The Cybersecurity Mesh Architecture is one of the new concepts popular these days to describe the future of cybersecurity. Among various creations of the last year, this one is worth looking at and thinking about.
It relies on concrete facts about what happened in the last two years and what the future is made of. It’s a different way of thinking about cybersecurity in a world where remote working, cloud workloads, and storage are increasingly becoming the norm.
Security professionals need to evolve their security infrastructure to be more flexible and efficient. The environment requires a more reactive, more composable, and increasingly more interoperable security infrastructure, relying on best-of-breed solutions supporting their infrastructure’s layers.
Sounds interesting? Let’s look more closely at how does this concept works:
- What has changed to create the need of a new concept
- The SOAR is one of the key pillars of the Cybersecurity Mesh Architecture
The last two years brought intense modifications in the way enterprises work. Companies had to rely on extensive remote work and migrate to the cloud for better flexibility. These were preexisting trends, but the COVID-19 and administrative lockdowns favored the movement.
With many more assets outside of the traditional security perimeter, breaches multiplied at an alarming pace, fostering the need for more and better cybersecurity.
Although cybersecurity investment rose sharply since the beginning of the outbreak, accompanying the consideration of the vulnerability of most companies worldwide, concepts about the matter didn’t change much.
There is a need to define a new cybersecurity approach according to the current trends.
Indeed, companies went all-in in their digital transformation to sustain activity. Many of them are now relying on tools outside of their traditional perimeter: cloud-native apps or remote apps, for instance.
Assets are increasingly located outside the traditional security perimeters, globally dispersed, and constantly moving. Cloud migration is now a strong trend that is leaving security thought for on-premises not prepared to regulate accesses and workloads on distant connexion, from anywhere.
More, companies are going multi-cloud to become more resilient in the face of disruptions. With every cloud provider supporting a different set of policies, creating a consistent security posture across cloud providers is challenging. The huge on-premises estate of services found in most organizations only compounds the challenges.
Users, devices, applications, and data have left the traditional office and data center. A single network perimeter no longer exists. The “inside is good and outside is bad” becomes more blurry.
Identity and context have become the ultimate control plane in a distributed environment that supports assets and access from everywhere. CSMA’s distributed identity fabric provides trusted access by our workforce, clients, business partners, and things.
Legacy controls thought for an enterprise located in a unique location, based on on-premise infrastructures, are inadequate to protect virtually (and physically) fragmented companies.
Today’s distributed and rapidly growing digital landscape requires a new approach to security architecture. Existing architectural processes are overly fragmented. This increases security risk, and operational overhead, especially in an environment where making sound risk decisions requires orchestrating a growing number of risk signals.
Employees connecting from unsafe networks on remote working bring a wide variety of threats. Adversaries exploit this situation to identify holes left as security lags behind this new paradigm. Data, operations, and systems are targeted. As a result, breaches are multiplying.
In a traditional data center, network perimeter security was a common mechanism for controlling access. Identity and context have become the ultimate control surface within a distributed environment that supports assets everywhere and access anywhere.
A proper defensive posture requires eliminating silos and inefficiencies, both from an organizational perspective and within technology, as the Cyber Fusion Center already aims. Consequently, the security environment needs to adapt. A new approach needs to be assessed:
- more flexible, composable
- more scalable, as the perimeter fluctuates
- enabling semantical awareness between your tools
The Cybersecurity Mesh Architecture is a holistic approach to security
Existing approaches to identity and security architectures are insufficient to meet today’s rapidly changing demands. Cybersecurity Mesh, understood as an architecture of your security posture (CSMA), helps to provide a standard, integrated security structure and posture to secure all assets, whether they’re on-premises, in data centers, or the cloud.
The Mesh follows the concept of a distributed approach to network and infrastructure security. It changes the understanding of the security perimeter in your company. It isn’t a unique fortress anymore. The Cybersecurity Mesh Architecture lowers the granularity of the scope by creating unique perimeters around every person or machine on your network.
The Mesh is about building as many perimeters of security as access points.
But this isn’t about decentralization. Control and authority are still managed from a centralized point. It’s more about deconcentration, where the central authority manages and controls. Each control and policy is distributed across the entire network and closer to each identity evolving.
You’ll recognize the likeliness with a Zero Trust architecture, where devices, services, data, and applications are accessed securely from anywhere by humans or machines with strict identity verification and authorization.
If you think about remote working, it makes sense.
CSMA enables stand-alone solutions to work together in complementary ways to improve overall security posture by standardizing how the tools interconnect. In short, it’s a collaborative approach to create cohesion. Cohesion needs fewer resources to work correctly and enhance each action undertaken.
