May 23, 2022
Hugo
David
Cloud adoption is a worldwide phenomenon. Metrics about the cloud computing market are incredible. It's projected to be worth $1.251B by 2028, compared to $368B in 2021!
Conjectural and structural circumstances are heavily helping the shift towards the cloud. Uncertainties and disruptions are in today's CEOs' and business owners' mouths. The cloud has numerous undeniable advantages: consistency, flexibility, scalability, and cost savings. These advantages are what every business strives for, especially in challenging times.
According to a survey of more than two thousand participants, 90% of businesses use cloud computing mainly to manage costs. Of course, among leading Cloud Service Providers (CSP), AWS is the major player in the field (62%), followed by Azure (43%) and GCP (33%).
Even though the undeniable benefits of migrating to the cloud make it an attractive strategy, one should not forget to adapt its security in the cloud. Indeed, as businesses migrate to the cloud, sensitive data is moved there as well, making accessing them a privileged vector of attack.
Thus, dangers are various and increasing (attacks, configuration, and user errors), especially within new strategies like multi-cloud and hybrid cloud.
In these environments, ensuring cloud security is even more complex as traditional security tools face a hard time adapting.
Prominent actors are fortunately taking steps to improve the security in the cloud. AWS, GCP, and Azure provide numerous services in terms of cloud security to implement controls and avoid errors or loopholes.
Still, the maximum value can only be attained by fully acknowledging your new security architecture and taking into account the security in the cloud. Between the capabilities provided by your cloud provider and your security tools stack, you have to build a bridge and manage the flow of alerts. This is where a security orchestration, automation, and response (SOAR) platform can step in.
Dangers in the cloud
As much as the cloud represents incredible business opportunities, a cloud account is also an attack vector. Resources and data become accessible from anywhere and, without proper configuration, anyone.
Businesses are aware of it when they choose to migrate to the cloud, according to The Cloud adoption report published by O'Reilly in 2021, surveying more than two thousand businesses. When asked what was necessary to succeed with a cloud-first adoption strategy, they mostly agreed on security in the cloud being a critical concern (59% of respondents).
Cloud security breaches from CSPs-side can happen, always bear in mind that no system is invulnerable, even though they tend to be somewhat rare. Most of the time, breaches occur because of the client misconfiguration or end-users credentials hijacking.
Indeed, when we look at cloud security studies made in the last three years, we can see that top answers are account/credential hijacking (45% in 2022) and misconfiguration of cloud services/resources (43%). Only after comes breaches from the cloud provider's side with insecure interfaces or APIs (34%) and DDoS attacks (26%).
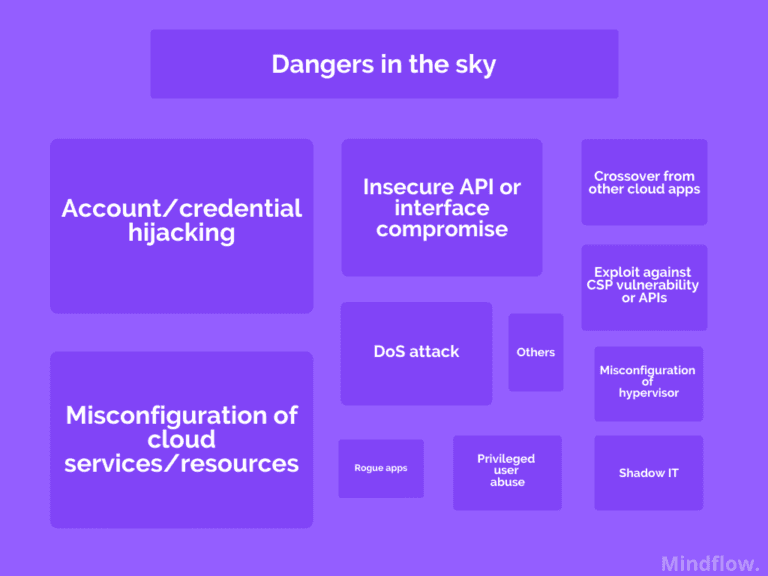
Whatsmore is the development of a multi-cloud strategy to increase resilience on behalf of businesses. According to the enterprise cloud index developed by Nutanix that surveys around 1700 IT decision-makers, more than 64% of companies plan to operate within a multi-cloud environment within the next one to three years. A further 83% of companies said they believe a hybrid multi-cloud environment will be the best option for them in the future. The bigger the company is, the more prone decision-makers are to adopt multi-cloud deployment strategies.
