Jun 10, 2022
Paul-Arthur
Jonville
"The future of SecOps part 3 – Security Automation" is part of a three articles series published by Mindflow to have a catch of what comes next in the cybersecurity world.
Today, human time isn't fast enough to face the rising threats that security operations endure daily. The rhythm and variety of attacks are growing. A Security Operations Center (SOC) may meet hundreds if not thousands of alerts daily. To stay up to the task of determining which one of these alerts are actual attacks, the speed of defenders and their processes need to increase.
As such, the SOC manager must look at how it can optimizes its processes. We're bringing security automation as the answer.
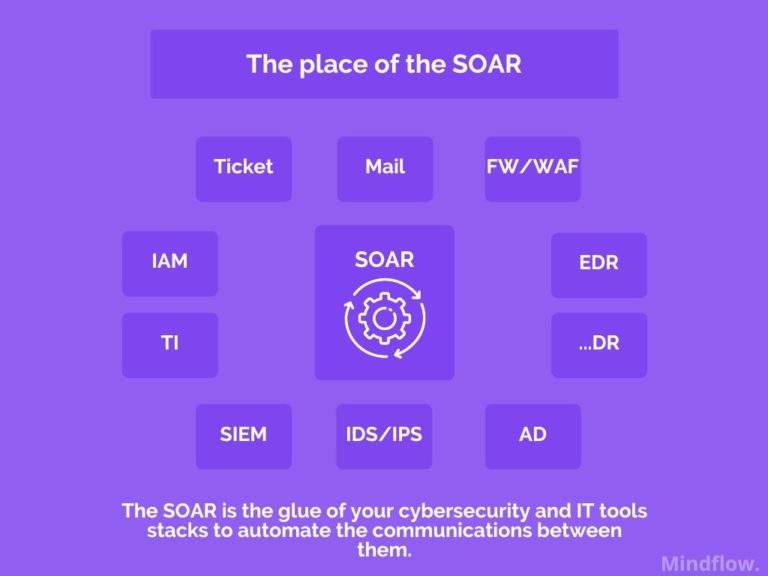
Automation products, such as Security Orchestration, Automation, and Response (SOAR), allow Security operations to meet that objective by providing a platform where they can design and store their security automation workflows. As such, a SOAR is enhancing the speed by allowing anticipation and consistency in enabling the sustainability of security automation.
With its help, the SOC would run faster and with fewer mistakes, thus :
Exponentially reducing the time to detect incidents
Exponentially reducing the time to repair these incidents; and,
Freeing time for more complex tasks
Also, Orchestration and automation help with multiple other purposes. Thanks to its orchestration logic, SOAR is, by design, the most suitable tool to assist in audit and compliance on a macro-level, i.e., for the Chief Information Security Officer (CISO).
Security Automation exponentially reduces the time to detect incidents
The Mean Time to Detect (MTTD) illustrates the average time needed to detect a threat that breached your company's system.
Today, the most valuable asset in most enterprises is the data it stores. Its amount or its sensitivity is growing at an unprecedented pace. You could imagine that an attacker finding his way into your information system can easily steal or compromise these crucial resources. The longer he stays in, the more dangerous it gets. You could think that detection comes in a relatively short time. On average, it takes more than 200 days to detect the incident, even in 2022.
Obvious TLDR: the sooner the issue is detected, the sooner you can fix it, and the better your company will be.
When assessing the time to detect, two main factors keep MTTD too high in your organization:
Suitable tools (up to date, properly managed); and
Speed of action
Harnessing security automation is an answer to these factors.
Automating the alert management from your sensor and log tools helps collect, compile, and tag logs from all the tools and devices across the different sources of your organization.
Your SIEM, network sensors, or EDR platforms are the first telemetry ingestor. They generate massive flows of alerts, and analysts must go through every one of them to determine which one needs further investigation. These processes aren't challenging per se, but they require manual tasks, such as checking for artifacts to decipher Indicators of Compromission and then trigger remediation action.
Automating the transition between initial alerts to enrichment and contextualization is the first step for security automation. These tasks represent the bulk of what N1 analysts must perform daily. They're dramatically repetitive - like copying/pasting artifacts to check if they are malicious or not. Plus, the processes are known. Analysts know the path to perform their tasks. It's like in the industry, endless lines of workers repeating the same processes all day long... talking about alienation!
You have all the tools needed; you know every step you must perform, and there's no cognitive material to add. You're in the typical case that is crying for automation.
Enabling security automation is finding a way to free your analysts from this burden, leaving them for the role of overseeing processes and the decision to initiate remediation.
However, current security automation tools aren't adequately addressing this issue. They're taking the issue by the wrong end in being addressed to small groups of people inside SOCs. They're designed for experts who have heavy dev competencies in a field where half of the professionals don't have pursued a course in computer science or designate themselves as coders.
