Jan 18, 2023
Hugo
David
Domain analysis is the process of analyzing a URL's domain name and top-level domain (TLD). URLs are one of the most common things an employee encounters daily. This is why it's also one of the most common attack vectors, hence the need for domain analysis tools.
Thus, cybersecurity professionals are used to spending time every day analyzing particular URLs through domain analysis. Repetitive, this process can include many different queries before different tools.
To fasten this, security teams tended to build chatbots to automate parts of the process. This is a process called ChatOps, where the chat client serves as the primary communication channel about ongoing work and ticket tracking.
Below we'll see how ChatOps can be implemented through Teams and how Mindflow can help set up a ChatOps strategy and automate domain analysis and thus orchestrate 3 tools.
Domain analysis process
From a cybersecurity analyst's point of view, the steps of domain analysis can include the following:
Identifying the domain name and top-level domain (TLD) of a website: This step involves identifying the domain name and TLD of a website and any subdomains that may be associated with the website.
Gathering information about domain registration: This step involves using whois lookup tools to collect information about the registrant of the domain, such as the name, address, and contact information of the organization or individual who registered the domain.
Analyzing the domain's DNS records: This step involves analyzing the domain name system (DNS) records associated with a website, such as the IP address and name servers associated with the website. This can help identify any potential malicious activity related to the website, such as redirection to a different website or using a content delivery network (CDN) to hide the true origin of the website.
Assessing the website's SSL certificate: This step involves analyzing the website's SSL certificate to determine if it is valid and issued by a trusted certificate authority (CA) or is self-signed.
Checking the website's reputation: This step involves checking the website's reputation with online security tools and databases, such as the Google Safe Browsing list and Norton Safe Web, to determine if the website has been identified as malicious or potentially dangerous.
Monitoring network traffic: This step involves monitoring network traffic to detect any suspicious activity associated with the website, such as traffic to known command and control servers or the exfiltration of sensitive data.
Investigating any identified threats: This step involves investigating potential threats identified during the domain analysis process and taking appropriate action to mitigate those threats.
It's worth noting that these steps might not be done in a strict order, and sometimes, some steps might be skipped depending on the goal and the specific context of the analysis.
Automate domain analysis tools through chatbots in Teams, the classic way
Domain analysis tools are precious resources that SecOps use extensively. However, even though they're efficient, there's a demand to be faster. There's thus the need to automate the use of domain analysis tools through chatbots.
To create a bot on Microsoft Teams that can listen for custom commands, process the command, and push the information to domain analysis tools like VirusTotal and URLScan, you'll have to use the Microsoft Bot Framework and the Teams API. Here's an overview of the process:
Register your bot on the Microsoft Bot Framework portal, which will give you a bot ID, a Microsoft App ID, and a password.
Use the Microsoft Bot Framework SDK to develop your bot's functionality. You can write the code using Node.js, C#, or Python.
Create a command in your bot code that listens for specific keywords or phrases. When a user types a command, the bot will respond by processing the command and sending a request to the desired domain analysis tools with the correct API keys to access the services.
Thus, you need to add to the code the API keys to authorize the requests to VirusTotal and URLScan.
Create a webhook in your bot code that listens for incoming requests from external services. When a webhook is triggered, the bot can process the response and send it back to the team.
Create a Teams app manifest and include the bot ID in it.
Create a package for your Teams appx, upload it to the Microsoft Teams app store, or sideload it in your tenant.
Once your bot is installed in a team, members can interact with it by mentioning it in a conversation, adding it to a channel, or using the custom command you've created.
To perform this process, you thus have to master different environments, which are Microsoft Bot Framework, the Teams API, and the programming language you use for the bot development. Don't forget the API of the external services you are trying to integrate.
That's quite a lot to do, especially programming-wise! Let's see how you can do it through Mindflow without code.
Orchestrate and Automate domain analysis tools and Teams through Mindflow
Mindflow will be the interface between your Bot and the external domain analysis tools, acting as the handler of requests and answers through a no-code interface.
Let's start with a broad overview of the initial setup of the Teams Bot:
Set up the Bot through App Studio, downloaded from the Teams Store.
Save the credentials generated to register them in Mindflow's Vault.
Set the endpoint with the webhook you can C/C in the Settings on Mindflow Flow editor panel (on the top left).
Set the specific command, like /analyzeURL, /analyzedomain, or anything you want.
Create an ad hoc Flow to configure an HTTP Request to get the Bearer token.
