Aug 9, 2022
Hugo
David
Today we're to talk about a very common task analysts face every day, malware analysis via phishing emails (or malspam), a classic, I may say!
As all of you guys know already, we have to study this regarding the whole environment. Indeed, we're facing a threat escalation in number and variety.
In this environment, phishing emails are still the favorite vector of attack. Performed in bulk, this isn't an expensive attack pattern. Millions can be sent, and even if attackers have a low success rate, below 10%, this pattern is still valuable as the cost of conducting massive attacks is insanely low. Spear Phishing - not your average Nigerian Prince asking for some money - presents a higher success rate, almost ten times higher than mass and undiscerned phishing, but it's also costlier. Attackers have to perform research on their target and adapt their attack.
All in all, phishing is working and is still the n°1 attack vector to date.
With such a vector of attack at their disposal, attackers don't hesitate to use it to send malware as attachments. Analysts thus have to monitor and analyze emails and their attachments to filter benign from malicious.
Considering the tremendous growth of attacks via email phishing every year, these analysts have difficulty analyzing all the potential threats.
As we said in our last article, the issue concerns the tools analysts use, not the workforce. Quick TL;DR: insufficient workforce + qualification issue + people in place are being burned down = feedback loop. The solution lies in finding new tools to answer the core issue: the lack of automation.
This is where the SOAR comes in. As the pinpoint orchestration and automation platform, it can transpose manual labor into computerized and automated processes. The result is tasks made faster and more consistent with the same amount of workforce.
We will study the email phishing malware analysis case to understand the benefits of the SOAR.
How an analyst manually performs malware analysis?
How can the SOAR help you perform Malware Analysis?
Usual handling of Malware analysis
Roughly put, steps manually performed by the analyst to analyze a potential malspam are as follow:
First, end users forward an email to the SOC. The assigned analyst takes on the duty of analyzing said email.
According to their response plan, here comes the first task. The analyst has to manually extract artifacts: sender IP, email address, subject, attachment file's hash, and email corpus.
For each of these artifacts, the analyst must submit it to their favorite Threat Intelligence database to see if there are existing reports.
In the first round of threat intelligence analysis, the analyst may want to confirm or refute the results. They thus go for a second round before their second favorite TI database.
Once results are generated, the analyst must compare first and second-round results and risk scores to assess an average risk score.
The analyst can close the case if the risk is benign - i.e., no hits on databases.
However, if results are uncertain - generating a risk score between benign and malicious - the analyst has to perform additional investigation. The analyst can send the attached file to a sandbox to run the file and witness which processes are launched.
Should the risk score (or the advanced investigation if needed) point toward a malspam, the analyst goes on to the containment phase, where they first quarantine the analyzed email and look for similar emails in every company's mailboxes. For every hit, the analyst pulls them into quarantine. Finally, to prevent similar attacks - ones that could use these newly found and confirmed IOCs - the analyst has to update exclusion rules on the Firewalls with the discovered IOCs.
From what we wrote, we can conclude a few things. First, emails are forwarded to the analyst. Second, the analyst has numerous tasks to perform before deciding about the mail's maliciousness. Third, they have to switch between the mailing solution, threat intelligence database to analyze multiple artifacts, a sandbox to monitor file execution, perform manual comparisons, pull the email solution again, maybe interview the end-user, and finally update firewall rules.
Lots of actions and room for errors, omissions, and, most of all, repetition that generates the formers.
We're going to see that, with the SOAR, you can predetermine all of these steps, leaving the human in charge of the crucial decision steps.
Handling Phishing email Malware Analysis with a SOAR
Indeed, as shown above, steps to analyze a malspam are known, and each analysis implies their repetition, ad nauseam. The next move is to introduce automation in it.
With the SOAR, you can take all incoming data to decide what will be the following steps in an automated manner. In another way, you can predetermine precise management for each use case and pre-configure the response by pulling other tools, 3rd party actions such as your NGFW, or disabling an account.
You can pull tools thanks to the native integrations the SOAR comes with. This is where industry-agnostic next-generation SOARs show their first difference from traditional ones. Their native integration library is more comprehensive and thus necessitates less work to implement new ones.
