Sep 1, 2023
Aditya
Gaur
We live in a world more digital and connected (and exposed) than ever before. Every text, transaction, image, video, or audio you transmit over the internet is vulnerable to adversaries — attackers, hackers, and the like — for malicious purposes you would have never thought of. Plenty of solutions and frameworks are helping individuals and organizations find a way to secure themselves best against these adversaries. In this article, we'll dive deeper into why organizations often struggle with cybersecurity despite having access to all the necessary tools and resources.
Social media and other large public platforms have never made a more significant push to brand themselves as secure than in the last few years of this decade. All Apple talks about is how secure their iPhone and iMessage are compared to their Android counterparts. All Meta talks about is how encrypted your Whatsapp, Instagram, and Facebook conversations and information are.
While it may seem like marketing rhetoric, Apple and Meta genuinely prioritize the security of their platforms, both tech giants have positioned themselves at the forefront of internet safety for their users. Cybersecurity has never been more pivotal, especially for companies overseeing billions of users and trillions of data points. Per research published by StockApps, Apple, and Meta —despite all the media coverage— they are the least intrusive with user data, harvesting fewer data points than many of their counterparts, such as Google, Twitter, and TikTok.
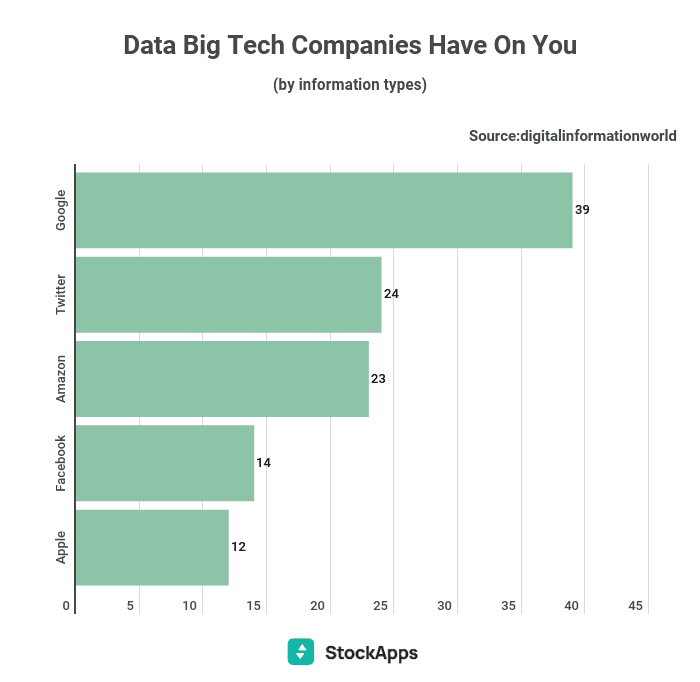
DataCheck, StockApps, Digital Information World: The number of data points big tech companies have on individual users.
Major tech players have recently significantly increased their cybersecurity investments directly into R&D or acquiring relevant products to bolster in-house expertise. In 2022, Alphabet—Google's parent company—acquired Siemplify for $500 million and Mandiant for $5.4 billion. Similarly, Microsoft has also actively sought to add cybersecurity IP and products to its architecture by spending $500 million for RiskIQ. These acquisitions were made at a significant premium, highlighting the importance of enhanced cybersecurity infrastructure and practices.
