Mar 21, 2023
Hugo
David
Today, in How to Automate, we'll examine how we can perform vulnerability prioritization with GreyNoise.
Common Vulnerabilities and Exposure (CVE) are identifiers for publicly known vulnerabilities in software or hardware products and are assigned by the MITRE Corporation.
Attackers can use CVEs to exploit vulnerabilities and gain unauthorized access to systems, steal sensitive data, or carry out other malicious activities. As soon as a CVE is published, attackers can, if not already done, start developing exploits to take advantage of the vulnerability. It is thus essential to perform vulnerability prioritization upon their release.
The number of discovered CVEs keeps increasing year after year. Research papers have already documented this exponential increase in numerous papers. For instance, 2022 saw more than 15,000 CVEs released. On top of this increasing pace, there is evidence that attackers are weaponizing these CVEs increasingly faster. This trend is due to several factors, including the rising availability of vulnerability information, the growing sophistication of attackers, and the availability of exploit kits on the dark web. Attackers also leverage automated tools and techniques, such as fuzzing, to identify and exploit vulnerabilities more quickly, whether old or new.
This increasingly hostile landscape highlights the importance of promptly patching known vulnerabilities to minimize the risk of a successful attack. However, as vulnerabilities in your networks and system are being more and more weaponized, it becomes increasingly complex to prioritize which ones to tackle first.
There are different ways to prioritize CVEs. The first and most used is to classify them according to their risk score in decreasing order, from 10 to 0. While assigning risk scores is one standard method of prioritizing vulnerabilities, it may not always accurately represent the actual threat posed to a system. Why? Some CVEs are either hard to exploit or not actively searched for on the web. Adding these two filters can help your teams better prioritize the CVEs that are more urgent to remediate from the ones that are challenging to exploit or unexploited at the moment.
In this article, we will explore the second alternative method for prioritizing CVEs: Are they actively being looked after on the web? To that end, we'll orchestrate 5 different tools:
AWS Inspector
Amazon EventBridge
GreyNoise
Jira
Slack

Vulnerability prioritization through GreyNoise query
We will analyze how to automate the process of vulnerability prioritization by analyzing the results of current scans on the web on GreyNoise. By using this approach, we can consider the specific vulnerabilities present in our system, their potential impact, and the current threat landscape.
As we said above, CVEs are prioritized according to their risk score. Although we're not going to do that, keep in mind that this Flow can easily be combined with or implement additional steps to classify vulnerabilities according to their risk score and exploit methods.
