools provided by different security vendors. Navigating between them implies time lost and fragmented frameworks. Also, there's an answer to be found in Orchestration. Tools acting as the glue between all of these solutions, such as Security Orchestration, Automation, and Response, are the pinpoint remedy to reduce the pane of glass and address the lack of automation.
A SOAR can:
Automate repetitive and low-value-added tasks such as triage or parsing
Design playbooks and determine specific triggers (an event or scheduled) to pre-build incident response workflows and harness machine-speed capabilities: circumvent ransomware attacks with triggers based on abnormal activity detected on an endpoint
Orchestrate flows between tools, such as intelligence gathered on TI feeds to sharpen detection tools (up-to-date IOCs and TTPs and hierarchization based on criticality)
Free up time for analysts to focus on higher-value tasks.
At first, leveraging another seems redundant and prone to more complexity. Yet, next-generation SOARs like Mindflow are based on a new set of values, far from your traditional SOAR. Mindflow uses the no-code approach to drastically reduce the time and skill barrier your analyst needs to master and properly operate it. Pre-built actions and playbooks help your analyst create fine-tuned incident response plans to adapt to the evolving threat continuously: constantly ingest new IOCs and TTPs to update your detection rules or scheduled scans to keep your CMDB up-to-date.