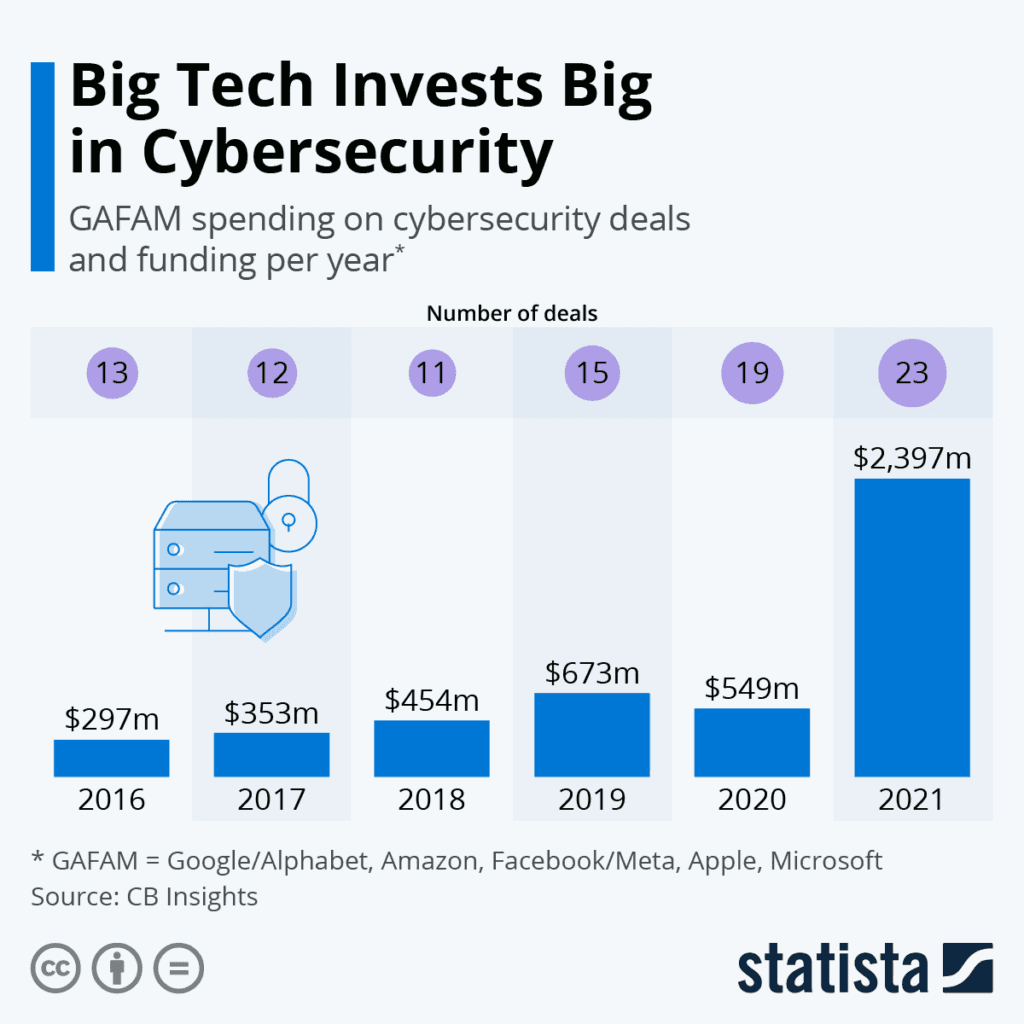
DataCheck, Statista, CB Insights: Big Tech has substantially ramped up its investments in cybersecurity, growing by around 800% in five years from 2016 to 2021.
Consumer-facing companies typically manage vast amounts of data, often more than business-oriented ones. Such platforms also host various apps and services to gather, exchange, and correlate data. This evergreen symphony of information flow requires deeply embedded encryption and other security measures, often lacking in the corporate world, where a given organization is as secure as the tools they use. An unwavering focus on user and data privacy underscores its importance in today's online landscape.
For users, cybersecurity and data privacy are necessary and often decisive factors in choosing a platform or product. I decline cookie requests, flag overly intrusive ads, and seek solutions to reduce my personal data exposure daily.
In a corporate setup, cybersecurity becomes a strategic focus, which often translates into the following:
PR campaigns touting investment in infrastructure and customer security,
Prolonged deliberations on further funding or the acquisition of the latest cybersecurity tools,
And then, when they find the tools, they can't use them at their full potential.
Bargaining hard to ensure they secure the best deal, often at the expense of functionality.
"We procured the premier email security tool at a huge discount. It's the best; we're undoubtedly protected now, even if no one knows how to use it."
Delegating immediate fixes to the IT department.
The misplaced belief that if nothing's gone wrong yet, it won't in the future.
In cybersecurity, assuming something is "not broken" is naive. If hackers are perpetually refining their tactics, how can a company remain safeguarded without adapting? As software and cloud continually evolve, the type and complexity of vulnerabilities are also increasing rapidly.
More from our CTO, Fabrice Delhoste:
In some organizations, cloud adoption has also challenged the adoption of enhanced security practices. Traditional security teams face some challenges to ramp up with those new technologies, while DevSecOps transformation may be out of their control.
According to the National Vulnerability Database, the number of new vulnerabilities discovered in 2022 increased by 25% to 25,000+. As of 31 August, the number of new vulnerabilities discovered in 2023 had already reached 18,700.