Register the Bearer token in the Vault to enable the call back as the Bot.
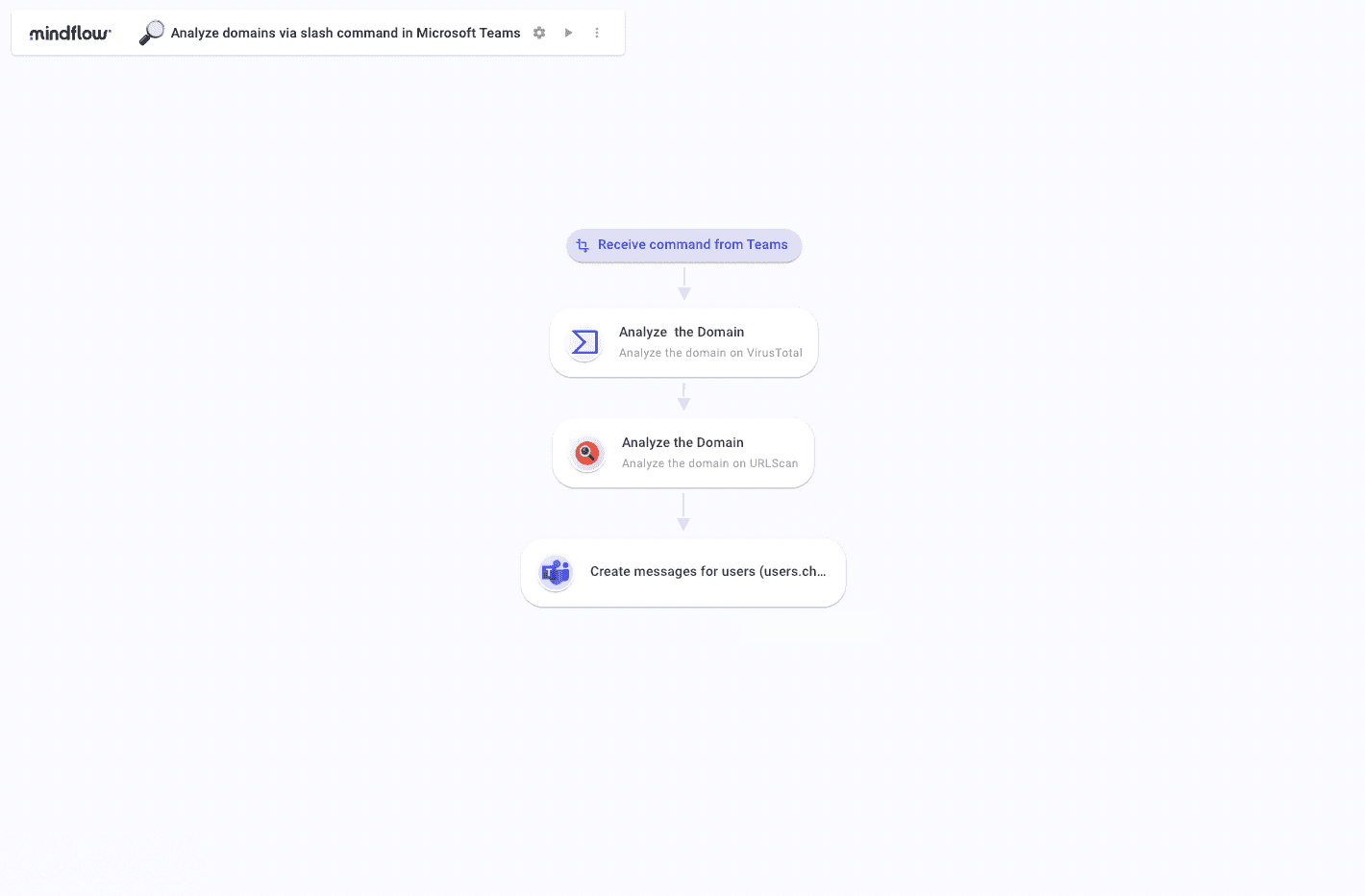
You're set to design your Flow:
Queried commands will trigger your Flow.
First tests to check the trigger will allow you to introspect the request and pick the URL queried.
Extract this URL and push it to the desired domain analysis tools: VirusTotal and URLScan.
As the last step, invoke Teams to send back the analysis results to the user who queried the URL.
Upon testing for execution, you can introspect answers to requests from VirusTotal and URLScan, extract the desired data and push it to Teams.
Find below how this Flow would look on Mindflow.