Jun 5, 2023
Hugo
David
The cybersecurity landscape is following the evolution of businesses and ways of working. The proliferation of SaaS platforms, the extension of remote working, and the expansion of supply chains are dramatically changing how business is done. Cybersecurity has to follow the track to allow organizations to operate safely in this new and more complex environment.
Today's organizations are constantly evolving, increasingly interdependent, and hyper-connected. Gartner has coined a broad theme in its Top cybersecurity trends for 2023: Responsive ecosystems to coin the cybersecurity answer to this environment and its specific properties (constantly changing, more interdependent). This concept advocates for a malleable cybersecurity architecture and processes to adapt to ecosystems that cannot be conceived as your traditional fortress.
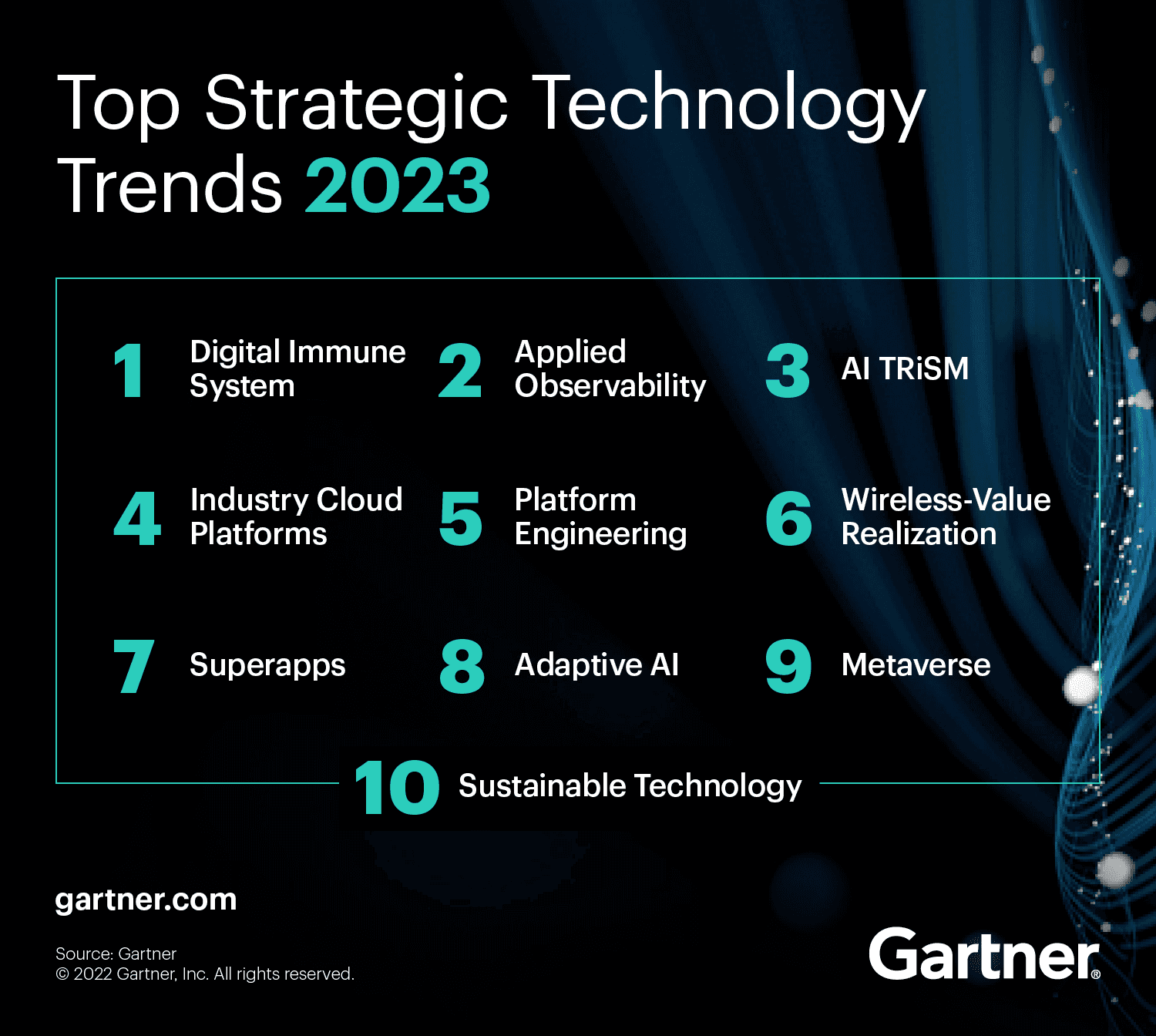
Today, we are focusing on one aspect of this theme: Threat Exposure Management. Gartner advocates for a continuous approach to threat exposure and management to face this complex landscape as part of their Responsive Ecosystem strategy. Answering this Responsive ecosystem needs to implement Continuous Threat Exposure Management (CTEM) to empower organizations to confront challenges posed by many threats emerging from direct and indirect ecosystems.