Thus, automation relies on a happy few, able to master the tools. Should they leave, you'll end up with debt, unable to pursue the processes they created. One adaptation here, one repairing there, and you're most likely done as to maintaining it; the rest is praying for it not to break. At one point, you'll be forced to start from scratch with new processes because formers became outdated (new tools or updates).
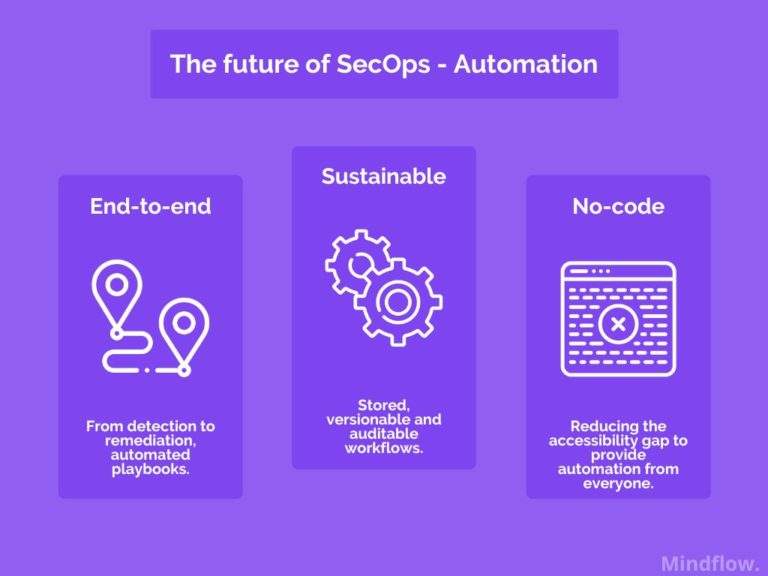
This is where no-code comes as an automation enabler in reducing the skill barrier needed to operate an automation engine and the technical debt accumulated with legacy ad hoc automation.
Security automation delivers value up to remediation tasks
You can define the Mean Time to Remediate (MTTR) as the time needed to close a defined incident. Automating the detection and confirmation of true positive incidents is only the first step when talking about security automation.
You'll save a lot of time by creating automated workflows for your basic triage and enrichment tasks, but you can go further.
When you're dealing with a known threat, you know its effects and how to counter them. An unknown IP deemed malicious trying to access your network shall be discovered. The next step is to add this IP to your web application firewall exclusion rules. In short, we're talking about incident management process. You already know end-to-end processes to perform to keep your network security in the face of such threats.
The analyst in charge is following the incident response playbook. However, still, even with a well-established incident management process, they must complete multiple tasks such as finding targeted device credentials, navigating networking hoops to connect to the afflicted device, looking up the commands to run, and then copying and pasting them into the incident to repair finally.
This is a lot of work to answer one incident, and it is prone to create even more delays, such as waiting for another analyst to perform one of the tasks described above or errors that can invite themselves at every step.
Recoup with the number of incidents your company encounters every day, and you're confronted with a massive amount of incidents to investigate and repair which leaves little to no time for analysts to do something else. In the end up, they're always coping with the inflows of alerts, sometimes they're not even able to deal with all of the alerts at the end of the day, leaving potential breaches ongoing for days... Ultimately, it leads us to the cruel and well-known statistic of breaches going undetected on average for a little more than 200 days.
Automation drastically reduces the time required for a human to perform tasks serially, enabling them to manage the inflows. They're able to create predetermined playbooks that will handle knon scenarios of incidents autonomously, leaving to the humans in charge final decisions or reports.
With automation, incidents gathering and diagnostic are combined with machine running processes executed as soon as the incident is detected and confirmed, thus reducing MTTR.
Security automation to enable humans to focus on more complex tasks
Security automation doesn't only provide the benefits of increasing the speed of detection and remediation and the consistency of your incident response actions and thus do more in less time.
When talking about doing more, there are more security automation benefits than we've already discussed. Automation also helps enable your analysts such as the focus on root cause analysis of the closed incident. At some point, you can't only rely on putting out fires. You have to find ways to prevent them. This goes by understanding the underlying cause of an incident.
To that end, analysts must pinpoint all the factors contributing to an incident. However, in the present state, analysts don't have time to take a step back and analyze the whole process of an incident: what happened, how it happened, and why?
Benefits are noticeable thanks to the ability to define the problem precisely. By identifying the root cause(s), you're reducing the number of future errors that could have occurred from the same root causes. Also, defining the cause helps develop the ability to implement tools and solutions to these.
As a whole, it helps improve your company's security, besides the obvious benefit of making your processes run whenever one wishes, or an event triggers it, without any need for urgent actions.
Also, automation of detection and remediation helps to free valuable time to focus on advanced tasks, such as threat hunting, where your analysts search your network for unknown threats. Whatsmore is that we've already covered what benefits security automation can bring to Threat hunting, like automating the querying in threat intelligence database or further investigation.








