Okay, bad news first. At some point, every company will be breached by an attacker. There’s no 100% security-proof system. This is why you need a User Entity Behavior Analytics (UEBA) tool.
Indeed, attackers can breach your firewalls, send you malicious e-mails, or even bribe one of your employees to gain access to your firewalls. Your protection tools and systems can quickly become obsolete when facing rapidly evolving threats.
A UEBA gives you an extra layer of protection at the core of your system when your first layers of protection have failed, and the attacker is inside.
Below, we’re going to learn together:
- What exactly is a UEBA;
- Can you combine UEBA and SOAR?
- Why you should have both.
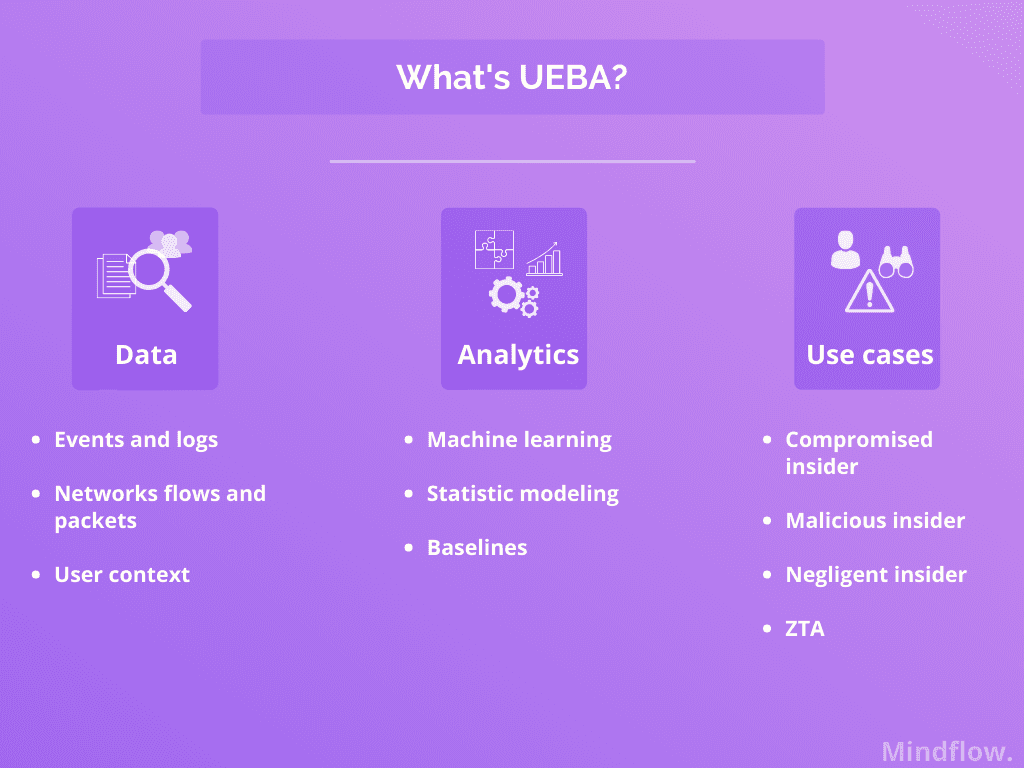
What’s a UEBA?
A UEBA is a type of cyber security process slightly different than your usual firewalls or detection and response tools. As its name states, it focuses on behavior monitored rather than precise Indicators of Compromise (IoC). To that end, there’s an essential emphasis on expected behavior, which is used to detect what can be called abnormal.
Let’s take an example to introduce the process. If one of the users on your private network is used to downloading a few files every day, but suddenly they start to download thousands of them, the UEBA detects this abnormality and goes red. It would notify the user concerned and a security agent to ensure this abnormal behavior isn’t malicious.
But how can a UEBA detect such deviations from normal behaviors? It uses several technologies to acknowledge past behaviors and compare them to new ones: machine learning, algorithms, and statistical analyses, to name a few. This is known as baselining. To that end, it ingests data from a general data repository such as a data lake or data warehouse or through a SIEM. They should not deploy agents directly in the IT environment to collect the data.
This way, a UEBA can detect a deviation from the previously established pattern about a particular user. Thus, it shows which anomalies could result in a potential, tangible threat. UEBA can also aggregate the data you have in your reports and logs and analyze files, flow, and packet information.
Here, you’re not going after security events or monitoring all your devices. Instead, you’re going to track all the users and entities in your system. Threats that we would call insider or internal and would divide into:
- Compromised insider: an employee has given access, unintentionally, through phishing for instance, to an attacker.
- Malicious insider: employees, former employees, contractors, or associates deliberately cause harm to your company by stealing intellectual property and/or customer information for financial interest or to cause disruption.
- Negligent insider: employees or contractors deliberately bypassing security policies out of convenience or incompetence.
As we said at the beginning of this paragraph, a UEBA doesn’t focus on your typical IoCs when detecting threats. The main reason is that it focuses on threats already in your systems. This is why we say that it’s the last layer of protection in your security architecture.
In this regard, even though a UEBA relies on cross-organizational security data to work, which is usually collected by your SIEM, these two tools are different in how they work and what they’re looking after.
A SIEM is an aggregation of different and complex tools and technologies that aims to give you a comprehensive view of the security of your system. It uses data and event information to see standard patterns and trends and alerts you when abnormal trends and events occur. A UEBA works the same way, but it uses user behavior information to detect normal behavior and what’s not.
A SIEM, however, is rules-based. Facing a SIEM, advanced hackers can work around or evade the rules. UEBA, on the other hand, does not rely on rules. Instead, it uses risk scoring techniques and advanced algorithms to detect anomalies over time.
The benefits of a UEBA
Some would say, “why would I need a UEBA? I have all the next-gen security tools in my security stack!”