Whatsmore is the accessibility delivered by these new SOARs. Far from their firstborn, next-gen SOAR are developing low to no-code approaches to ease the handling. Creating workflows is becoming a drag-and-drop game, where analysts pull actions and conditions to determine a given process. Configuration of these steps is where low and no-code start to differ. Low code keep the need for programming skills. No-code is pushing the approach to the maximum by withdrawing configuration by code.
To sum up, through the next-gen SOAR, you build workflows by pulling natively integrated tools to define conditions and actions accordingly.
Let's dive into the malware analysis through the SOAR.
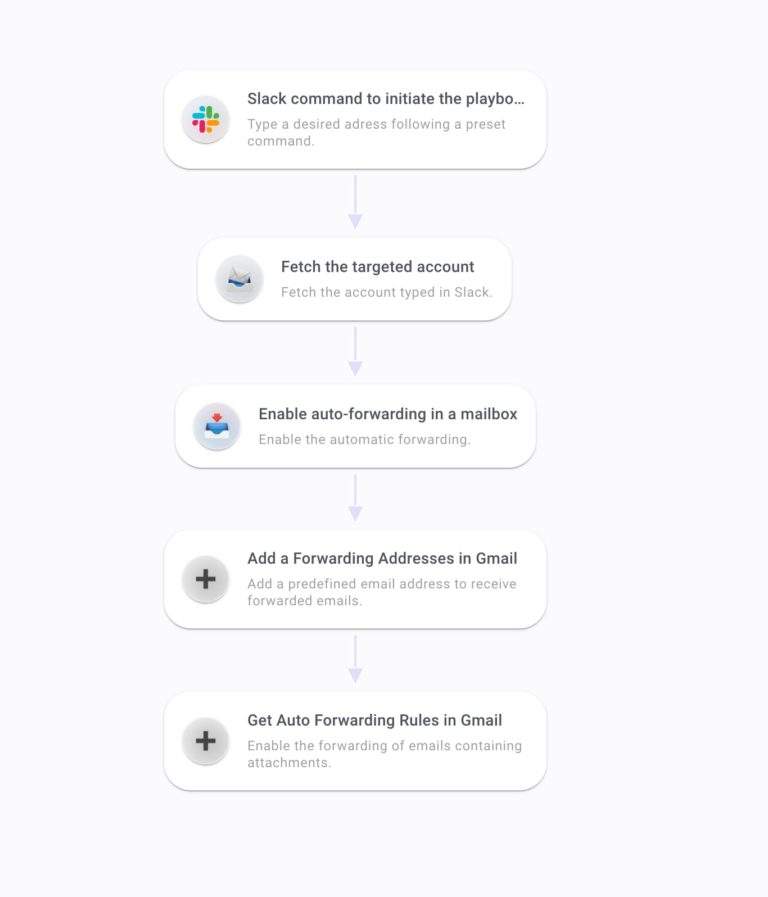
The first thing the analyst would do is to preset mailboxes and forwarding of emails. The analyst can also automate this through the SOAR by pulling their mail solution, Gmail or Exchange, and bulk selecting all employee's emails to add forwarding addresses and get forwarding rules.
Then, they can instruct auto-forwarding of emails containing attachments to a predefined email address.
This playbook can be run on its own, periodically, or can be individualized to fit in an onboarding playbook as a setting up step after the creation of the email address.
