Today, we will learn why nocode cybersecurity automation is the only way for security teams around the globe. Let’s first get into the state of affairs.
State of cybersecurity automation today
We are in 2023, and yet, cybersecurity teams around the globe are still massively relying on manual work to perform some of the most repetitive tasks you could imagine. No, we are not only talking about the usual top-notch organizations that have time to answer Gartner of Forrester surveys. We are talking about the other hundreds of thousands in this World.
When it comes to repetition and alienating work, cybersecurity has indeed its fair share of the burden. Take triage, for instance. In other words, it means taking an artifact reported in an alert and trying to assess whether it is an IoC. The analyst will do such by querying internal (information collected from internal sensors, such as the usual IP address, DNS, or MAC address) and external threat intelligence (flagged IP addresses over the Internet) to enrich the alert. Then the analyst would start the identification work to determine the precise nature of the incident (source, extent, risk) of the case or declare it a negative alert.
We are often talking about SOC when it comes to cybersecurity. This time, let’s take an IT/Security team of an SME that works hybrid on a cloud-based working solution (Google Workspace or Microsoft 365), a widespread case.
The number of alerts, for as long as the organization tries to cover the different risks such processes would endure, would already be consequent even when only talking about basic monitoring. Like dozens of daily alerts: unauthorized sharing, an unusual amount of downloads, deletion, logins from unusual places, an unusual number of failed login attempts, password recoveries, or potential phishing through emails. Five events, and we can already decipher the kind of repetitive work the IT/Security team folks will have to perform daily to depart noise from true alerts. And there are lots of noise out there.
From there, we could ask ourselves? Is it a sensor configuration issue? You could reduce the number of false events by refining the configuration further, but that is not counting on the unpredictable human element. Holidays, negligence, urgency, maliciousness. These four elements only will already bring you lots of alerts every day. Refining is not the only solution. Also, too much refining could lead you to miss alerts falling out of your perimeter. It’s better to collect a bit too much to be sure to catch what you are after than too little.
Building processes to handle all these data flows are more important than everything else. No matter your strategy, you will have to face alerts if your organization operates on the Internet and you have humans under your watch.
How can you build a machine that can handle increasing flows? Industrializing the processes. Identifying repetitive processes and leveraging technology to reduce the amount of human work that it needs to be handled.
Why is it not widespread yet? This is what we are going to understand next. What will enable its widespread? Nocode cybersecurity automation.
Challenges facing cybersecurity automation
Cybersecurity automation is easier said than done. Automating security processes involves a myriad of challenges. APIs, languages, environments, and connectors are just the tip of the iceberg. Each tool in your stack likely has its unique API, requiring you to understand and work with various interfaces and protocols. This increases the complexity of automation and the time and resources needed.
Maintaining these integrations is another challenge. APIs constantly evolve, with new versions offering improved functionality and deprecated features. Keeping up with these changes requires continuous monitoring and updating of your connectors, adding to the workload of your already stretched team.
Changing a tool in your stack presents yet another hurdle. Each change requires the development of a new connector, a time-consuming process that can delay the deployment of the new tool. And if the person who coded the connector leaves the company, you’re left with a piece of code that no one else understands, further complicating maintenance and updates.
Even when you’ve got everything set up, there’s the constant fear of someone else messing up your carefully crafted code. And let’s not forget the countless hours spent troubleshooting because of a missing comma or a misread step in the vendor’s documentation.
Then there’s the pressure to prioritize immediate tasks over long-term improvements. Want to develop a workflow to automate the enrichment process? Too bad there are alerts to treat. This short-term focus often leads to missed opportunities for efficiency and improvement.
And finally, there’s the misguided belief that buying a well-known Security Orchestration, Automation, and Response (SOAR) tool will solve all your problems. But these tools often come with their own set of challenges, from complex interfaces involving heavy coding and steep learning curves to limited out-of-the-box integrations. And if they don’t provide an integration for a tool you use? Too bad you’ll have to develop your own connector. What if a new version of your critical monitoring tool is out? Chances are the vendor providing your SOAR is manually crafting connectors, and you will either have to wait weeks before it’s out or develop your own… back to square one.