Beyond traditional cybersecurity approaches
As organizations transition from traditional methods of maintaining cybersecurity, they encounter many new challenges tied to an ever-growing digital ecosystem. Technology and business processes have evolved so quickly in recent years that the usual static and reactive cybersecurity models no longer provide adequate protection. As threats and organizations become more dynamic, organizations must respond by adopting Continuous Threat Exposure Management as part of their Responsive Ecosystem strategy.
The increasing role of third parties in digital ecosystems
The Continuous Threat Exposure Management approach goes beyond traditional cybersecurity practices, emphasizing the need for continual assessment to capture the organization's entire threat landscape, including its internal and external vulnerabilities and weaknesses. It provides a more holistic viewpoint, considering known and unknown threats and vulnerabilities.
In doing so, it acknowledges the impact of the supply chain extension through the increased use of SaaS platforms (outsourced data storage, productivity tools, business management applications, etc. The types of usage are growing every day). In taking advantage of the flexibility of these SaaS tools, organizations are piling up external vulnerabilities serviced directly by vendors. While these solutions offer substantial benefits, they also introduce new risks.
As organizations become more reliant on these third-party services, they must also recognize that threats can and will arise from sources outside their direct control. Addressing these risks requires evaluating vulnerabilities within the supply chain (data breaches, software vulnerabilities, and potential misconfigurations) that attackers can easily exploit.
Through continuous monitoring and assessment, Continuous Threat Exposure Management allows organizations to pinpoint areas of potential risk within their third-party dependencies and proactively work to mitigate these threats.
Acknowledging the human factor among vulnerabilities
Continuous Threat Exposure Management doesn't stop here. It also emphasizes the human factor as part of vulnerabilities that must be monitored, assessed, and mitigated. The CTEM concept refines and contextualizes cybersecurity strategies to focus on improving the security posture of the entire ecosystem, including internal (your infrastructure), external (third parties), and human factors (employees).
Following this holistic approach, CTEM promotes communication and collaboration among different departments and stakeholders, encouraging a culture of shared responsibility. Breaking down silos between technical teams, business leaders, and risk managers ensures a more comprehensive understanding of the threats faced. It improves the organization's cybersecurity posture through accountability, responsibility, and better resource allocation.
The need for continuous threat assessment and management
As we said above, implementing a constant approach to threat management is vital for staying ahead of ever-evolving vulnerabilities. The Continuous Threat Exposure Management methodology excels at providing comprehensive coverage of an organization's cyber risk profile.
Continuous Threat Exposure Management emphasizes regular vulnerability monitoring, including patchable and non-patchable threats, and monitoring the security posture of their suppliers by the organization to remain fully informed about their internal or external security posture.
By routinely tracking and evaluating known and emerging vulnerabilities, organizations can dynamically understand their threat landscape and allocate their resources accordingly. This mindset equips organizations to proactively identify and mitigate vulnerabilities before they can be exploited, drastically reducing the risk of security incidents.
Focusing on the human element and how it contributes to the overall threat exposure enables the organization to measure, assess, and mitigate risks associated with human error, insider threats, and phishing. CTEM programs work to eliminate a significant portion of potential vulnerabilities that stem from non-technical sources through collaboration and cohesion, significantly improving the organization's ability to defend against and recover from attacks.
Business risks and priorities from the attacker's lens
Continuous Threat Exposure Management defines cybersecurity as a holistic approach. The organization is understood as an ecosystem rather than an individual entity with intricate business goals and processes. As organizations examine their digital ecosystem and cybersecurity measures, an essential consideration is aligning Continuous Threat Exposure Management initiatives with the organization's overall business risks and priorities, considering the organization's dynamics to make it thrive rather than impeding it.
