Oct 10, 2022
Paul-Arthur
Jonville
More and more companies are shifting to the cloud. It's less demanding to run and allows for more flexibility for companies. Vendors also benefit from the cloud by providing their products via the cloud.
Almost every security service provider now provides some of its services on the cloud, including the cloud SIEM. To them, having a cloud-based SIEM is a must in environments that generate many more alerts than traditional on-premise architecture.
From this point of view, it makes sense. However, cloud environments have their own set of native tools that generate alerts, so a cloud SIEM can seem a bit redundant for cloud-based enterprises. We must determine how to approach Legacy SIEMs, Cloud SIEMs, and Cloud Security Automation. We'll see that legacy SIEMs are pretty much done because cloud SIEMs are unanimously offering better conditions for modern enterprises unless exceptions are made.
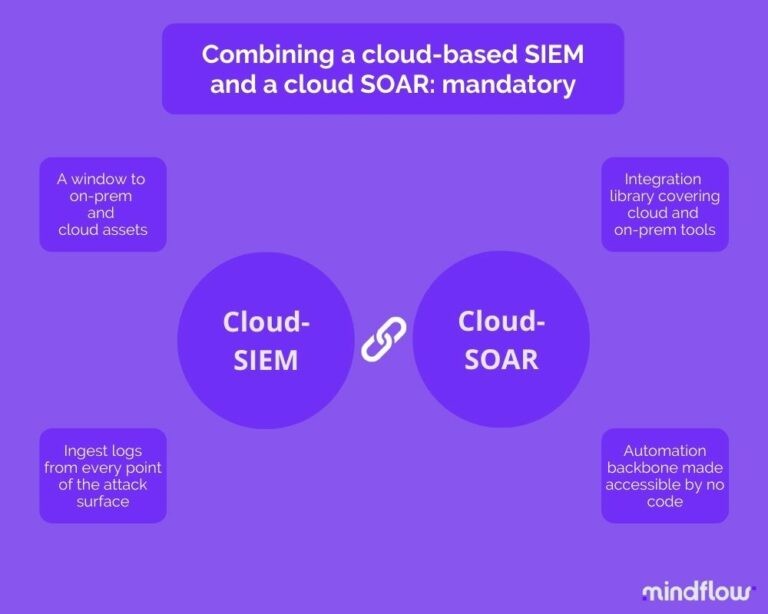
It's trickier for hybrid companies to work between a public cloud and on-premise equipment. There's a need for a control window in both environments. However, in this case, the number of alerts is gargantuan, thus the need for some arms' work integrated with the SIEM. This is why SIEM vendors have been buying SOARs (Security Orchestration, Automation, and Response platforms) these last few years.
However, let's take a long-term view and think five years from now. Cloud-based enterprises will be the new standard. The focus will be on whether I can connect to all my SaaS on the cloud. Here, the Orchestration and automation platform will be the central point of your cloud security architecture.