Yet we wonder why cybersecurity automation is lagging. The answers are just right there.
What nocode cybersecurity automation brings
Call it as you want: nocode SOAR, nocode cybersecurity automation, or anything else, nocode applied to cybersecurity is a gamechanger for the following reasons:
Create workflows faster than writing a runbook
No-code platforms feature intuitive, drag-and-drop interfaces that make it easy to create automation workflows. Pile up the different steps, delegate the automating work to the automation engine, and mind building following your notebook. The key is saving time and effort during the building process, as you don’t have much time to spare. To be precise, a nocode SOAR should allow you to create a workflow in less time than it takes to write your runbook.
Eliminate the connector issue.
As traditional SOARs, nocode SOARs or nocode security automation platforms usually come with pre-built connectors for a wide range of tools. If one doesn’t don’t bother, you’ll end up stuck in the mud. Having pre-built connectors available is a must if you want to get serious about automation. This means you no longer have to worry about developing and maintaining your own connectors. The platform handles all the complexities of integration, allowing you to focus on what matters most – securing your organization. Yes, you are looking for a platform that has industrialized the integration process.
Automate basic processes in days.
With these two features, you are on the path to building an ability to create workflows in minutes (okay, hours at best) and version them just as fast. Onboard and start to build in hours. Deliver your first workflows in days. Identify automation-prone processes in your daily tasks, and let’s get going. Basic alerting workflows will take hours to be deployed and will change your life even before you start getting your hands on remediation workflows.
Mindflow: the nocode cybersecurity automation platform you are looking for
What we have described above is what Mindflow brings to IT/security teams, Security teams, SOCs, and every people working in cybersecurity: speed, consistency, and efficiency.
