Jul 29, 2022
Hugo
David
This week, we will talk about cybersecurity challenges (like every week but even more today!), the attrition rate, attractivity, fatigue, and skills issues in cybersecurity jobs.
It's commonplace to know that a security analyst's job is stressful. The pandemic added even more stress to their shoulders. The number of initial alerts (before their filtering) grew and is still growing as of today, only making their jobs worse. On top of this are the other usuals: shortages, qualifications, and the need to stick with an ever-evolving landscape (threats, tools).
It's no wonder the cybersecurity field is riddled with stats like alarming churn rates.
Below, we're going to deep-dive into the latest stats as of 2022 released by the ISACA, examine, examine these cybersecurity challenges to understand their origins, and try to find answers to them.
This journey will go as follows:
the well-known alert fatigue phenomenon,
the workforce issues,
understand the retention nightmare,
and, finally, how to tackle this issue (unexpected hint: SOAR!)
The Alert Fatigue phenomenon
Before we start our journey inside the cybersecurity challenges, we're giving you a quick heads-up about alert fatigue. Alert fatigue happens when people tasked with answering alerts are overwhelmed by them. Without the right processes to handle significant inflows, people cannot filter and adequately treat alerts as they come.
After a while, these people learn that there is a good chunk of false positives and duplicates (between messaging apps, email, or notifications) in this flow of alerts. To find a way to handle the influx, they ignore some of them, deeming them ab initio irrelevant or inconsequential.
In some sort, this ever-increasing flow desensitizes them. It occasionally leads to missed or ignored accurate alerts or delayed responses because of inadequate hierarchization.
The issue is that some of these alerts are important events by themselves or point to a real event occurring in the systems.
There's a well-known example from the healthcare field to illustrate this. Under constant pressure and incoming alerts, clinicians ignore clinically unimportant alerts that could cause an incident to spread and cause serious harm to patients.
The same thing happens in the cybersecurity field. Analysts tend to choose between two options because of the sheer number of alarms every day and the lack of adequate handling capabilities: adjusting alert settings outside of safe parameters (we all know that one company says they have only a handful of incidents weekly) or ignoring alerts when they're coming up.
Either way, it can lead to missing accurate alerts and potentially ignoring devastating incidents, allowing an ongoing breach to go on for months before finally detecting it.
But what's the real issue here? Have analysts choose not to look at every event on their screens? Let's not forget that, on average, security teams have to face up to 11.000 alerts daily, every day, every week. Plus, the processes to handle these alerts are still wildly manual. It means that SecOps has to repeat thousands of times the same processes and, most of all, the same basic actions, such as the initial triaging alerts between real and false positives. All in all, this essential initial step takes up to 20% of an analyst's time.
Indeed, analysts know how this way of working slows them down. Almost 3 out of 4 analysts agree that manual processes slow triage processes (Forrester).

See Modern Times? Same thing. This is alienation. Having to blow out fires occasionally, not having time to accomplish other, more rewarding tasks. But that's not all. As in any flawed system, their operators are the first victims when they fail. In the cybersecurity field, breaches can have enormous impacts on multiple pans. As the company's capital becomes increasingly digital, it represents a valuable target to attackers. One flaw, one ignored incident, can lead to an open breach in your systems and access to attackers.
When this happens, the first line of defense feels responsible, even more so when the breach is significant. This turns into added responsibility on top of pressure and hours piling on. Overall, this work environment impacts the quality of cybersecurity professionals' lives, leading to stress and exhaustion.
Now, we have to think about the initial cause. The number of alerts? Many companies can do better, but when you look at the budgets invested in the last years versus the results, I wouldn't count on piling more greenbacks to solve the problem. Cyberattacks are here to stay and growing in number and sophistication daily. Broader evolutions, such as cloud migration, structurally nourish this trend.
Another way to look at this challenge is by looking at the processes in place to handle it. This is where automation AND orchestration (people often forget that these items are equally important) will play. Follow the journey or jump to the last part of this paper to read about it if you can't wait!
The Cybersecurity Workforce issues
There are two challenges when discussing the cybersecurity field workforce: shortages and skills gaps.
Shortages
We already wrote on the workforce shortage issue here a while ago. To put it briefly, even though the workforce gap in cybersecurity was slightly reduced in 2021, from 3.1 to 2.7 million people needed, there's still a structural offer deficit compared to the demand being boosted by the recrudescence of attacks.
As a result, when asked about their staffing level, 3 out of 5 companies declare that they're somewhat or significantly understaffed, which is growing in regards to the year prior. It's not that they are not even trying to hire; they are! Among all companies, 60% of them have open positions that are mainly targeting technical cybersecurity professionals.
When you add up staffing shortages and alert fatigue, you have a situation that can have disastrous consequences. Picture this: understaffed and ill-equipped teams face thousands of alerts daily.