The goal of this Flow is to automate the notification, extraction, submission, classification, and prioritization of CVEs found in your network and systems with the help of GreyNoise and to, ultimately, reduce the risk of an actively used CVE by automatically prioritizing the remediation of such CVEs found by AWS Inspector.
Automating vulnerability prioritization through Mindflow
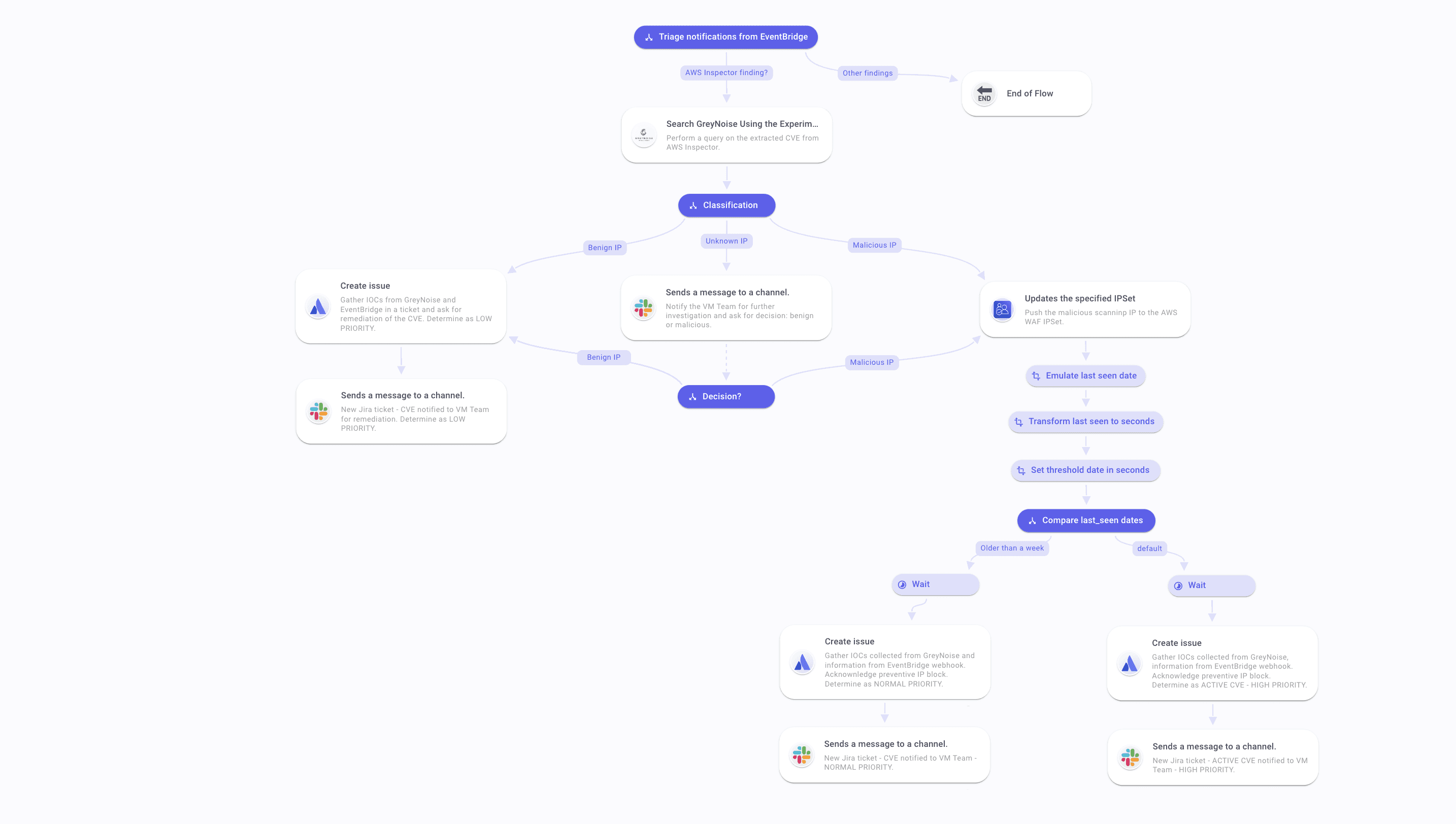
Such a flow would typically involve the following different steps, as shown below:
Trigger: This flow is triggered by a webhook from AWS EventBridge that ingests data from Security Hub, which listens to AWS Inspector findings.
Triage: As EventBridge will trigger the Flow with different alerts that may create too much noise, we will select the findings reporting CVEs. To do so, we will make an if condition where if the product name is equal to Inspector, we proceed with the Flow execution. Otherwise, the Flow ends.
CVE identification: The webhook will contain the vulnerability ID, the data we want to submit to a GreyNoise Query. You can introspect the webhook payload and pick this field to automate the extraction of vulnerability ID in future payloads. This data is pushed to the GNQL API call using GreyNoise Enterprise API.
Classification according to the IP flagged: the API answer payload will contain a lot of data that are of interest for various use cases. Here, we'll first extract the IP found scanning the web for this vulnerability. For these IPs, we'll start by removing the classification issued by GreyNoise (benign, unknown, malicious) and proceed with a first triage according to these attributes.
Unknown IP: Ask for further investigation on Slack. Upon result, classify as benign or malicious.
Benign IP: Create an issue and assign it with LOW PRIORITY.
Malicious IP: Push IP to AWS WAF IPSet.
Classification according to last seen: Once you have determined the nature of the IP flagged as scanning the web for this vulnerability, it is time to know when it was flagged. To do so, get the last seen field in the GreyNoise API answer payload to determine if it has been seen in the previous week.
If yes, create an issue with HIGH PRIORITY.
If not, classify as NORMAL PRIORITY.
Ticket creation: from then, create Jira tickets and gather the data collected from the webhook: vulnerability ID, vulnerability risk score, remediation guide; and from the GreyNoise API answer: classification, lastseen, port scanned, software in cause.
Team notification: Finally, query Slack API to post a message on the dedicated channel to notify the Vulnerability Management Team, the SecOps Team, or the IT Team, depending on what team in your organization is handling such incidents.
Additional steps
On top of this existing Flow, we can add several extra steps to automate the vulnerability prioritization process further. First, departing the CVEs found by analyzing the risk score in the EventBridge webhook. Also, suppose GreyNoise returns an IP scanning the web for this vulnerability but classifies it as Unknown. In that case, you can add a threat intelligence enrichment step by invoking your Threat intelligence platform and/or database to add an external source to contextualize an unknown IP and leave your team to classify this IP as Benign or Malicious.