Sep 16, 2022
Hugo
David
Today's cybersecurity landscape is filled with challenges. We often go for automation when trying to find solutions to handle them structurally. To most people, automation appeals to speed, which is the first answer people turn to when they need to accomplish more in the same time as before.
There's no debate about the fact that cybersecurity automation is the only concrete answer for this first challenge. However, people often overlook other benefits of automation. You can't take automation as only a speed enhancer. If you were to achieve high, well, you could rush every task and prey for no errors, or you might hire 200 hundred people and make them work day and night 7x24x365... Wait, isn't that illegal?
More seriously, automation isn't and shouldn't be only about bringing speed. Execution speed, without proper controls, can be the source of massive incidents. There's this old saying that goes, "Do it fast or do it well" (at least when I was a child in France...). It's still valid as of today, to some extent.
Indeed, adequately implemented automation can help us reach unprecedented momentum in the digital world. By properly implemented we mean with consistency. There's the notion that we think is paramount regarding cybersecurity automation because it brings various benefits to your organization and processes.
Below, we're going to understand what consistency exactly means; and we'll see that,
Often overlooked, consistency is nevertheless a significant benefit when it comes to cybersecurity automation.
What is consistency?
Let's start from the basics and slowly link this notion to the cybersecurity automation field. Usually, we use the term consistency for people or processes that have the capacity to always behave in the same predicted way and achieve the same level of success in something.
In other words, on unchanged terms, the delivery will always be the same. As such, consistency is conducive to generating multiple benefits. Among them, we can list the main:
Introduce clarity. Consistency generates clarity, or understandability, of the processes because, in order to create consistency, you have to define the processes first to understand every factor coming into play. Beyond clarity of the processes, consistency also brings clarity to the outcomes. If this process is executed as such, then the outcome will be this.
Bring in structuration. Consistency is the antonym of luck or fortuity. Trying to be consistent is working to attain the same results every time. Luck partly or totally relies on external elements to help you attain the same result. Consistency forces you to structure your processes to leave as little holes as possible. Working towards this goal leaves no place for external factors.
In other words, you can't achieve consistency without the dedication and an action plan, which means structuration.
Instigate self-confidence. As a direct consequence of clarity and structuration, consistency also brings self-confidence. You know what your processes are, how they work, and what you can expect from them in determined circumstances. It helps you build confidence in your abilities and qualities, no matter the number of iterations.
Inspire trust. Self-confidence ultimately leads to trust. More precisely, trust from your third parties, customers, or vendors. Having consistent and thus documented processes also help them assess how you will react in a said environment. It shows them that you're serious about what you're doing; no prey and spray or behaving erratically.
In today's world, cyberspace equals interconnectivity and interdependencies. One weak link in the chain and the whole chain can break. We've seen this several times in recent years. The most known example is Solar Winds. A breach that implied gigantic consequences across the whole chain.
Once the trust link is broken, especially in cybersecurity, it takes an incredible amount of time to build it back. You thus need to maintain that link, which goes by looking to develop consistency.
To sum up, consistency makes you trustworthy.
Give place for improvement. Finally, working towards implementing consistency in your processes, because it gives you clarity, structuration, and self-confidence, gives your room to improve. When consistent, you can see how processes are being performed, and outcomes are reached. From then on, it's easier to gather feedback and, ultimately, spot the areas that could use some improvement for an overall more efficient process or potential weaknesses that could hamper them and the like.
To put it in another way, consistency gives time for incremental improvement.
To wrap this part. From what we've learned above, consistency brings many different benefits. Overall, it helps you get better at doing what you're doing and makes you understand why it is like so. As such, we can easily acknowledge why consistency is, to tell the truth, needed everywhere, in any process across the enterprise.
However, in cybersecurity, potential impacts of unknowns can be devastating. There's no place for inconsistent behavior of unsteady processes. Consequences can be high and may be too high for the average company. To be honest, consistency is a top priority in cybersecurity. We're going to see how cybersecurity automation, besides speed, brings consistency.
Why and which cybersecurity automation?
The increasing digitalization of the modern enterprise, besides its immense benefits on productivity, dramatically expands the attack surface. To counter this symptom of digitalization, security tends to "shift left" to stretch over the whole enterprise.
But, this extension implies the multiplication of processes to ensure that all the controls and the monitoring, detection, identification, containment, and mitigation processes are adequately made. Facing that many processes and tasks are near impossible for even the most skilled team.
You can't rush these tasks. As said above, the consequences could be dramatic. You neither can't rely on hiring enough people, even though if you would establish consistent processes. Cybersecurity automation is the only realistic way to attain consistency. Doing it in an old-fashioned way, via manual tasks or ad hoc cybersecurity automation, risks leaving loopholes, creating friction, and in the end, creating technical debt.
Even though these aforementioned approaches bring you either speed or expand your working bandwidth, you cannot reach consistency through these. Since they rely on human execution, manual tasks are naturally prone to errors or omissions. Even more, as the pressure rises due to the sheer number of alerts to handle, it upsurges the said risks. In the end, it creates inconsistent behavior that impacts your outcomes.
As for ad hoc cybersecurity automation, which, per se, is designable by only a handful of people, their maintainability is conditioned to their staying in the company. Once they're gone, such automation is becoming increasingly complex to understand.
Moreover, processes in cybersecurity are counted by hundreds. Each of them can, if done inconsistently, imply dramatic consequences. The kill-chain is vast and sometimes comprises dozens of different actions before the payload delivery. One incident detected can lead to an occurring cyberattack or maybe the only clue that could lead to such an attack. An inconsistent process can sometimes overlook some of these clues. Only cybersecurity automation can introduce this needed consistency.
