Nov 17, 2022
Hugo
David
Automatically query HaveIBeenPwned to verify that user emails are not listed in a new leak. Then, initiate remediation steps for each finding if there are any compromised emails.
Why? Compromised emails can be devastating if not detected early. A compromised email could lead to impersonation, business email compromise, open the way for an initial entry and to escalation for the attacker.
Through Mindflow, an analyst can automate most of the actions needed, from the monitoring to the remediation phases. It leaves the analyst with the root cause analysis and the lessons learned processes.
Tools orchestrated and automated: 6

Browse.ai

Gmail

Google Admin

HaveIBeenPwned

Slack

Jira
How would you manually check for a compromised email?
Let's assume how you would manually check for potentially compromised emails in your company.
First, you would be forced to check weekly for new leaks released by HaveIBeenPwned manually. Straight away, we can safely say that it's the kind of task you will forget from time to time. It can be resolved by creating some recurring task on your calendar or writing a big red cross every Friday, but there are sexier ways.
Then, whenever a new leak is released, you must look at the details to understand what's at stake. Once fully aware of the leak, it's time to go on your workspace platform. In this example, we took Google Workspace. Let's hop on Google Admin to fetch employees' emails and copy and paste them into the HaveIBeenPwned search engine to see if one of these email addresses hits.
Should a hit occurs, no time to waste. Go to the Google Admin panel and select the corresponding user. Start by signing out devices that look suspicious (or sign out everything if you're unsure). Also, to ensure that there's no unauthorized access to the account, you want to reset the employee's password.
Once these preliminary steps are done, you will send a direct message to the employee on your internal communication channel to notify him of the incident and advise him of the following steps. Also, this message is a good start for a quick interview with the employee to decipher the root cause. It may be just a mistake on their end afterall!
In the meantime, you're going to create a ticket in your ticket management system to keep track of the incident and enrich it based on the findings (user affected, time of discovery, first steps performed).
Once the employee has registered a new password, you can proceed with their interview. The key is to gather intel such as: are you alone, were you alone at the time of the incident, has someone accessed your laptop, or, if you have your email account set up on your smartphone, who has access to it, have you encountered something fishy in the last days (unusual email, gone somewhere, etc.), is the password of the credential pair shared with other accounts (if yes, which accounts?), etc. In the meantime, check on signing and email logs to see if suspicious emails have been sent from the employee's email address.
Once enough intel is gathered, analyze them and decide if the incident is benign (no suspicious activity) or if there has been suspicious activity on the employee's email account.
Even if this use case seems easy to remediate in theory, we see that, in practice, many actions are induced for the analyst in charge. There are quite a few apps and tabs to open to investigate and assess the severity of the incident. Quite a few tools to log in, pages to fetch, and logs to analyze.
Imagine if the leak shows not only one email address but 3, 4, or more. It can rapidly devour the analyst's time and imply repetitive processes. Even though some password managers do such monitoring, there are still the first steps, the remediation process, and the root causes analysis to perform. About all these steps, we see that human cognitive capacity is needed mostly when it's about determining the root cause analysis. Let's reduce human interaction to this only step and automate the rest because remember that, in an analyst's everyday schedule, triage rapidly makes a good chunk of their day.
Objectives? Streamline the incident response plan, ensure every step is correctly performed, and reduce the overall time to detect and remediate.
Let's see how you can manage such a use case through Mindflow with remediation steps included.
How can you check for compromised emails via Mindflow
How is Mindflow achieving this goal? By reaching the selected tools from their APIs, Mindflow allows the analyst to push and pull information to each service to automate most of the process to detect and remediate a compromised email following a leak released on IHaveBeenPwned.
How is the compromised email monitoring and remediation going to work through Mindflow?
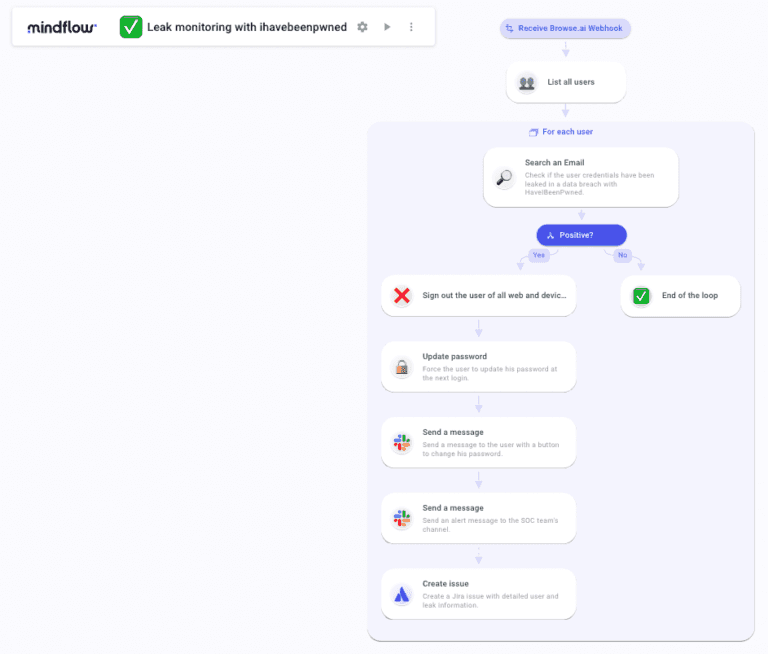
First, we're going to hook on Browse.ai to monitor HaveIBeenPwnd. Each new leak will trigger the Flow. The first call will get users' information on Google Admin. Straight away, you will automatically list all users from your Google Workspace through Google Admin and extract their email addresses using the data transform feature from Mindflow.
Once done, you will submit each email address to HaveIBeenPwned to look for a match. Inside this loop, if there's a match between one of the submitted email addresses and the HaveIBeenPwned database, the first remediation steps will be triggered as follows. You're going to sign out the devices and force a password update. Then, you can pre-determine a message to the user through Slack that will comprise a link to the changing password page. This message can also be the start of the root cause analysis between you and the targeted employee, as described above.
Also, in the same loop, you can automate the sending of a message directly to the SOC team to warn them of the incident in a dedicated channel and, to help them keep track of the incident, create a ticket in the ticketing system, here Jira, and populate it with the findings.
So, what has been automated?
Monitoring? Check
Alerting? Check
Remediation? Check
Incident tracking? Check
What is left? Root cause analysis.
What we could easily add to this Flow would be a further enrichment by fetching email and signin logs from Google Admin to allow the analyst to perform a quick investigation during the employee interview to check on any suspicious email or signin that could have happened since the incident has occured.
Unlike a manually performed incident response plan, what's better is that every step is tracked, every action is notified upon failure, and all are auditable.