Skills gap
In addition to the workforce shortage, security teams have to endure a fast-paced, evolving landscape. Besides the relative increase in the sophistication of attacks and the incremental changes the industry brings, most analysts are confronted to various degrees with the advent of the cloud.
First, consider that, according to the ISC2, the cybersecurity field is particular in that almost 50% of practitioners don't have a computer science degree or limited experience and thus have little coding knowledge.
If the cloud addresses scalability or infrastructure investment, it also increases your attack surface by changing the traditional security perimeter. Yesterday, it was designed around the enterprise office, and it is now high in the cloud, accessible from everywhere worldwide.
Thus, security infrastructure needs to evolve, and cloud computing skills are in dire need in most security teams. Right after the soft skills (a whole different story), 1 out of 2 companies indicates that cloud computing is the second-largest skill gap among cybersecurity professionals (52 percent).
This adds to what we've described above, and it starts to be impressive when you add. Alerts are growing, people shortages, and skills gap = talent war.
The retention issue
Yes, before we discuss how we can solve this issue, we'll first examine the talent war and the retention issue most companies face regarding cybersecurity professionals.
Although everyone in 2021 saw a hike in employee retention among cybersecurity teams, this year's shows a reversal. When looking at the broader picture, the increase in deterioration in retention is explained by the pandemic. In 2020 and mid-2021, because of economic uncertainties, hirings slowed, and thus, movements between companies slowed as well. As a result, employees stayed longer and put their career projects on hold.
With the second half of 2021 and 2022 coming, economies are re-opening, and companies are starting to hire again. Consequently, the retention rate is severely hit, up to 3 out of 5 companies today.
Hit because, in the cybersecurity world, 1 out of 2 reasons a cybersecurity professional leaves their job is because other companies have recruited them. When you look at those who left because of insufficient incentives (salaries, bonuses, and development opportunities), which means that they were offered better alternatives elsewhere, the figure is up to 80%, which signals a fundamental disconnection between how their management sees them.
But there's more! Returning to the first things we said initially, cybersecurity professionals also point to the high-stress load induced by their jobs as contributing to their departure.
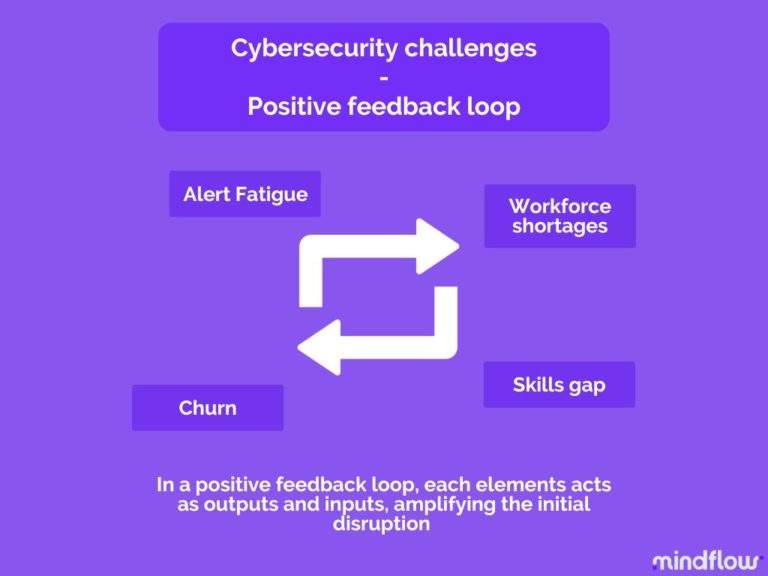
Ultimately, it leaves already understaffed companies even more vulnerable to attacks. As reports show, there's a correlation between all those stats. Alert fatigue, staffing levels, retention, and attacks are somewhat interrelated. Out of all the companies that reported attacks in 2021, 6 out of 10 are understaffed and have difficulties in hiring. They're vulnerable, understaffed, and have problems hiring! In this vicious circle, outputs are routed back as inputs and make a cause-and-effect chain, forming a positive (amplifying the disruption) feedback loop.
Keys to tackling cybersecurity challenges
What's the initiating input of the positive feedback loop? As we said in the first part of this paper, the initial input is the inadequacy of processes to handle the increasing flow of alerts companies face.
However, it doesn't mean that you only have to bring answers to this unique problem. We also said above that every output in this chain acts as an input. This means that they also have effects on their own and need answers, too. It's only by working on every part of this loop that you're going to solve the issue as a whole durably.
To that end, companies can use various means.
Some have already improved benefits and bonuses to address the retention issue. They can also increase their budget and allow for the development of their analysts' careers by taking on their part the fees needed to pass certifications. Doing this increases their attractivity by creating career paths inside their organizations and providing ways for skills enhancement.