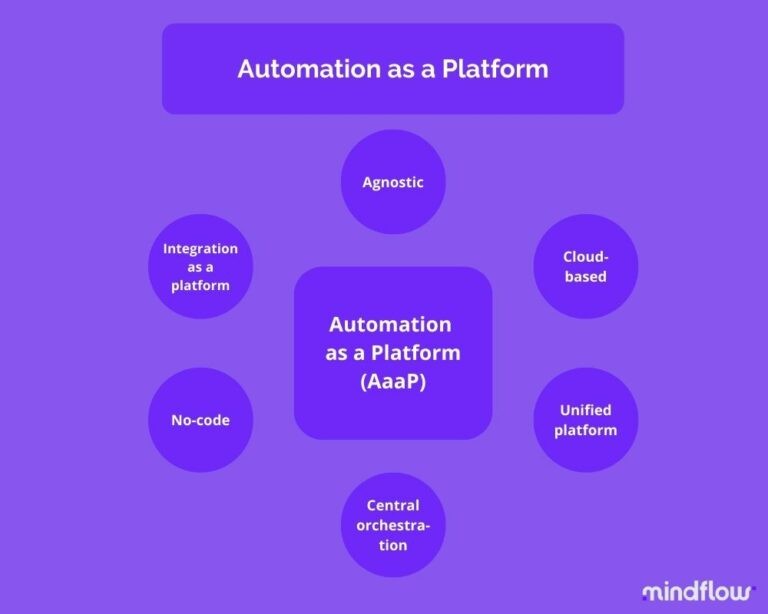
Due to this wide variety of tools and processes, you need a platform to centralize the cybersecurity automation processes; an Automation as a Platform (AaaP, how original) where you can orchestrate these processes. This platform should focus on delivering best-of-breed cybersecurity automation and beyond and find a way to make it accessible and understandable to generate consistency and its benefits. To handle processing capabilities needed, this platform has to be cloud-based. This way, it can scale as you need.
Consistency through cybersecurity automation, what value does it bring?
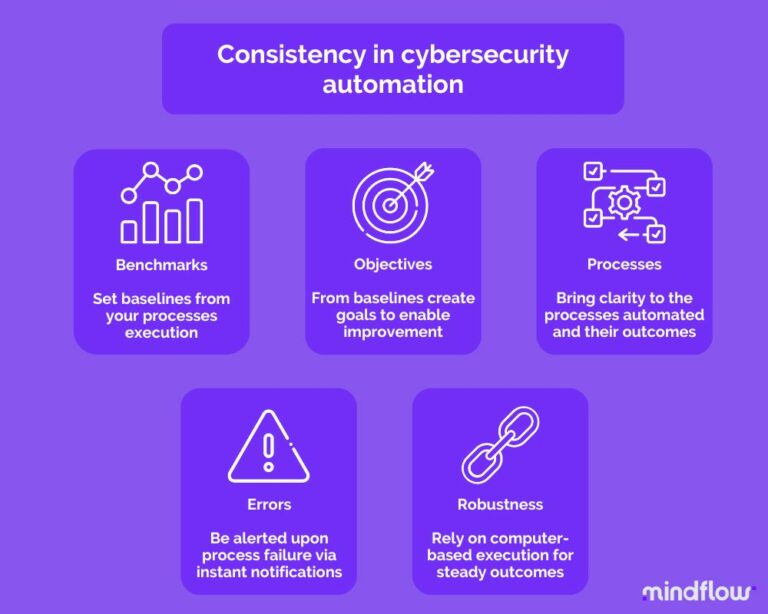
Cybersecurity automation through an automation and orchestration platform ultimately delivers consistency that materializes in the following effects:
Enable benchmarks. Consistency, because it brings structuration of your processes, helps build benchmarks. Benchmarking is more challenging when processes are done inconsistently, as you don't have a clear view of them and their outcomes. By bringing clarity and structuration, you can measure and track performance.
Define objectives. Related to benchmarks, once they're designed, you can determine objectives to reach from there. Identifying and working towards achieving goals necessitate thinking and planning future actions needed to attain them—a clear plan of action.
Refining processes. With automated processes in place, you can identify improvement ways and enhance each process set up. With clarity and accessibility, you can make slight adjustments and experiment with the outcomes. In other words, automation welcomes versioning and rollbacks, which are far more complex when doing things manually or via ad hoc cybersecurity automation.
Identifying and eliminating errors. Even though cybersecurity automation inherently reduces errors thanks to computer streamlining capabilities, no process is perfect. Sometimes, automation can break or lead to errors. On automation and orchestration platforms like Mindflow, you can audit every action performed to identify where a process broke. Even more, automation platforms can generate alerts upon failure, which help the users be more reactive and ultimately limit vulnerabilities linked with such shortcomings.
Finally, consistency facilitates the deciphering of errors. Because automation leads to the same outcome, errors, should they arise, are also consistent, thus making it easier to identify where they're coming from.
Improving robustness. Not only does a process need to be consistent, but it also needs to be accurate. Even though the most skilled and sharp analyst could perform a process a hundred times fairly consistently, one error can lead to sizeable consequences. On top of that, many processes are repetitive but require precision in their execution. Human execution inevitably fails. This is one of the reasons automation was welcomed in the automotive industry. Consistency at a large scale can only be achieved through automation. No matter the number of executions, you will have the same outcome.
This ultimately leads to increased readiness. The process has been designed, implemented, and automated. It thus runs, and you know it; you can rely on it. Through this, thanks to cybersecurity automation, you're designing processes that are consistent with preparing for the worst to face it.