There are too many separate tools with too many separate dashboards. For example, today’s security and identity deployments consist of multiple tools that often are not fully integrated (for example, they might be only loosely coupled by supporting federated authentication). In other cases, numerous tools may duplicate supporting functions.
Operating these tools requires many separate dashboards, multiple policy administration points, and maintaining many ad hoc integrations. This problem is exacerbated when new security or identity needs surface, and new tools appear.
Cybersecurity mesh architecture is a composable and scalable approach to extending security controls, even widely distributed assets.
Rather than every security tool running in a silo, a cybersecurity mesh enables tools to interoperate through several layers. Its flexibility is especially suitable for increasingly modular approaches consistent with hybrid multi-cloud architectures. CSMA enables a more composable, flexible, and resilient security ecosystem.
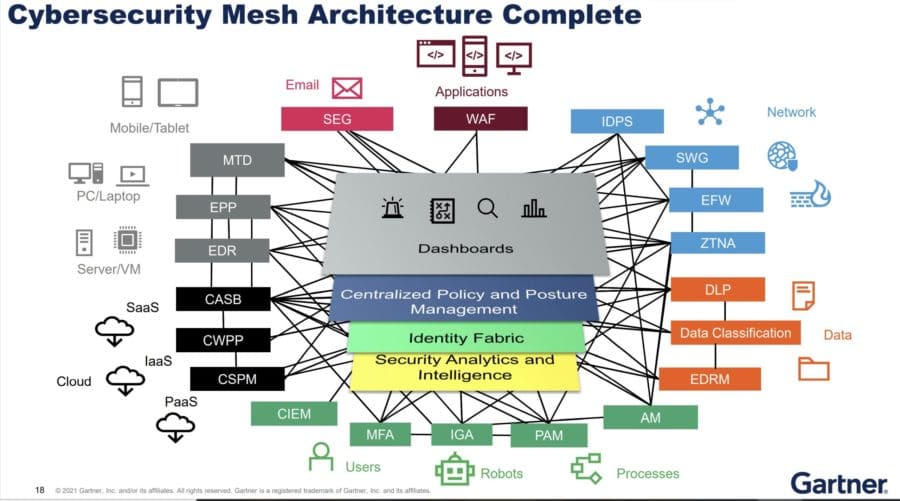
Here, you acknowledge that the Cybersecurity Mesh Architecture comprises four layers that enable precise security controls to work together collaboratively and facilitate their configuration and management. This architecture fosters composability, scalability, and interoperability for security controls.
These layers are:
- Security analytics and intelligence combine data and information between your technologies and enrich threat analyses to trigger appropriate remediations.
- Distributed identity fabric provides in-depth and flexible capabilities to build a Zero Trust Architecture adapted to your needs (directory services, adaptive access, decentralized identity management, identity proofing, and entitlement management).
- Centralized policy and posture management to distribute a centrally defined policy into the native configuration of each security tool.
- Dashboards to offer a comprehensive view into your security ecosystem, enabling faster reactions from your security teams.
The SOAR (Security Orchestration, Automation, and Response) is a way for your security analysts to integrate the management of workflows in a unified platform. It blends perfectly as the security analytics and intelligence layer that a Cybersecurity Mesh Architecture needs.
Integrating multiple security tools remains a necessity. Other companies are starting to provide CSMA-like approaches in unified solutions. However, as we said in a former article, these monolithic solutions can be attractive thanks to their unified ecosystem.
However, you’re first locking yourself in this ecosystem, leaving interoperability at the doorstep. Also, consolidating best-of-breed solutions in a single entity is rare, if not nonexistent. Combined with the lack of interoperability, you’re exposing your company to unfillable holes in its defenses and laborious and precarious ad hoc integrations.
As you begin to build the supportive layers of your cybersecurity mesh architecture, you’ll realize that the tool to enable interoperability between your distributed security solutions will be critical to the security mesh.
An API-driven, standardizer technology and extensible analytics platform is the best technology to fit in because the one thing your cybersecurity mesh architecture needs is orchestration and automation.
Orchestration to break silos and enable semantical awareness between your technologies by standardizing communications. Automation to allow real-time sharing between all tools and flexible and scalable postures.
The SOAR, a precise tool developed to fulfill the needs for orchestration and automation, is the answer here.
The SOAR as an orchestrator finds its way in a Zero Trust architecture. It also finds its place in this strategy.
More, agnostic SOARs, like Mindflow, are, at the core, developed to answer these exact needs. They rely on continued integrations to the best-of-breed technologies in the market, no matter the vendors. They’re enabling full composability and flexibility of your architecture.
These SOAR should be the pillars of this Cybersecurity Mesh Architecture new paradigm.