By making cybersecurity an interdepartmental concern, organizations can integrate the needs and concerns of the departments constituting the organization and foster enhanced communication and collaboration between them to embed cybersecurity principles throughout the organization, fitting their different needs.
CTEM enables a more targeted and practical risk management approach involving all stakeholders by contextualizing security threats and vulnerabilities with business objectives. Understanding the potential impacts of threats on business operations enables organizations to prioritize contextualized mitigation efforts that focus on preserving valuable assets and business processes and minimizing mitigation consequences.
CTEM also emphasizes the harsh reality that no organization can fix all its vulnerabilities. Even the biggest teams don't have the time, technical know-how, or resources to keep up with the flow of threats that must be prioritized. Considering the potential business impacts of threats is thus central to cybersecurity measures' operational viability and success. Continuous Threat Exposure Management acknowledges that some security efforts may have unintended consequences, such as impeding the flow of information or disrupting workflows.
Continuous Threat Exposure Management emphasizes the "think like an attacker" approach to risk assessment to improve target efforts. The organization analyzes threats through the attacker's lens to prioritize better vulnerabilities according to their respective criticism, attractivity, and ease of exploitation. Thus, organizations can better anticipate potential risks and develop more informed cybersecurity strategies.
Thus, CTEM ensures that organizations' cybersecurity strategies protect their critical assets without hampering growth and innovation by balancing security concerns with business objectives and assessed risks.
Defining success metrics and risk acceptance criteria
An essential aspect of implementing a Continuous Threat Exposure Management program is defining appropriate success metrics and risk acceptance criteria that balance security concerns with the organization's objectives. By establishing clear metrics and thresholds, organizations can evaluate the effectiveness of their cybersecurity efforts, ensuring that their strategies not only address potential threats but also support operational and strategic goals.
Setting comprehensive success metrics enables organizations to measure the performance of their cybersecurity initiatives and track their progress over time. These metrics may include reducing vulnerabilities, improving the organization's security posture, or decreasing the time required to detect and respond to security incidents. Clear success metrics not only facilitate the assessment of cybersecurity effectiveness but also help identify areas for improvement.
Each organization must balance securing its digital assets with the practicality of implementing risk mitigation measures. Establishing risk acceptance criteria involves determining the organization's threshold for tolerating potential threats. Organizations can make more informed decisions about resource allocation and threat management strategies by defining risk acceptance thresholds. This approach enables them to prioritize the most pressing risks and focus on mitigating vulnerabilities with the most significant potential impact on their operations.
Incorporating risk acceptance criteria into the Continuous Threat Exposure Management methodology ensures that the organization's security efforts are grounded in a comprehensive understanding of its digital ecosystem and the associated potential threats. This understanding enables the organization to take a more proactive approach to risk management, focusing on addressing vulnerabilities before malicious actors can exploit them.
Conclusion: is this new?
Continuous Threat Exposure Management brings together a lot of already-known best cybersecurity practices to face a rapidly changing, increasingly interdependent, and complex landscape. In today's environment, more than before, organizations are flexible, hyperconnected, and intertwined with their clients and suppliers. This trend is set on the increase as SaaS tools grow, and the ingestion of ever-growing data sets advocates for externalized storage. Moreover, as employees increasingly turn to hybrid ways of work, the exposure keeps getting polymorphic and more complex.
Cybersecurity cannot keep up with this landscape as usage and technology evolve. It must rethink its approach to securing the organization without building barriers.
By coming up with the concept of responsive ecosystems, Gartner puts the finger on what the organization is today and how cybersecurity must evolve to keep protecting it without impeding its pace of growth and innovation. To do so, they are bringing back to light concepts such as risk assessment and human awareness to stress their importance and the need to take them into account to secure the organization. Gartner also considers the growing interdependence between suppliers and clients, where monitoring cannot stop at your organization's frontiers. A secure organization constantly maps its surroundings because it is part of a broader ecosystem where one breach can impact everyone.
Continuous Threat Exposure Management is not new per se, but a welcome reminder.