These changes reflect the shifting nature of the cloud. Public cloud providers will completely manage many control elements, so the surface area for attacks on this layer is significantly reduced. However, clouds will increasingly be targeted by attackers, reinforcing the need for better control of businesses' share of responsibility for what happens in their cloud environment, notably identity and privileges access.
But also, multi-cloud equals the multiplication of security tools monitoring different and somewhat impervious ecosystems. This is why one of the top concerns among decision-makers is interoperability between multiple clouds, especially security-wise (49% of answers about interoperability). Finding a solution to enable such interoperability is thus essential. Solutions such as SOARs that can streamline comms and add connectivity between all of the cloud security services, thus acting as a glue in some figurative way of speaking, will be critical for these companies.
Limits of traditional security in the cloud
Cloud environments are dynamic. The boundaries between development, operations, and security teams are fading. SecOps teams need complete visibility not just in particular flows but also into apps, infrastructure, and the network.
Companies, therefore, increasingly need a unified platform to build monitoring, detection, and remediation processes to protect their environments from breaches and attacks.
However, cloud-native environments are complex and pose challenges for SecOps and IT teams:
Cloud environments are fast-paced and exhaustive. Before assuming a particular behavior, analysts need to capture a broader picture of the overall activity. Then they can potentially identify security threats.
However, SecOps teams rely on multiple tools and thus fragmented processes, i.e., siloed security, to monitor these systems.
This approach easily creates overloads in a (multi) cloud environment as alerts are coming from everywhere. SecOps and IT teams are overworked by the sheer number of alerts and struggle to handle cases through multiple panes of glass. Ultimately, an unmanaged cloud security strategy leads to a slow down of detection and investigation processes.
Logging inconsistencies complicate threat detection. As we said, in the cloud, authentication comes from multiple places. But, as your company is virtually shattered, your authentication logs come from different sources. Thus, abnormalities are harder to spot and counter.
Also, according to the type of services you're working with, you may rely on different authentication methods and services, which adds another layer of complexity for your teams. This is one of the reasons making some companies create dedicated Identity teams.
Provisioning and de-provisioning lag. Workloads and authorizations are dynamic; teams often struggle to depart which entity should access what resource. Consequently, there's usually a big difference between your company policies and the actual state of authorization in the cloud. Add ephemeral entities on top of it, and the work quickly gets unmanageable.
Organizations often struggle to assess the extent of workload authorizations and lag in deciphering attacks and their potential impact, leading to significant security breaches.
However, a single misconfiguration of these security groups can have cascading consequences and lead to a severe breach. A lot of pressure relies on SecOps teams to ensure and respond to any incident.
Cloud providers are stepping up their security game
CSPs had to ensure adequate safety following the worldwide adoption and the nature of data and resources stored on the cloud. Soon, most major CSPs developed and provided tools in their ecosystem to ensure security in the cloud.
Stating the differentiation of responsibilities and missions implied help avoid misunderstandings about the responsibilities between customers and providers. In this regard, CSPs have developed a particular responsibility model for which contract party is responsible for what. It's called the shared responsibility security model (SRSM).