The issue with legacy SIEMs
Even if SIEMs have been out for 20 years and are considered the core of a state-of-the-art cybersecurity architecture, they still face many issues that most companies will face someday. Among these issues, let's list the most frequent ones:
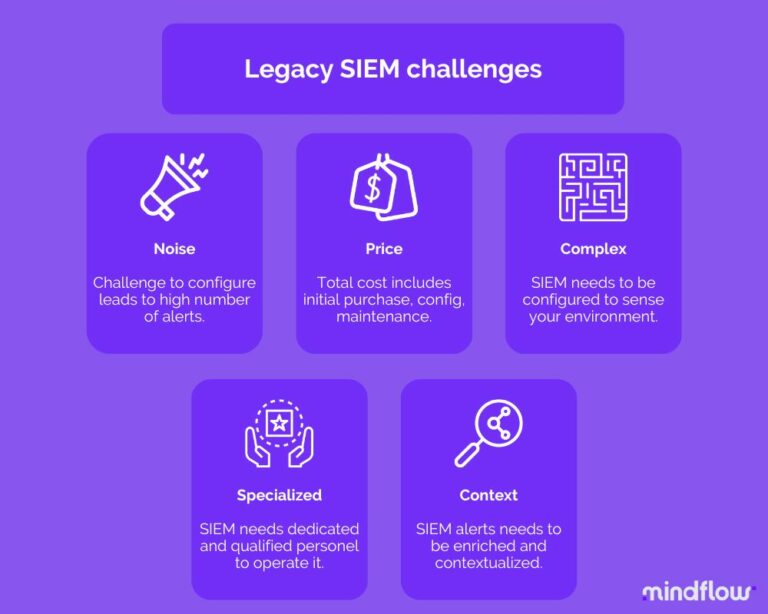
Cost: Even if the SIEM cost of initial acquisition has been decreasing (well... some are still pretty expensive, to be honest...), the majority of the cost is to be found in the costs associated with installation, out-the-box customization provided extra by the vendor, more customization on your end because why not, maintenance, log storage, and staffing. This old study from the Ponemon Institute depicts that, on average, the total cost of the SIEM can be divided into 25% going with the initial purchase and 75% toward the rest that we just mentioned. It's a lot that could be spent elsewhere.
Complex: We could say that the old traditional SIEM does nothing independently. It's not that true anymore; many SIEM platforms embark on advanced features like User Entity Behavior Analysis (UEBA) that show some real interest in detecting abnormal behavior on the network. But still, the SIEM alerts are pretty much it. Customers have been programming ad hoc automations for years to make the SIEM more active. It proved so important that vendors started to provide out-of-the-box integrations with some third-party services to ease the burden on customers' end (and create vendor ecosystems, duh).
However, a SIEM also needs configuration to work correctly. The vendor will usually add configuration to your environment at an extra cost during the initial installation. However, your environment evolves, and the SIEM rapidly becomes untailored to your threat model and your organization's needs. Ultimately, you'll have to dedicate employees to maintaining correlation rules to avoid having a SIEM unfitted to your environment that would generate false alerts and put you at risk.
High specialization: The point above leads us to the fact that SIEM is a highly specialized tool. It needs dedicated employees to maintain it in your environment. Then, you have to operate it and do the proper log analysis, which is a job. It requires lots of resources in a field that, as we all know, structurally suffers from shortages and even more among the most qualified people, typically SIEM analysts.
Noisy: Not being able to properly configure the SIEM, your company risks facing the dramatic SIEM syndrome, where you're drowned under false alerts or duplicates. There are enough studies out there to expand my point. The Netwrix research claimed that 81 percent of respondents complained that their SIEMs generated too much "noise data."
Lack of context: what is the SIEM doing? Its primary function is to aggregate system logs and to notify alerts to analysts when something unusual may have happened: incidents. However, the alert alone doesn't provide much information. It lacks context and actionable data. Thus, analysts have to start the manual work of enrichment to add context to the alert and learn how to respond.
Cloud SIEM alone is not the answer
Even though we've been talking about cloud migration for years, the last two years have marked a paradigm shift for enterprises. Many forced to adapt, albeit unprepared, started their cloud migration.
Still, the trend is set, and more enterprises are moving their assets to the cloud. The ones that have already started this journey, realizing the benefits it includes, are willing to move more assets, especially critical ones. Others have more time to prepare for this migration and want to build a new security architecture in their future public cloud.
One thing to consider here is that many enterprises are in a hybrid situation where they have an increasing part of their assets moving to the cloud although still having a part on-premise.
This new and complex environment, combining work-from-home and work-from-office, on-premise infrastructure and cloud-based one, employees from all around the world accessing data at any time, generates massive amounts of data that traditional SIEMs aren't able to ingest unless backed up by an incredibly expensive infrastructure besides the apparent shift needed to support the migration of critical workloads outside the on-premise networks and systems.
