Dec 23, 2022
Hugo
David
Today, we're going to have a little chat about enrichment automation. Enrichment refers to the process of gathering additional information about a security incident to confirm it, understand it better and respond more effectively through its scope, impact, and root cause.
Enrichment involves collecting data from various sources, typically external and internal. The internal includes logs, network traffic, identity information (name, IP, MAC, etc.), etc. External enrichment involves using communautary or proprietary databases collecting vulnerabilities, attackers' tactics, techniques, and procedures (TTPs) or malicious indicators of compromise (IOCs).
Collecting this data helps to identify patterns, trends, and other clues that can help to shed light on the incident, as said above.
We'll see that it is thus essential to determine the appropriate steps to take to contain and recover from the incident and prevent future incidents from occurring.
But, as important as it gets, enrichment can be a long and tedious process with the potential to be extremely repetitive. This leads companies to look for ways to reduce the time needed and the repetition induced. The main answer lies in automation platforms.
The incident response process
As said above, the enrichment process is part of the incident response broader framework that refers to the process of identifying, assessing, and responding to a security breach or cyber attack. This series of steps are taken by a company to minimize the potential impact of a security incident and to prevent future incidents from occurring.
Frameworks vary, but you can outline four main steps. The first one is to identify the incident. This involves monitoring systems and networks for unusual activity or suspicious behavior, as well as reviewing logs and other data sources to determine the scope and nature of the incident. Once the incident has been identified, it is assessed to determine the extent of the damage and the potential impact on the organization.
Following this, a plan is developed to contain the incident and prevent it from spreading further such as disconnecting affected systems from the network. The final step in incident response is to recover from the incident and restore normal operations. This may involve repairing any damage that has been done, cleaning up any malware or other malicious code, and implementing new security measures to prevent future incidents from occurring.
The place of enrichment inside the incident response process
Enrichment is an important part of the incident response process because it helps organizations to better understand the nature and scope of a security incident. By gathering and analyzing additional information about the incident, you can more accurately assess the potential impact of the incident and determine the appropriate steps to take to contain and recover from it.
Enrichment can also help organizations identify the root cause of a security incident and take steps to prevent similar incidents from occurring in the future. By analyzing data from various sources and identifying patterns and trends, organizations can gain insights into the TTPs used by attackers and develop strategies to defend against them. This can include implementing new security controls, strengthening existing controls, and training employees on how to recognize and respond to potential threats.
Considering this, enrichment is an essential part of the incident response process because it helps organizations to confirm or refute an incident, identify its full extent, assess the potential impact, and take the appropriate steps to contain, recover from, and prevent future incidents.
That can take time and be repetitive
Per se, enrichment isn't an arduous process it mostly resides in fetching information in some places. Still, you have to perform it. Without it, you better be discarding every alert and praying. Most of the time, you have answers in your information system that you need to fetch. Thus, the process can take an extensive amount of time and can be multiplied in the hundreds or even the thousands, considering the company.
Enriching alerts can take an extensive amount of time
The length of the enrichment process can vary depending on various factors. First, the specific incident, and its intrinsic complexity. Second, the tools and resources available to the incident responders. These two factors are combining and impact the enrichment length. In some cases, enrichment may be relatively quick and straightforward, involving a simple lookup of an IP address or domain name in a threat intelligence database. In other cases, enrichment may be more complex and time-consuming, requiring the use of multiple tools and sources of information to gather all of the relevant data. Additionally, the time it takes to perform enrichment may be impacted by factors such as network latency and the availability of relevant data.
Having said this and knowing how many tools a company can run as its security stack, there is a link between the length of the enrichment process and the number of tools used to perform enrichment. Using more tools and sources of information is keen to provide a more complete picture of a potential threat that is helping analysts to assess the scope and impact and better remediate it correctly. Still, using many tools also takes more time to gather and analyze all of the relevant data collected since the person in charge will have a more extensive library of potential external and internal touchpoints.
The more alerts there are, the more repetitive enrichment gets
Enrichment can rapidly take a disproportionate amount of time when the number of alerts is large. This can be a significant challenge for organizations that are facing a high volume of alerts, as they may not have the resources or bandwidth to review and analyze each alert in a timely manner adequately.
One of the main reasons that enrichment can take a disproportionate amount of time in such case is that it often involves reviewing large amounts of data from various sources. This can be a time-consuming process, especially if the organization does not have the appropriate tools or resources to collect and analyze the data efficiently or if the data is splattered across different tools. Additionally, the process of identifying and analyzing patterns, trends, and other clues that can help to shed light on the incident can also be time-consuming.
Having processes and tools in place to efficiently review and triage alerts, and to prioritize their response based on the potential impact of the threat is sometimes not sufficient, as the number of alerts is too important and generates lots of noise.
Indeed, incidents can be false positives or duplicates. False positives can occur for various reasons, such as when a security system is configured to be too sensitive and generates an alert for normal or benign activity, or when a security system is not properly configured and generates an alert for a known, benign event. Duplicate alerts, on the other hand, are alerts that are generated multiple times for the same event or threat. This can occur when a security system generates multiple alerts for the same event or when multiple security systems detect the same event and generate separate alerts.
These two can be significant challenges for organizations, as they can generate a large volume of alerts that must be reviewed and triaged and thus be time-consuming and resource-intensive, and can distract from more serious threats.
