Dec 29, 2021
Paul-Arthur
Jonville
Attacks are growing in volume and variety. Security operations centers use diverse tools to handle the work: SIEM, IDS/IPS, or EDR, for instance. However, companies struggle with an overwhelming amount of security event data without enough human resources to deal with them adequately.
The companies are then turning to solutions such as Security Orchestration, Automation, and Response (SOAR) that can help them manage tasks like data aggregation, enrichment, correlation, and remediation.
Still, good data is the foundation of any strong defense. A SOAR relying on redundant or irrelevant data will not be effective. This is where threat intelligence becomes essential.
Threat intelligence is at the heart of the SOAR
Today’s security technologies often feed your incident response team massive logs and events. However, these logs and events are riddled with false positives, duplicates, or missing enrichment, enabling your analysts to make the best decision.
A SIEM usually does this work, effectively aggregating data across your internal network. However, SIEMs aren’t first made to enrich this data, deliver raw information to your analyst, and lack enrichment features.
Thus, your SOC analysts must manually work through this data to distinguish real from false alerts, switch between the different tools they use, and make decisions based on the processed data. They end up with a massive amount of work to process each incident, leading to alert fatigue and multiple panes of glass.
The SOAR came around to answer this precarious state by combining three existing tools:
Security Incident Response Platform (SIRP) gathers alerts and events from different sources, such as your SIEM or IDS. The analyst can add related data like logs or IOCs and then can compare the results to threat intelligence feeds;
Security Orchestration and Automation integrating tools and allowing to build workflows;
Threat Intelligence platforms (TIP) aggregate various TI feeds to enrich incoming alerts.
As a result, SOAR —first coined by Gartner— is an orchestrator and an automator. This means it works on playbooks (or workflows), integrating multiple security technologies in repeatable and automated security workflows designed to describe threats and how to handle them. This frees up time for your humans to tackle more complex goals and is a natural complement to your SIEM.
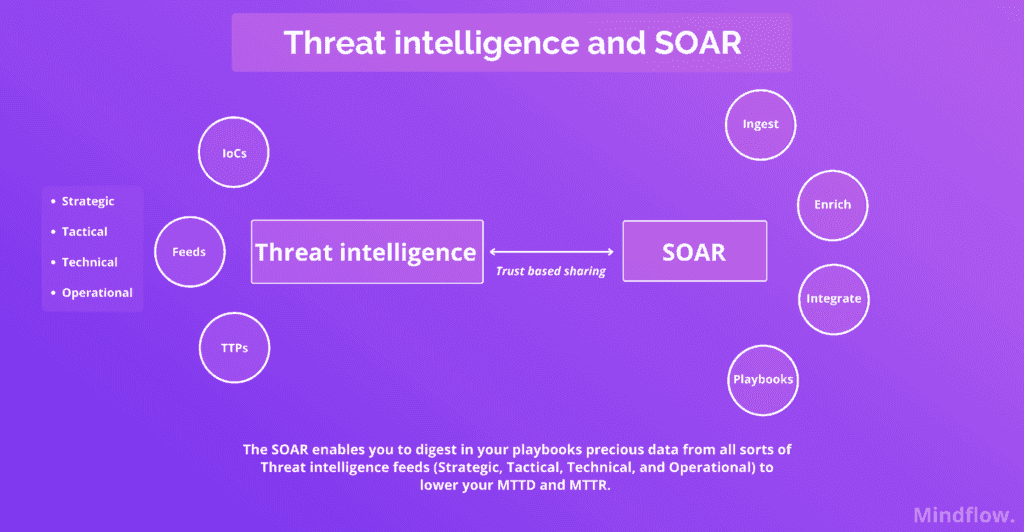
However, you need a full, integrated view of external threat information to make this work. This way, your SOAR can fully understand what is happening and take the right steps to remediate threats.
We’ve described how a SOAR combines a SIRP and an SOA. Now, this is where things get interesting for our demonstration. The third tool a SOAR combines with the first two described supra is the TIP, which is crucial.
