Mar 16, 2022
Paul-Arthur
Jonville
Threat management usually occurs after an incident has occurred. You start investigation processes after the alarm has been rung.
However, more advanced threats can surpass your defenses without ringing the bell. To counter this, analysts need a complementary approach. They gather threat-hunting tools and processes to perform proactive searches within your networks and detect and neutralize these more advanced threats before they cause damage.
Thus, they need to dedicate specific resources, such as threat hunting tools and time, to deciphering deep malicious behavior and creating specialized reports that aim to understand the attack in depth and identify its root cause.
With the rise of more advanced threats, Threat Hunting is more critical than ever in your company. However, it is too often put on the side because of various factors, making your company vulnerable to the most dangerous threats.
Coming up:
What are the challenges hindering Threat Hunting in your company
How the SOAR can help orchestrate your Threat Hunting tools and processes
A recap on the value brought by the SOAR
Threat hunting challenges
Looking at the global data concerning security breaches, we'll find interesting facts about the need (or lack) for Threat Hunting. In 2021, the average length of a breach going undetected was 212 days, up from 200 days a year earlier. Combined with the fact that breaches are costing companies more money, attacks are growing sneakier and deadlier.
Also, it means that they have evaded your defenses. From that point, either you're waiting for the breaches to materialize, or you will hunt them down proactively. In other words, if you consider the kill chain, Threat Hunting helps you gain visibility where you're traditionally blind, between recon and action.
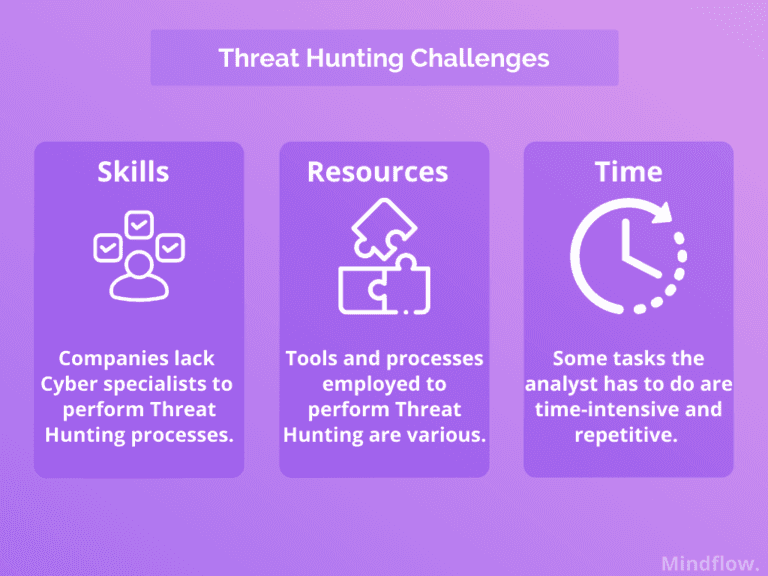
It's easy to say, but hard to do. Implementing and conducting regular Threat Hunting processes presents numerous challenges. We've listed some of them that your company may face today.
First, as we said above, Threat Hunting needs dedicated resources. Yet, resources are scarce. Even though the workforce gap was reduced in 2021 from 3.1 million to 2.4 million workers, there is still a gap to be filled to ensure a proper level of defense in every company.
Also, cyber professionals' salaries are growing rapidly. In 2020, they grew 16.3%, five times more than tech salaries in the US. It's becoming increasingly complex for companies to recruit top talents and thus properly perform advanced tasks, notably managing threat-hunting tools and processes.
Even if a company were to recruit such talent successfully, it would instead dedicate them to value-oriented tasks. Threat-hunting tasks regroup many manual processes that are time-intensive and tedious, thus creating a loss of value for an expensive human resource.
In addition, companies have an increasing number of tools to use. Modern companies have, on average, 40 different tools available in their cybersecurity stack. Threat-hunting tools are thus diverse and create multiple panes of glass for the analysts, which is time-consuming.
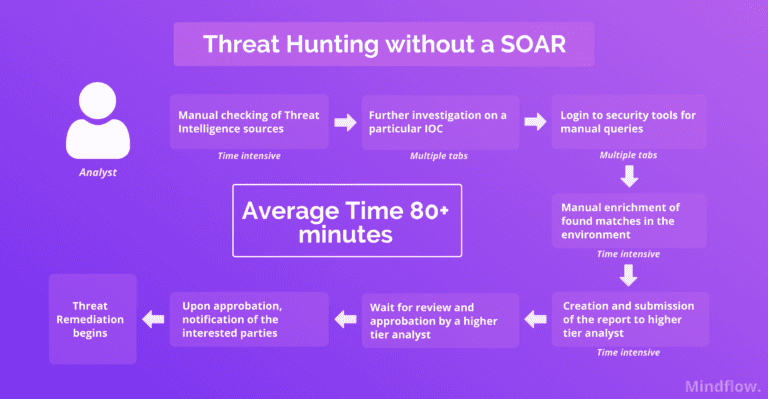
Let's describe the usual processes an analyst follows to proactively search for unknown threats on your network.