The cloud SIEM brought increased capacities to enable security teams to monitor and manage all users, servers, devices, applications, and other endpoints with efficacy and efficiency. We could sum up the cloud SIEM pros as such:
Faster deployment: The cloud SIEM does not require hardware to set up, maintain, or perform updates, thus enabling a much faster and cheaper deployment.
Scale: these SIEMs can scale to your evolving environment because they're cloud-based. As you grow, the cloud SIEM provides the agility, flexibility, and scalability to ingest massive amounts of data from your systems, on-premise or on the cloud, and process them from a single pane of glass solution.
Staying current: On-premise SIEM, like any on-premise equipment, has always had difficulties keeping up with new technologies and capabilities. One main advantage of having a cloud-based solution is staying current thanks to the ease of update deployment and the product's adaptability to the ever-evolving tech environment.
All in all, cloud SIEM takes advantage of the boundless capacities of the cloud. The logs that are ingested can be analyzed immediately and rendered. Thanks to cloud computation capabilities, cloud SIEM are increasingly integrating machine learning and artificial intelligence to enhance their detection abilities. However, these pros are missing two crucial points in the cloud.
Facing the SaaS revolution
First, the explosion of apps used by companies, also in cybersecurity. To detect, SIEMs need to connect to these products as your company evolves. There is a need for a core capability of integration. Without such capability, your company faces caveats whenever you purchase a product. Implementing any new product will take weeks or even months without a rapid integration capability.
This leads back to what we drew in the introduction. To address these needs, cloud SIEM vendors have tried to address this issue by looking for IaaS platforms to connect to their SIEM. However, the real trend has been for cloud SIEM vendors to buy SOAR platforms to create dual products: a cloud SIEM coupled with a cloud SOAR to create a holistic interface where the SIEM acts as a brain and the SOAR as the arms and legs.
This is why we saw a particular market trend in the last few years: a consolidation between SIEM and SOAR. This trend has led some analysts to write about SOAR's capacity to be an autonomous product. However, this conclusion doesn't encompass the core revolution brought by next-generation orchestration and automation platforms.
We don't believe that the acquisitions will kill the SOAR market. These acquisitions targeted what we may call First-gen SOARs. Still, they missed a new wave of SOARs that emphasized integrations and which capacities are far more important than first-gen SOARs. This led to a rethink of the company's cyber architecture, where Orchestration and Automation platforms are its backbones.
Finding a way to analyze alerts and remediate incidents
Second, cloud SIEM is not answering one of the main issues concerning their ancestors: the sheer number of alerts. Leveraging the cloud infrastructure and computation capabilities often leads to a dramatic increase in alerts. Of course, some of these alerts come from the expansion of the company's attack surface moving to the cloud, but they also come from the core configuration issue of the cloud SIEM.
The big picture is that alerts are growing. What's more, these alerts are coming from an increasing set of sensors. You have the incoming alerts from your on-prem tools and those from your cloud assets. All of them need different workflows to be handled appropriately and necessitate different integrations to allow alert enrichment and confirmation and pave the way to remediation.
Considering this, we need automation to handle this amount of alerts. We also need ways to ramp up the ability to integrate tools and create playbooks to address these use cases. These capabilities are brought by SOARs, especially those focusing on delivering modern user experience through UX design and no code logic to facilitate the automation design process. Otherwise, there's a structural obstacle to scalability.