Enrichment automation: Make enrichment faster and more consistent
The need to reduce the time spent on enrichment
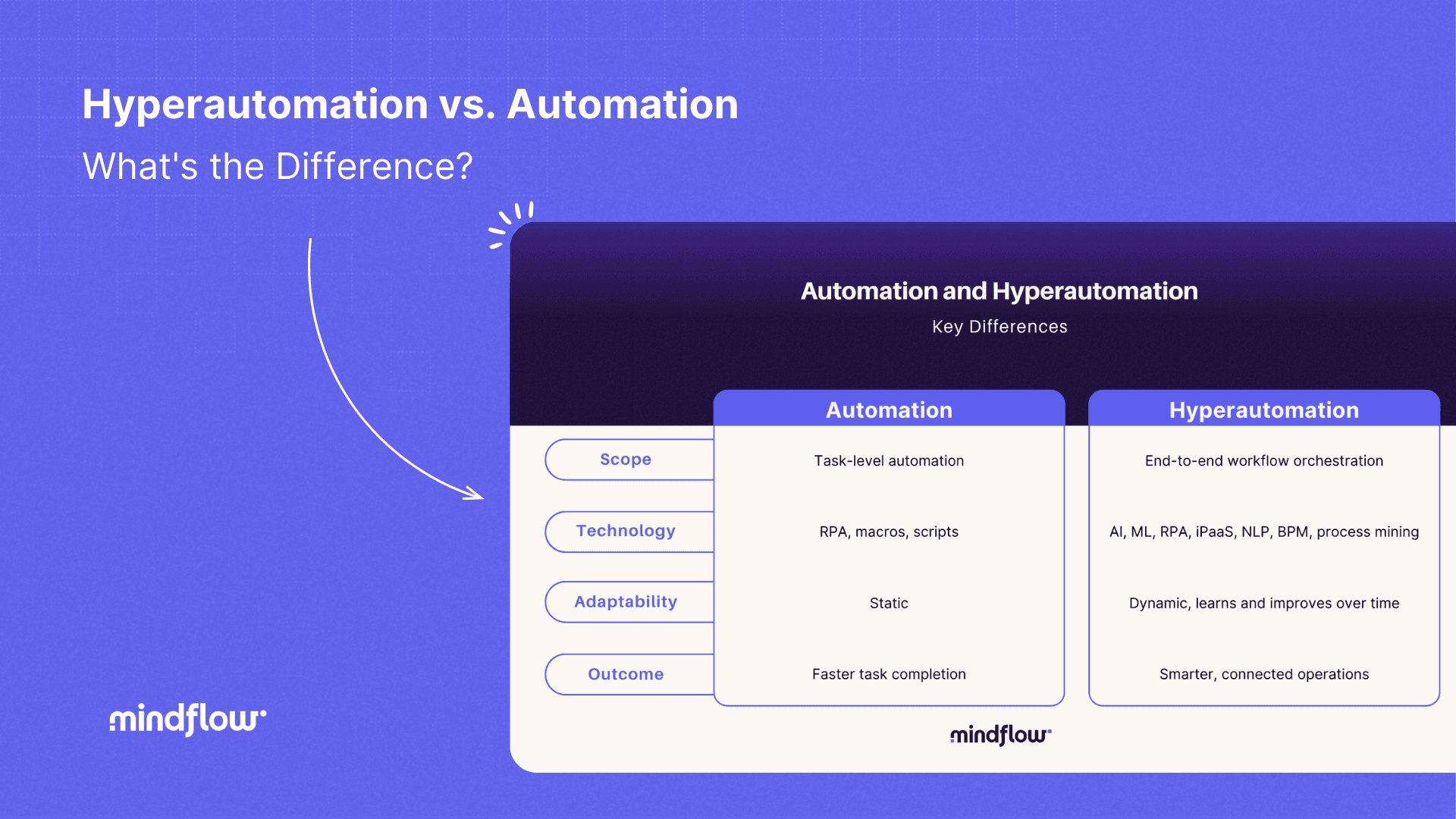
One way to reduce the time and resources required for enrichment in the incident response process is to automate certain parts of the process. Automation can help organizations to more efficiently collect, analyze, and act on data related to security incidents, which can reduce the time and resources required to respond to them.
Organizations can use automation tools to monitor systems and networks for unusual activity or suspicious behaviour, and to alert staff when an incident is detected. These tools can also be used to collect and analyze data from external and internal sources before the touch points, such as logs, network traffic, threat intelligence databases and other sources of information, to identify the unusual behavior, confirm the incident (and depart false positives and duplicates), lists the IOCs, and report to the user.
Additionally, automation tools can be used to take quarantine and remediation actions based on the data collected, such as blocking suspicious traffic or disconnecting affected systems from the network.
Overall, automation can be a valuable tool for reducing the time and resources required for enrichment in the incident response process and can help organizations to more effectively respond to security incidents and prevent future incidents from occurring.
Reduce human errors through enrichment automation
Besides reducing the time needed to perform the process, enrichment automation can help to reduce the potential for human error in the enrichment process by automating certain tasks and providing a more efficient and consistent approach to data gathering and analysis.
For example, an incident responder may use an automated tool to quickly and accurately look up IP addresses or domain names in a threat intelligence database, rather than manually searching for this information. Automated tools can also be used to monitor networks and systems for potential threats, providing real-time alerts and allowing users to assess and respond to potential security incidents quickly. By using automated tools, users can reduce the time and effort required for enrichment, and can also minimize the potential for human error as we already demonstrated here.