As we said above, SOAR solutions work via playbooks. The problem is that these playbooks run on data fed into them. Thus, their efficacy will only be as good as the data used. SOAR naturally ingested TIP with SIRP and SOA to make a unique tool.
Threat intelligence is paramount to sharpen your security stack
The SOAR can ingest Threat intelligence to take on two challenges encountered by more and more SOCs worldwide: information overload and prioritization.
SOC is facing increasing attacks daily. We've found that, on average, security teams face more than 100,000 attacks daily. Operating in strategic fields, such as healthcare, some companies can face millions of attacks per day. Security teams can't keep up with the threats because they rely on manual work to deal with the plethora of information. As a result, they investigate only a fraction of these incidents, around 10,000 on average.
This leaves room for attackers to sneak in and wander into your systems unnoticed for months. On average, a breach takes 212 days to be detected and 75 days to be remediated. That's precisely 287 days of unseen damage.
Of course, there are tools to ingest all of this information. SIEMs have been around for decades, and they indeed do it well. Still, dealing with this amount of information is nearly impossible if you have to work through each incident independently. This is why people came up with threat intelligence. Known attacks, their patterns (Tactics, Techniques, and procedures), or pieces of evidence left behind (Indicators of compromise) are listed in feeds that help analysts deal with the incidents they're facing.
This way, Threat intelligence can reduce the time Security teams need to research and triage alerts. However, Threat intelligence feeds are various. Ingesting all the information they gather tends to be as challenging as ingesting the information ingested by your SIEM.
This is where the SOAR comes in. Via automated playbooks, a SOAR allows you to update threat intelligence into your system continuously. More, a SOAR like Mindflow, no-code, and drag-n-drop takes one more step in easing the work by allowing you to create steps by just dragging one of the services you want to call (a TI feed, for instance), dropping it on your workflow (to, let's say, enrich a phishing alert), and connecting it with other steps (to create an automated phishing investigation workflow).
In supplying automated threat intelligence in real-time, the SOAR allows you to be comprehensive and fast in triaging the alerts and to have an exhaustive view of the threats coming in, not leaving some of them unnoticed.
Besides enabling you to distinguish real threats from false positives, threat intelligence also provides the basis for prioritizing threats. Analysts still have to deal with thousands of daily threats even after the initial triage. Among them, some are minor, and some are major. Even though all the threats should be handled in an ideal world, you need to consider and prioritize the most dangerous ones first. Again, this is where Threat intelligence is crucial. You can have a more comprehensive view of the threat and treat critical ones first.
SOAR = Lower MTTD and MTTR
In cybersecurity, we use several metrics called Key Performance Indicators (KPIs) to benchmark our stacks and determine whether or not they're efficient in handling the threats.
Threat intelligence and the SOAR impact these KPIs by working on two key metrics: Mean-time-to-detect (MTTD) and Mean-time-to-response (MTTR). We said above that, on average, companies need 212 days to detect and 75 to remediate threats. You can imagine that related MTTD and MTTR aren't good in this context.
So, by automating the Threat intelligence, the SOAR helps you lower the MTTD by keeping your security stack as up-to-date as possible. Most basic threats (which compose most of the threat landscape) are known and listed on such TI feeds. Having the capacity to ingest all the data makes your security stack undoubtedly more efficient in keeping you unbreached because the "unknown unknowns," which are the last things you want when you're in defense mode (you want to have the most comprehensive knowledge of the potential threats you're dealing with to be able to defend against), are decreasing fast with accurate and up-to-date intelligence.
Even though your TI is top-notch, you have to be able to remediate quickly. Cyberspace is characterized by fast, light connections, minutes, or even seconds, which equals Mo or Gos downloaded or corrupted, which can differentiate between a successful and a failed breach.
This is where the ability to handle incidents from detection to response makes the SOAR a unique and much-needed tool in a security stack. Automated playbooks can help you detect threats and remediate them, thus lowering the MTTR.