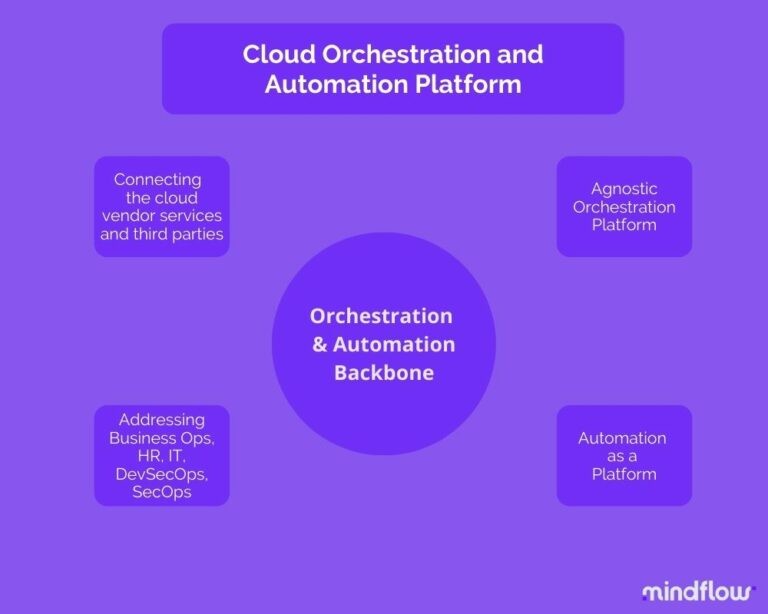
Enterprises have dozens, multiple hundreds of different tools enterprise-wide. No O&A platform can meet their needs if it can't connect to their whole tech stack environment. This SOAR evolution leads us to the final part of this article: the cloud-native orchestration and automation platform.
For Cloud-based enterprises, a cloud-native orchestration and automation platform is the first tool to have
Let's think about the cloud market in 3 to 5 years. The cloud market is expected to grow above the average market at a steady rate. It shows the increasing trend in the move to the cloud to build infrastructures that are less costly, more reliable, and more efficient.
Furthermore, facing difficulties in the macroeconomic context, enterprises will look for ways to reduce their functioning costs by moving more assets, if not all, into the cloud. Linked to this is the amount of capital and humans dedicated to value creation. Relying on the cloud helps reduce maintenance and infrastructure processes that need capital and humans.
As we started to depict above, it leads to a profound reflection on the future of Orchestration and Automation platforms.
Benefiting from the API revolution, these platforms develop an impressive ability to integrate products. Integration libraries are growing sharply and becoming a central point in the enterprise that allows the connection between every cloud-native tool. From the vendor-native tools of the leading cloud service providers to third-party SaaS provided via these ecosystems, next-gen SOAR is connecting all the tools of the modern enterprise stack.
Coupled with this integration capability-making Orchestration feature is the Automation engine that naturally comes with the SOAR. This engine makes these platforms an actual glue by connecting the flows between the tools beyond cybersecurity.
Why is beyond security important? Security doesn't stop at the SOC door. Cyberattacks have shown that security is everywhere in the enterprise, from the core conception of software to business processes like onboarding and offboarding employees. As marketers say, security needs to shift left. It is good, but finding ways to enforce it is another challenge.
The SOAR at crossroads
The advent of next-gen SOARs must make us consider their role in the enterprise. As said above, most existing analyses fail to understand the new capabilities brought by these platforms. They focus on what old SOARs brought and their structural limits. In their opinion, and by adopting their partial lecture on the SecOps automation market, they're right when saying that SOAR is vowed to be coupled with cloud SIEMs.
However, when talking about these new SOARs, strengthened by their ability to connect more tools and address a much greater number of use cases, we need to rethink the place of these Orchestration and Automation platforms. Some said that the SOAR was at a crossroads, where its destiny was between being a SIEM, or more precisely, a cloud SIEM adjuvant, and an automation backbone. These new Orchestration and Automation platforms are showing the way to a new market beyond the mere triaging tools that come with a SIEM.
In the cloud, next-gen SOAR allows the enterprise to connect its stack and to make the most of it by automating hundreds of use cases to address an unprecedented array of needs, from the old security one to the DevSecOps, by passing through HR, Business, and IT processes.
This is why we're saying that next-gen SOAR is going beyond security to target the enterprise and, thus, become a backbone to automation. Far from being adjuvants, these platforms are meta-engines, paving the way to hyperautomation.