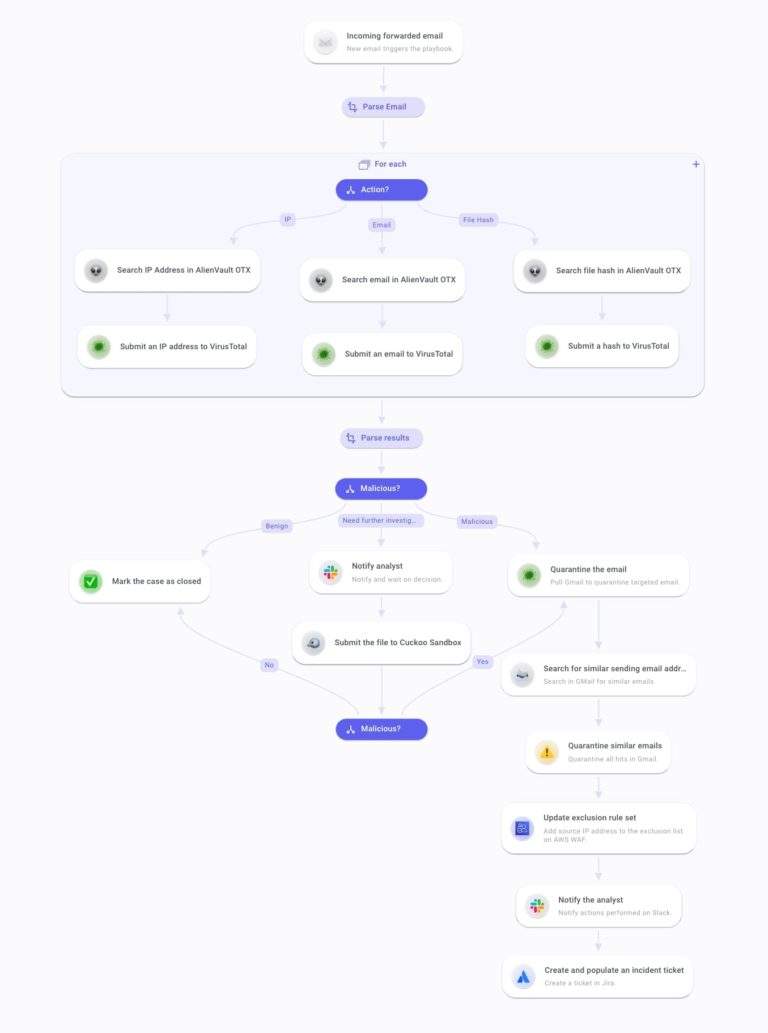
Now on to the second playbook. Incoming emails act as triggers to the workflow. The first step will be to extract and parse all the data contained in the mail: metadata, attachments, and content.
Then, each metadata (source IP, subject, sender email address, and file hash) will be sent to 2 or more threat intelligence databases. Here, we'll use VirusTotal and AlienVault OTX.
Results of the queries are sent to your communication channel that notifies the analyst. The same goes for risk scores after being compared and averaged to reflect a middle ground between the two platforms. The analyst can then assess the maliciousness of the submitted email.
If the risk score equals 0, the analyst can choose to close the case. If the risk score reflects a malicious attempt, the analyst can initiate the containment and remediation processes. Suppose the risk score doesn't reflect benign or malicious attempts. In that case, the analyst can choose to start a deeper investigation by submitting the attached file to a sandbox platform. Here we'll use Cuckoo Sandbox.
Results are gathered and also sent to your communication channel.
The case can be closed if the results point to a benign file. Else, the analyst can proceed to initiative containment and remediation.
The containment step begins by pulling your email solution and quarantining the target email. The analyst may search for emails containing similar IOCs in your company's mailboxes. Hits can then be quarantined.
Finally, the analyst may consider pulling your Firewall solution and updating the ruleset to add the malicious source IP to the exclusion list.
Once done, the analyst is notified of the actions performed via the communication channel and the ticketing solution they can close.
Conclusion: Automated Malware Analysis saves time!
Malware analysis is one of the first use cases SecOps wants to automate. Traditionally, analysts handle malware analysis manually. As we saw, even though the process is relatively simple, it takes time when you do it manually. You have to perform numerous tasks with various tools, back and forth, and perform manual comparisons.
With the SOAR, tasks needing human action in malware analysis are reduced to only a handful at best. Others are performed at computer speed. It saves time and limits tedious labor. On top of that, orchestrating and automating the malware analysis adds consistency to the process. Every email is processed the same way, limiting omissions.
A workflow that would manually take hours now takes minutes for a consistent result. This is how next-gen SOARs tackle the structural challenges cybersecurity practitioners face today.