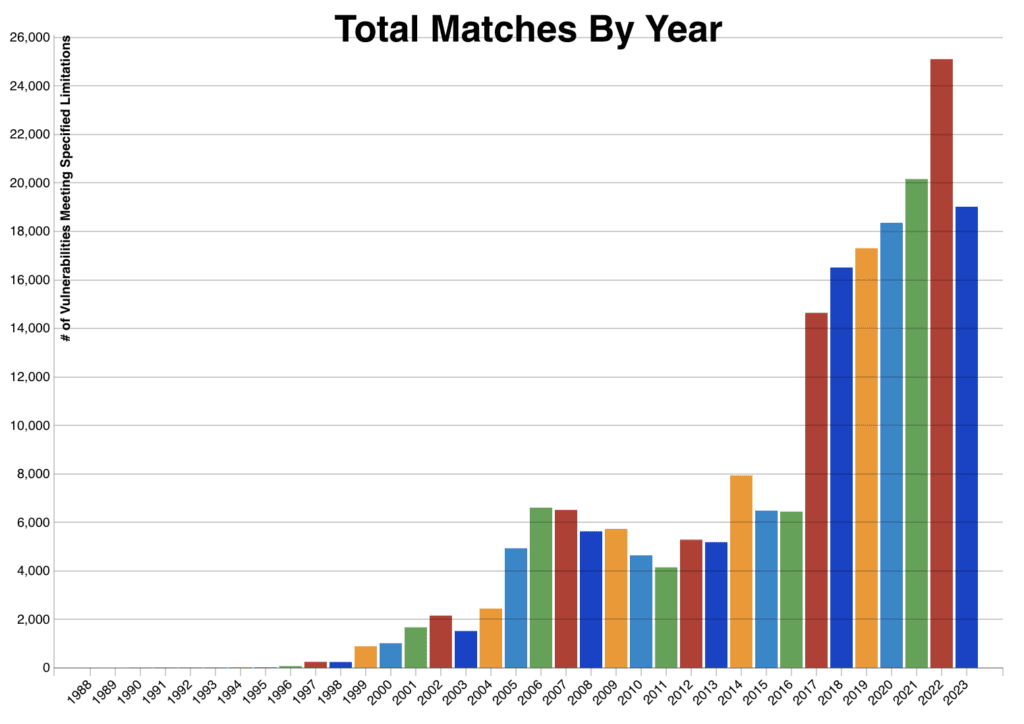
DataCheck, NSIT —National Vulnerability Database: Plotted in the graph above the number of vulnerabilities discovered every year,
There are also myriad other non-cybersecurity-focused tasks and discussions, often dominated by KPIs and, occasionally, ethics. Is this the extent of most corporate cybersecurity practices?
Why do consumer-tech entities outpace their corporate counterparts in adopting robust cybersecurity practices? Regulatory authorities certainly play a part, pushing significant platforms like Facebook, WhatsApp, and TikTok to adhere to stringent data security guidelines. Moreover, these platforms face the looming threat of reputation damage, which could potentially collapse their business model — their primary concern.
Let's take a look at where corporations and leaders are lagging behind their peers in the race to develop a robust cybersecurity posture:
Misconceptions about Cybersecurity
1. The "Compliance is Enough" Conundrum
Meanwhile, similar large enterprises are not concerned about what lies inside their house: intellectual property, employee data, huge codebases, and other financial and non-financial transactional data. What's securing that? Who's regulating that? One might say that each of these enterprises has to suffice "strict" compliance guidelines and standards to achieve industry validations such as NIST Cybersecurity Framework, PCI Data Security Standard, SOC2, HIPAA, and ISO/IEC 27001. But the truth is, compliance is not equal to security —and any organization that thinks otherwise is slowing down its path to a more secure one.
In most cases, compliance standards are the basic level of security and privacy an organization needs to have to be considered worthy of doing business. These organizations would do the bare minimum to be compliant and meet deadlines. It's like ticking things off a checklist without understanding the intent behind that checklist.
Instead, organizations should treat security and compliance standards as a starting point for their cybersecurity strategies. Starting with any of these frameworks is an excellent way to reach the basic security levels. Instead of starting from nothing, the organization can have an essential security structure. It can better define the path forward for its Security, SOC, and IT teams —and the rest of the company.
A word from our CTO, Fabrice Delhoste:
There are also some more intrusive certification/compliance standards (e.g., ANSSI CSPN or CC, PCI-DSS).
The issue, then, is they are often overly complicated to achieve (for example, you need to certify every single version of the software and engage in extensive audits), and so, financially, some organizations reduce the scope to be compliant or do it for one version to unlock sales. They are also often unaligned with modern cloud or SaaS applications.
2. Cybersecurity is all about technology.
Imagine taking cybersecurity orientation lessons and training on how to find malicious emails. It sounds boring, right? Training employees on cybersecurity and digital health best practices is important to create a first line of filters and defense. Per a research survey done by Proofpoint:
Compared to 2022, organizations see a 76% increase in direct financial loss from successful phishing attacks.
Less than 40% of people, on average, could define what phishing, ransomware, or malware were
Only 56% of organizations had a security awareness program to train their employees.