Still, regarding retention capabilities, companies can put better task rotation and time management schedules in place. Establish and implement a rotation system to enable employees to spend less time triaging alarms and more time doing more rewarding tasks. Redefine responsibilities regarding breaches and improve in-store management in such cases. Not everything happens because of cybersecurity professionals' failures; they need a management tier to explain this to them to preserve their morale after breaches. Longer hours should mean more benefits. It's costlier, sure, but it's also more human.
As we have said in numerous articles, the answer to addressing the qualifications gap lies in adopting a new approach to solving cybersecurity challenges. The chase for top-tier talent can be replaced by lowering the skills needed to operate as a whole. This can be done by purchasing no-code solutions that can be placed at the core of your cybersecurity architecture, from which your employees can orchestrate all of their processes.
Finally, to act on alert fatigue, there's, of course, automation. Brought up as the ultimate solution for years, it still has to show its full potential. Here, we said that the main obstacle to the advent of the age of automation in the cybersecurity field was its lack of maturity regarding accessibility. Too technical and too expensive, automation capabilities are still a niche available to a happy few.
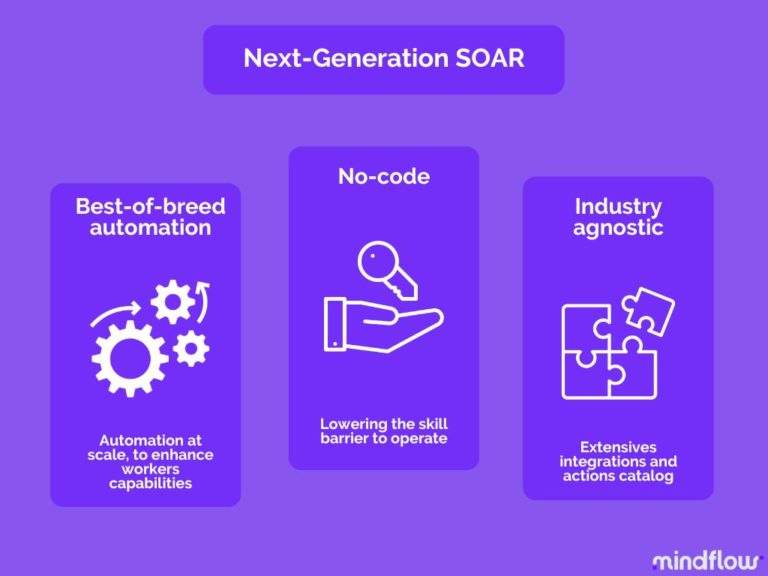
A revolution in usage occurs when the means become accessible to the most. This is what next-gen SOARs are looking to enable.
Cybersecurity challenges: Next-gen SOARs at the forefront of the automation revolution
Regarding automation in cybersecurity, SOARs are the GOATs. They're designed to be the best of breed regarding automation. Automation is at their core.
We've seen that most daily tasks analysts must perform are pure and straightforward repetitions (always bear in mind the Modern Times comparison). Processes are known by heart but are still performed manually.
Even though some employees can master and accomplish them at maximum speed, they're tedious and cause alert fatigue, which is the initial input of the cybersecurity positive feedback loop.
The solution is automation. This is actually what happens when processes are mastered. Automation is as old as work itself. It's a circle of continuous improvement, from the initial learning of the methods to their mastering, leading to their automation. The keys are the benefits generated at each step. The initial learning brings benefits that are soon increased thanks to improving (mastering) the processes.
To achieve even more significant benefits, you want better speed, fewer inconsistencies, and less waste = Optimization. You're looking to automate these tasks. Look at the automotive industry as it enters the automation revolution. Tesla - Giga Press (made by an Italian company) is a true revolution in the car-making processes, accelerating car-making at an unprecedented pace. German car companies have been harnessing automation for a while now, but they're also looking to ramp up automation because of its promised gains.
Cybersecurity needs to enter this revolution as well, at maximum speed. There's no other viable option. Hire thousands of analysts? Good luck.
Basic tasks are repeated alarmingly. Automation removes workflows or steps that are repetitive, redundant, or can be performed without active human monitoring. Applications are multiple exponentials.
Still, reports from the SANS Institute, Gartner, Forrester, or ISC2 show that people are waiting for actual automation capacities. Existing products have not helped to solve the issue.
Only Next-gen SOARs are addressing this issue. Bringing no-code and process-agnostic platforms is the only way to make automation accessible.
SOAR means automation engine. No code means accessibility. Process-agnostic means hyperautomation potential—both mean automation at every level, addressing most organizational processes. Products like Mindflow are part of this new cybersecurity approach, and SOARs are the central pillar of a renewed architecture, promoting automation at every level of your organization.