Drag-and-drop interface and visual canvas editor
Mindflow features a drag-and-drop interface and visual canvas editor making, creating, maintaining, and improving automation workflows easy. Create a workflow, get your runbook at hand, and start building, as simple as that. You can visually map out your processes, making understanding and optimizing your workflows easier.
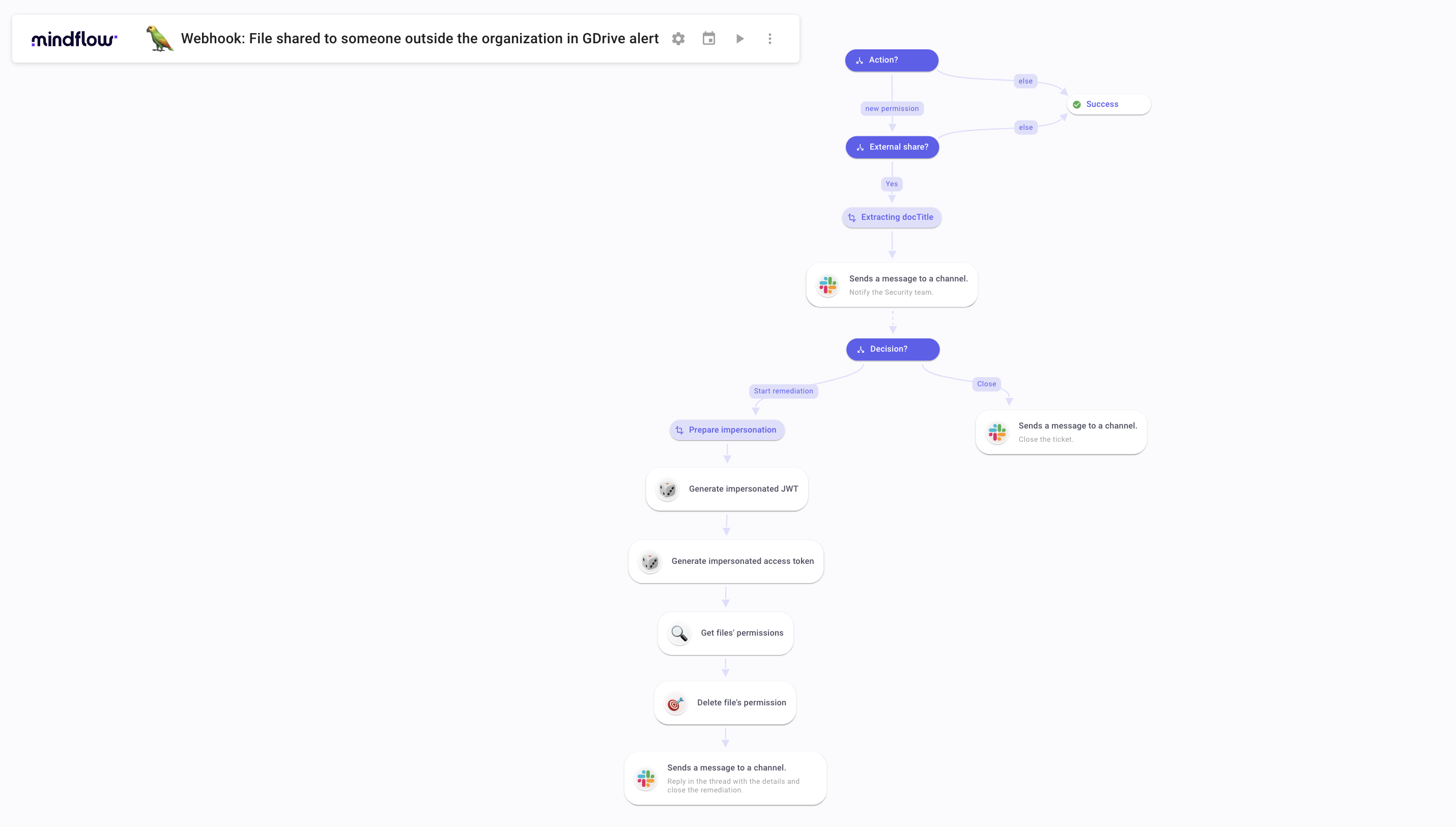
Connectors? We’ve got you covered.
If you are wondering what makes Mindflow stand out from its competitors, you have your answer with its integration capabilities. Its integration capability is automated. This allows the platform to provide way more connectors than any other platform on the market, both in quantity and quality. This time, you don’t have to worry about connectors a single bit. You will have pre-built connectors for your tools as long as they provide APIs. If they don’t? Pre-built HTTP Requests can be crafted as a fallback. Virtually no limits.
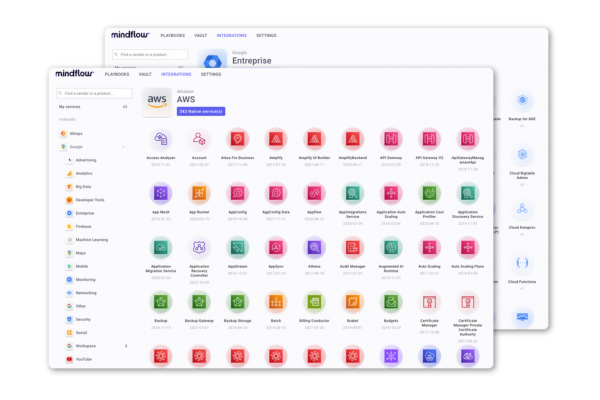
Redefine the way you work through nocode cybersecurity automation.
Real automation capabilities are game-changing. Yesterday when you were spending your time chasing fires here and there to try to put them out, today you will let the machine do it for you as starters. This means less T1 work for the biggest security teams and less work for everyone for other and smaller teams.
But as your processes get structured and automated, you will get ready to proceed further, up to the next parts of the incident response: Isolation and remediation. What stops you from automating these parts? You have all the API endpoints of your tools and an easy-to-use automation engine at your disposal; what are you waiting for?
Isolate the device through your EDR, wipe it through your MDM, push that IP address in your Firewall blocklist, revoke that sharing link, reset this user’s password, etc. A myriad of possibilities to automate incident response from its detection to its remediation.
When we talk about orchestration, it is about—making sense of all your tools from a single place. This is what Mindflow brings through nocode cybersecurity automation.