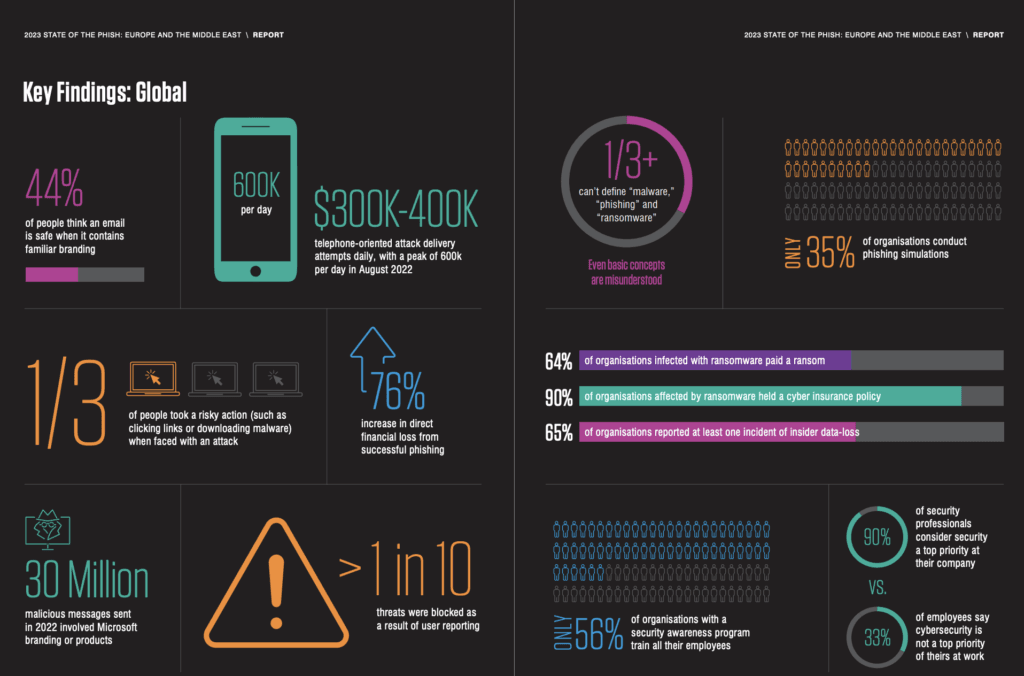
DataCheck, Proofpoint: A snapshot of the State of the Phish Report by Proofpoint.
How should companies and teams approach this? Cybersecurity is a technical, critical, and infrastructural part of any organization. It creates the boundary line between a good business and a failed one. If adversaries could easily play around with its software, Microsoft wouldn't be Microsoft.
Cybersecurity must be embedded into the culture for continued success. It should define how people are supposed to behave in the premises —virtual or physical— of their company. At Mindflow, we do our best to be the best at adopting a human-centered cybersecurity and governance approach —it has worked so far and, more importantly, hasn't felt like a burden to anyone. 🚀
Let's analyze this using this data from Statista, FBI, and Datto.
Phishing is the most common attack vector. Attackers usually create a sense of urgency while impersonating a higher-up executive or direct managers of the victim to seek critical information such as login credentials, account details, etc. As a result, business email compromised-related losses make up the lion's share of enterprise losses due to failed cybersecurity and governance practices—$2,396 million in losses in 2021.
Cyberattacks are rising and have become increasingly complex and challenging to detect. This has led to sustained and unfortunate growth of corporate and government data breaches, which have grown at over 20% each since 2021.