The analyst first consults their Threat Intelligence sources, such as RSS feeds and specialized blogs. Then, they manually collect relevant or new information about unknown Tactics, Techniques, and Procedures (TTPs) employed by attackers and Indicators of Compromise (IOCs) of an attack.
At this point, the analyst notices a particular IOC, such as a Hash, indicating an early attack stage. The analyst now has to begin a further investigation to determine the IOC's criticality by performing multiple queries on different threat-hunting tools.
Once they validate the severity of the IOC collected, the analyst logs into your SIEM or EDR to begin the hunt. They must run queries on each to verify the presence of this particular IOC on your systems.
If your analysts are to find matches, they now have to start documenting them to create the incident reports, which include the number of devices infected, file names, and other details.
Finally, the finished report is submitted to a higher-tier analyst for approval. Your analyst waits to notify the concerned parties.
The senior analyst, in turn, starts a deeper analysis of the threat. They try to discover new patterns that evaded your defenses and which tools the attacker used to improve your company's defense against familiar attacks in the future. These tasks are the most challenging yet the most rewarding.
Without leveraging orchestration and automation technologies, your analysts are experiencing multiple stages of pain, especially when navigating between their Threat Hunting tools. This implies a risk of false-positive alerts during the process for rather easy-to-automate tasks.
Fortunately, thanks to its automation and orchestration capabilities, the SOAR can drastically reduce the time and skills needed to perform Threat Hunting.
How can SOAR orchestrate your threat-hunting workflows?
As we said above, many companies have put it to the side due to the variety of challenges associated with using threat-hunting tools. The SOAR makes this accessible. Let's examine how your analysts can leverage a SOAR to ease the threat-hunting process.
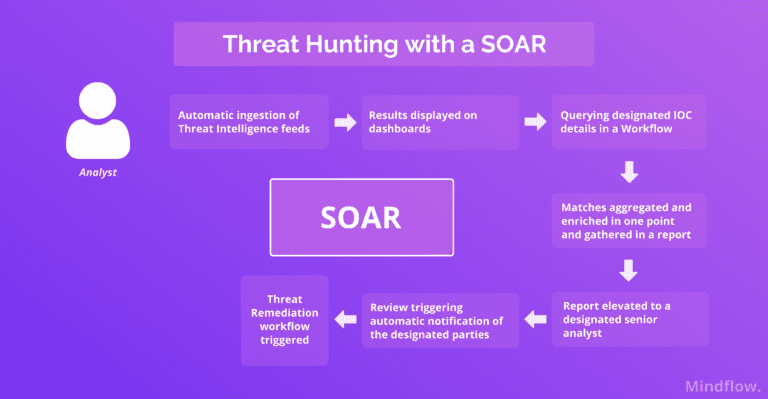
In a previous article, we described how a SOAR ingests Threat Intelligence thanks to automated workflows. When talking about Threat Hunting, these workflows deliver massive value. Once on your SOAR platform, you can check for the results of your automated ingestion of relevant Threat Intelligence data from Threat Intelligence feeds.
Your analyst can check out a particular malicious intel within this data, like the one we've described above. Suppose your TI ingestion workflow hasn't already planned cross-checking steps before multiple TI Feeds. In that case, your analyst can trigger a specific enrichment workflow to gather additional information, such as the criticality of the IOC.
Based on the results of this additional search, the analyst can trigger a threat-hunting workflow across your company's environment. Thanks to APIs integrated by the platform, the workflow starts querying the specific IOC gathered before your security tools, such as your SIEM and EDR. Your analyst doesn't have to jump between your Threat-hunting tools but waits to complete the search.
Once the search has been done, your analyst can generate a report based on the findings, such as the number and criticality of the devices infected, the severity of the threat detected, file names, hashes, etc. Then, he can elevate it to the senior analyst for decision.
As part of a deeper investigation of the threat, the senior analyst can trigger another workflow. He can detonate the discovered file on a sandbox to report its effects, for instance, and check the file history to reverse engineer the attacker's TTPs.
Let's recap the value brought by the SOAR
Automated Threat Intelligence ingestion: SOAR ingests Threat Intelligence data in a centralized data lake for the analyst to leverage. It seamlessly integrates data from various sources, such as external threat intelligence feeds.
Proactive and Automated Threat Hunting Process: Your analyst reduces the time needed to hunt down threats by using SOAR capabilities to search for malicious activity across your network automatically. By triggering workflows, they can find designated IOCs faster and prepare the work for much more complex tasks, such as correlating the IOCs with attackers' previously unknown TTPs.
Build automated workflows to streamline processes from a Single Platform: You can pre-build your incident response procedures from your SOAR platform, like Mindflow, by creating pre-built actions. Your SecOps teams thus acquire complete visibility about the threat-hunting tools and processes activated to perform the hunt.
Using these workflows, your analysts automate the repeatable and time-consuming tasks described above and focus on forensics tasks to discover new TTPs.
Remediate Threats faster: Finally, SOAR can leverage your environment - your EDR platforms or Mail Security tool, for instance - to automate the proper remediation of the discovered threat.