First, bear in mind that the human element is the cause of 85% of successful attacks: compromised, negligent, or malicious insiders, all of them include a human as the primary vector of the successful attack. Second, even though cyber security tools are evolving, defense or, more often than not, profoundly reactive.
As a result, we’re confronted to waves of rapidly changing threats. We’re trying to cope with the attackers’ ingeniosity discovering and weaponizing unknowns.
Combine these two elements, and you have soon-to-be-breached systems. This isn’t to be alarmist or defeatist, no. This is about facing the truth concerning cyber security. No matter what you’re using to defend yourself, you can’t and won’t achieve 100% impermeability to the surrounding threats; there are too many unknown variables to be sure of your absolute security. Thinking that if you’re protected against this or that threat makes you’re thus invulnerable leads you to be caught off guard when it’s time.
Acknowledging this helps you prepare for this eventuality instead of facing it naked, unprepared.
We can think of this as one of the last inner layers of defense of your company once the enemy is inside its walls. You want to be able to keep track of your enemy once it breaches the gates, to know where they’re going, what they’re targeting, and where to hit. More, sometimes, you wouldn’t even be aware of the breaches until enemies advance on the kill chain to deliver their payload.
The bottom line is: don’t only focus on preventive measures but also insider detection.
As always: think of an onion or a Vauban fortification, multiple layers of defense complementary to each other. The goal is enhanced security posture, with no holes left behind.
Can you pair UEBA and SOAR?
Okay, we’ve seen what’s a UEBA and its benefits. We know that UEBA is an extra layer of protection, having earnt its place in your security stack. Still, can you maximize its efficiency and efficacy within your system?
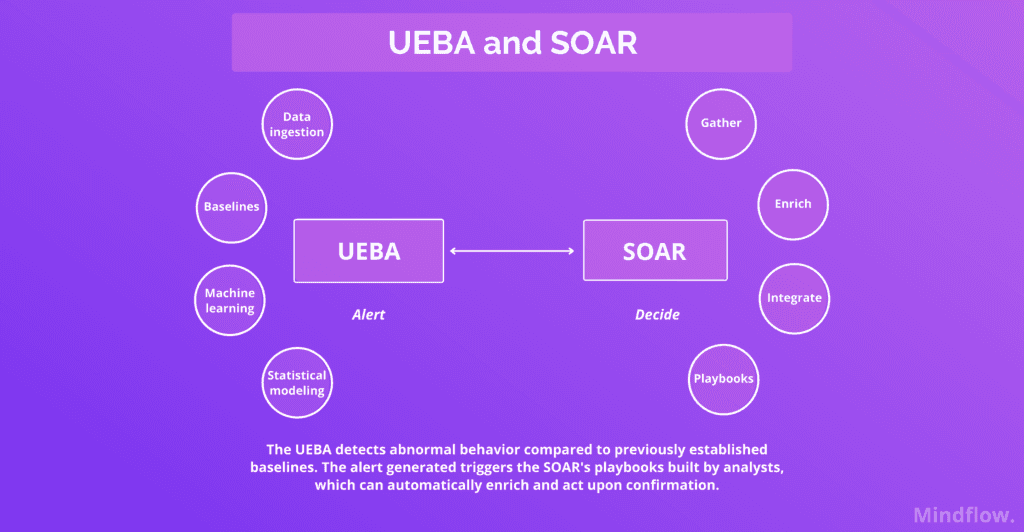
This is where the Security orchestration, automation, and response (SOAR) helps us. As we’ve said multiple times here, a SOAR is designed to orchestrate your tool stack and automate information sharing and decisions via playbooks. In these playbooks or workflows, you’re connecting the tools you’re using to automate the flows between them.
Why is this useful? First, most of the time, companies are using an increasing number of tools coming from different providers, thereof lacking semantical awareness. The SOAR is a wrapper. It connects them and enables the automation of flows. As such, it makes your system coherent as a whole: an orchestrator.
As a layer of defense, it has to be connected with the other tools you’re using to deliver its maximum efficiency. As an informative tool about the whereabouts of your users’ activities on your network, its main mission is to provide an exhaustive vision, not to act.
However, threats can materialize fast once they’re delivering payloads. We’re talking about machine-time speed. Can you imagine a human having to switch between alerts coming from the UEBA and mitigation processes? You need to leverage the power of your other tools in such time to mitigate active threats. A SOAR helps you to decide.
By integrating UEBA and SOAR capabilities, security teams can proactively detect and react to complex security events and perform automated behavioral profiling while also automatically interacting with IT and security systems to mitigate incidents.
Let’s take the example of a malicious insider, the most challenging insider threat in terms of complexity. The user is 100% legit. The only things that could uncover them would be abnormal traffic or suspicious privilege escalation. The UEBA acts as an alert if this behavior diverts from its baseline. However, you need to act fast to counter eventual data theft once you’re alerted.
Working old style would make you switch between your user management system, endpoint monitor, firewalls, or proxies to neutralize the user’s activity and potential data outflows.
The SOAR enables you to predetermine these steps in playbooks and set triggers. For instance, a UEBA alert can trigger your user privilege revocation playbook. The security agent is notified of the alert; he can even be advised on which steps to take next. The playbook can autonomously mitigate the threat from detection to remediation: an automation platform.
Conclusion
The sky’s the limit when talking about the SOAR orchestration and automation capabilities. We’ve already talked about EDR and SIEM pairing benefits with a SOAR. Here again, we’ve shown that a UEBA can benefit immensely when oversaw by a SOAR: you’re able to act upon alerts via the SOAR platform.
All in all, a SOAR is a wrapper. It enables you to make the best out of your tools and build advanced security processes such as a Zero Trust architecture, for instance.