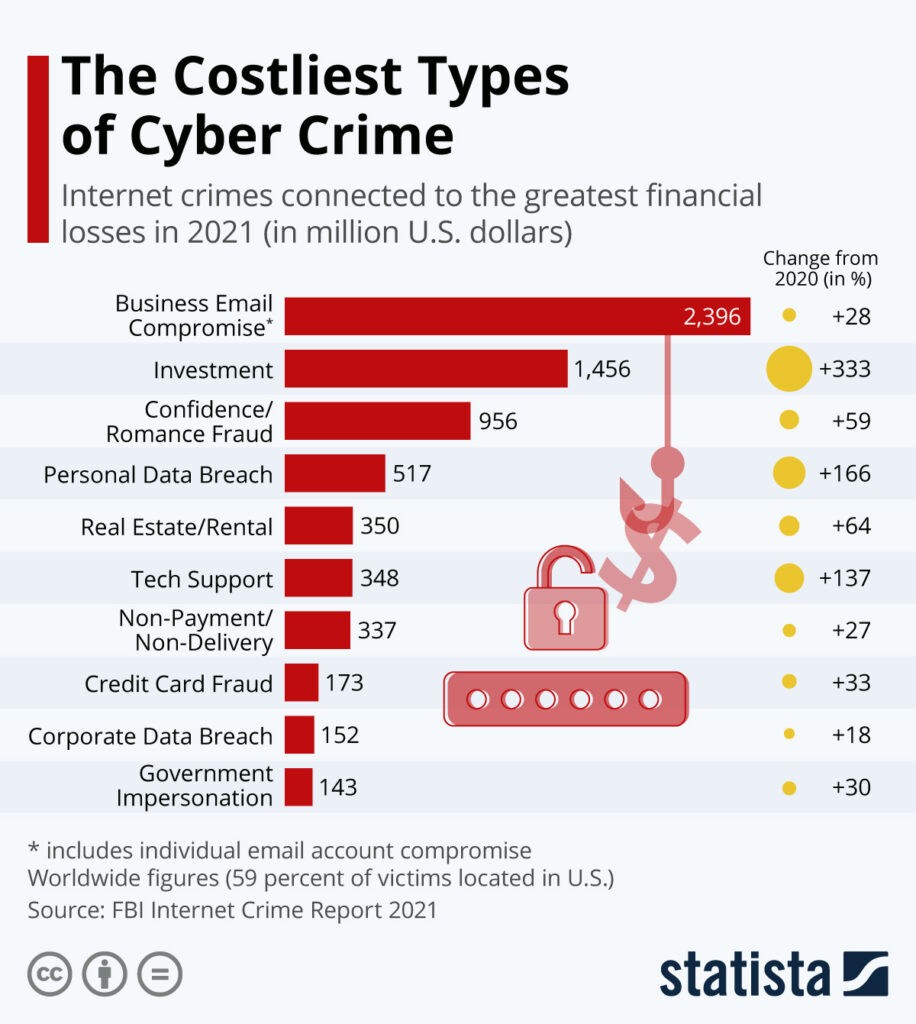
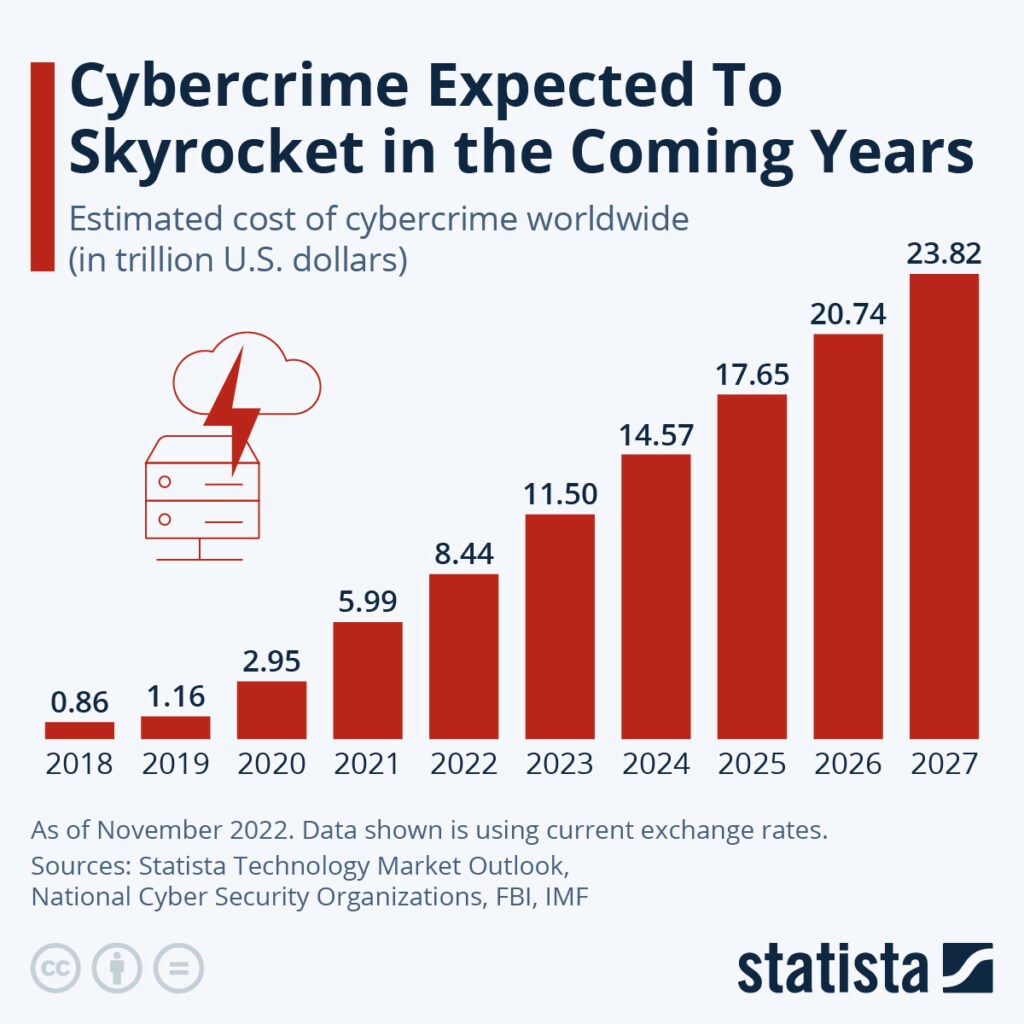

Cybersecurity is not failing but not succeeding at keeping the adversaries out of bounds. Solving this requires a deep understanding that cybersecurity is not only a technical discussion but also of strategic and financial importance. When viewed solely as a technical topic, it becomes too operational as it is hardly ever given priority when long-term strategic planning discussions are held —CISOs are hardly given the same stature as other CXO-level executives.
Viewing cybersecurity as an organizational issue would also result in the impending transition to a management challenge. Cybersecurity can only be implemented correctly if considered and communicated as a technical lever of excellence rather than a strategic one for any work culture.
When cybersecurity efforts address only technology, the result is poorly informed company leaders and poorly protected organizations.
3. Preferring protection over resilience
We still live in a corporate world where leaders flaunt their cybersecurity credentials—not the login details but the lengthy conversations about the number of tools they've implemented. #security, right?
Yet, the spotlight remains solely on protection. As they say, put enough walls, and nobody can get in. Per a Harvard Business Review and MIT research:
Roughly 76% of leaders believe they have built a robust cybersecurity arsenal through enough strategic investments in vendors or startups.
87% projecting their cybersecurity budgets to skyrocket in the next year.
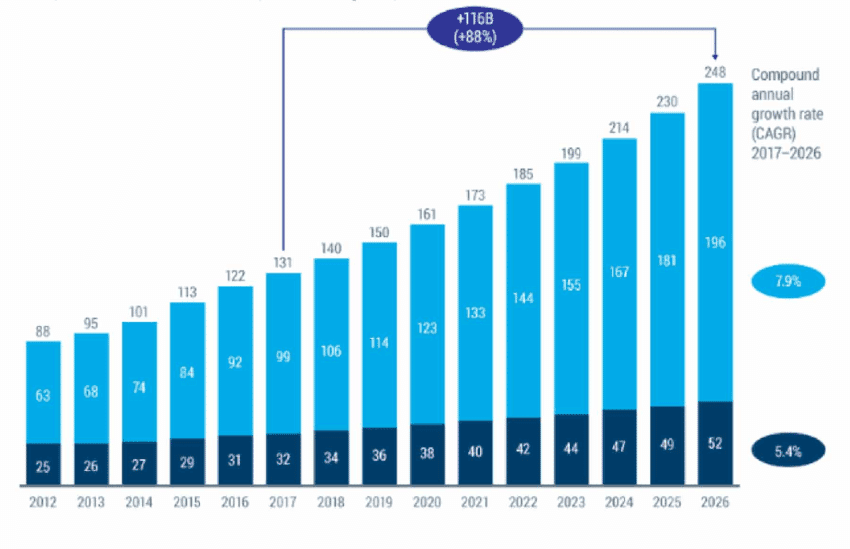
DataCheck, AustCyber: Cybersecurity spending has grown significantly and is projected to grow in the enterprise space.
This protection-first approach can only go so far. With the rapid rise of AI-enabled cyberattacks, protection alone won't do. So, it's not about if but when the breach happens. How should corporates prepare for this? The conversation needs to pivot from protection to resilience. Think of it like this: instead of just building a ship that can't possibly sink (which, history tells us, can be a dangerous assumption), you're also preparing your crew and passengers with life vests and drills —and all other resources needed if it comes to the worst possible scenario.
Resilience pushes corporations to embrace the worst-case scenario, strategize for it, and ensure swift and efficient recovery —in case anything goes wrong despite all the protection.
The Solution: Cyber Resilience Approach
NIST describes cyber resilience as " the ability of an information system to operate under adverse conditions or stress, even if in a degraded or debilitated state, while maintaining essential operational capabilities and to recover to an effective operational posture in a time frame consistent with mission needs."
Later, blog articles will explore the strategic solutions to these issues. But before we leave, here's a cyber resilience framework developed by a BCG and Sloan MIT research group. This framework can be broadly divided into four phases, covering everything from what happens before a cybersecurity breach to the after-effects of a cyberattack.
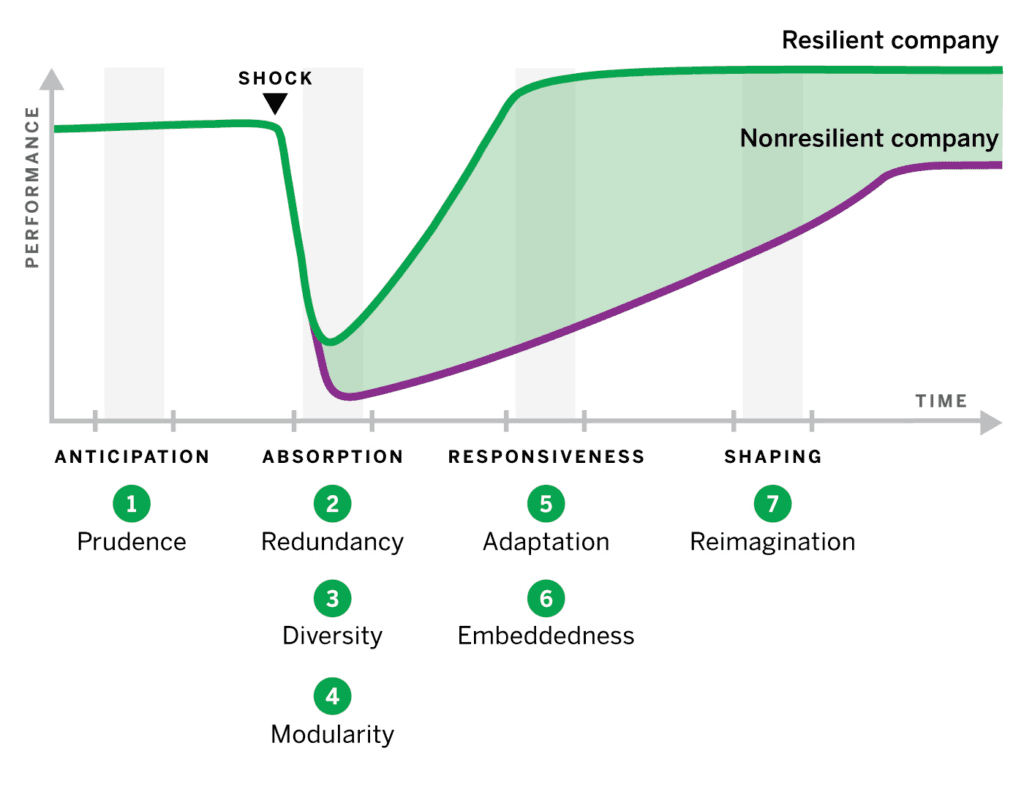
1. Anticipation: Before the Breach
People and Teams: It is important to know who has to be involved if something wrong happens. This has proven to be a tremendous version for large companies. Hence, it becomes necessary for organizations to know their assets and understand what role they play in a crisis.
Principle of Prudence: This principle asks security teams always to expect the unexpected. Security and other teams in an enterprise should have enhanced knowledge of known and unknown cyber threats. This involves putting the guardrails so the business can operate smoothly during a cyber disruption.
Tabletop Exercises (TTXs): These are internal reviews and cyber security simulations similar to drills. It needs to include all departments, not just cybersecurity and IT.
2. Absorption: Reducing the Immediate Impact
Redundancy: This includes duplicates or proxies of data, such as local data storage or virtual duplicate instances. This can be understood using the natural and biological principles where organisms generally have a first line of defense, and if that fails, they have backup resources to rely upon.
Diversity: Organizations should leverage a mix of people, processes, and technologies to reduce risk. Diversity leads to complexity, which can make the company cyber-resilient in an inherently defensible manner from adversaries. Overreliance on a single system or defense method can make an organization an easy target, as there is a single point of failure.
Modularity refers to an organization's ability to isolate affected systems from healthy systems and substitute: This refers to the ability of an organization to isolate affected systems from healthy systems and substitute the compromised resources with functional ones. Most implementations of zero-trust architectures focus on enabling the possibility of isolating components of an organization's IT infrastructure. At the most basic level, the infrastructure should allow for at least essential access management and, preferably, a role-based access management system.
3. Responsiveness: Reducing the Duration of the Breach
Adaptation: Dealing with a cyber attack or a data breach is about responding quickly and adapting those responses to what the adversary is doing. It's essentially a cat-and-mouse game. The threats presented by an adversary can be both known and unknown. Thus, it is paramount for any organization to learn as much as possible about a hazard and adapt quickly as per the resources available —this builds on the agile methodology applied to cybersecurity.
Embeddedness: Any organization's IT infrastructure and data warehouses are built up using a network of products and services. It is essential to understand that the negative impact of any attack can have ripple effects across the whole ecosystem. It becomes the responsibility of the leaders to communicate about any attack or breach to its second-tier stakeholders.
4. Shaping: Post-Breach Actions
Reimagination: This involves a post-breach retrospective. The goal in this phase is for the organization to learn as much as possible about the attack's source, causes, and impact. Resilient organizations can learn efficiently from these instances and implement systems and frameworks that enhance resilience even more. In most cases, cybersecurity and leadership teams can constantly develop better solutions.
Enter Mindflow: Championing Cyber Resilience
Mindflow enables organizations to shift from a protection-first to a resilience-first approach. Mindflow is not built to be another tool in the enterprise-grade cybersecurity arsenal but a dynamic platform that can adapt to any team's or organization's IT and cyber security stack. Here's how:
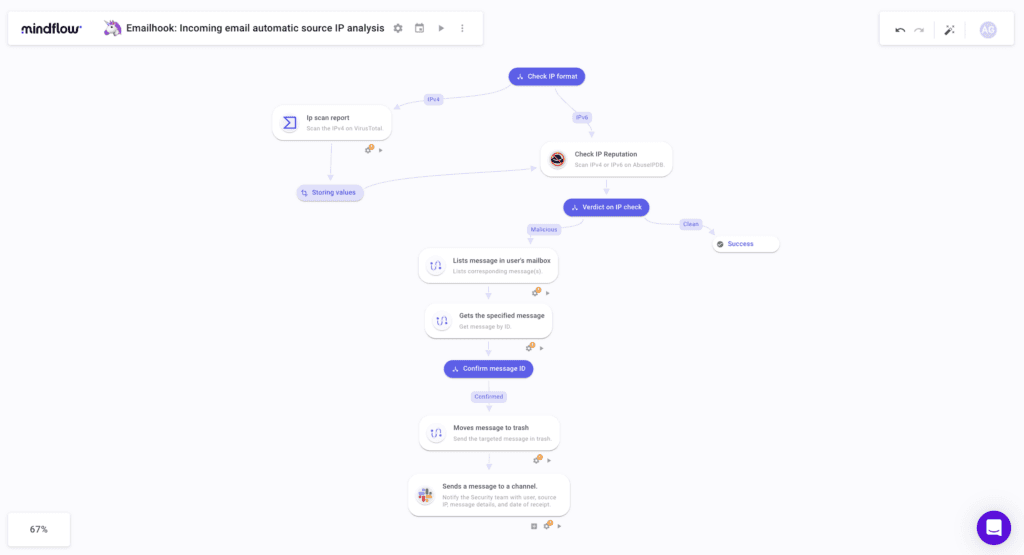
Automated Proactive Defense: Mindflow's robust automation and orchestration capabilities enable it to detect alerts and threats in real-time by integrating with whatever tool Endpoint Protection, Threat Intelligence, Email Security, and Compliance tool the organization uses. Mindflow integrates with a wide variety of best-of-breed cybersecurity tools. Instead of waiting for threats to manifest, Mindflow can proactively locate information about these alerts, create a ticket in Jira in a flash, send a message to the team lead, and remediate the alert —all of this is completely automated. 🤖
Orchestrated Responses: Mindflow's orchestration capabilities ensure that all components of an organization's cybersecurity apparatus work harmoniously. Seamlessly coordinating threat detection, mitigation, and post-event analysis provides a faster and more reliable remediation of threats.
Minimizing Human Error: Mindflow addresses this by automating complex tasks that would traditionally be manual, thereby reducing the chance of oversight or mistakes that could compromise security. Automating cybersecurity workflows brings —an often overlooked advantage— consistency to the outcomes. With consistency, an organization can better plan and react to any situation. Some major benefits of consistency are clarity, structure, and trust.
How can automating cybersecurity workflows bring consistency?
Consistency enables benchmarking and tracking performance to help define objectives and plan future actions.
Automation allows for refining processes and versioning. Further, errors can be identified and eliminated on the fly, improving reaction time.
Automation ensures accuracy and robustness at scale, increasing readiness. Read more…
Integration Across Platforms: Mindflow stands out by seamlessly integrating with a vast library of cloud, SecOps, DevOps, ITOps, and other business-critical products. This ensures that information flows smoothly across systems, leading to more informed decision-making and a comprehensive view of the organization's health.
Empowering Decision Makers: Beyond automation and orchestration, Mindflow provides critical insights, role-based access management (RBAC), and analytics to decision-makers. This data-driven approach ensures that leaders are always equipped with the information they need to make informed choices about cybersecurity, reinforcing a culture of resilience within the organization.