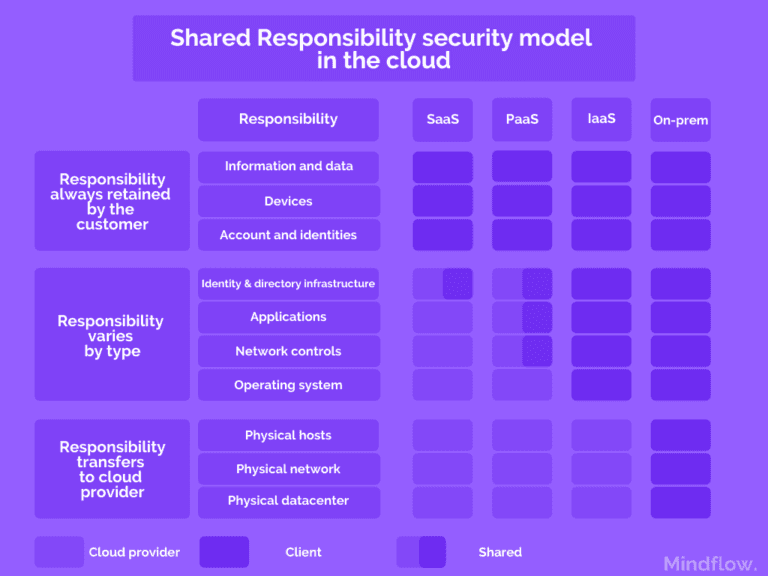
Most of the time, the SRSM states that the CSP is responsible for maintaining a client's operating environment application, while clients are responsible for what happens within the environment.
Today, 72% of participating organizations view the cloud as more secure than what they can deliver on-premises themselves for better costs. The cloud offers opportunities for centralized platforms, provides architectures that reduce the surface area of vulnerability, and allows security controls to be embedded consistently over multiple layers.
Major CSPs provide somewhat comprehensive cloud security tools to control dataflows, detect threats in their environment, and ensure compliance with your company's policies.
Microsoft Azure Cloud
Azure Security Center is the platform's cloud-native security posture management (CSPM) service. It provides centralized infrastructure security management for workloads hosted in Azure and on-premises infrastructure. Azure Security Center monitors deployments against best practices, and any misconfigurations are flagged for remediation.
Azure Firewall is a managed firewall service for Azure workloads. Built on Azure infrastructure, it's capable of scaling to cloud-level traffic. Teams can use it for the central configuration of rules across networks to allow only legitimate traffic.
Azure Sentinel is Azure native SIEM. Of course, built on Azure infrastructure, it can ingest telemetry data from multiple sources for analysis and threat detection at a massive scale. Data sources can be Azure's or hosted in other cloud platforms or on-premises. Numerous connectors are available for streaming the telemetry data.
Azure Web Application Firewall provides centralized protection from known vulnerabilities. Known threats are centrally patched and updated at the WAF level. Acting in a centralized way leaves attackers little time to exploit known vulnerabilities. Also, centralization avoids the burden of individually mitigating vulnerabilities.
Google Cloud Platform
Security Command Center is Google Cloud Platform's (GCP) native CSPM solution. It provides a single-pane view of the security status of your workloads hosted in GCP.
Web Security Scanner is GCP's WAF. It protects your web apps hosted in GCP (GKE, Compute Engine, and App Engine) from known vulnerabilities.
GCP's Cloud Armor service protects from specific cloud-based attacks such as organized volumetrics DDoS attacks or behind load balancers like SQL injection, remote file inclusion, or remote code execution.
Chronicle Detect is GCP's SIEM. It helps detect threat patterns at scale by ingesting logs from multiple GCP resources. It applies a standard data model across the ingesting telemetry and then can apply detection rules, no matter the massive amount of data.
AWS
AWS IAM enables ITOps to create users and roles with permissions to specific resources in the AWS environment. IAM works on Zero Trust principles and always assigns the least privilege permissions to users and roles that ultimately minimize the impact of a breach. It also supports multi-factor authentication and single sign-on (SSO).
Amazon GuardDuty comes on top of numerous AWS services (Cloudtrail, VPC, S3, DNS logs) to leverage machine learning to detect malicious activity in your environment.
Amazon Macie discovers and protects sensitive data such as personally identifiable information or personal health information stored in S3 buckets.
AWS Config records and continuously evaluates AWS resource configuration and keeps a historical record of all changes to resources.
AWS CloudTrail tracks all activity in your environment (executions in AWS console or API calls).
AWS Security Hub is a dashboard that combines information from the above services in a unified view.
AWS Shield is a fully-managed DDoS protection service and is enabled by default.
AWS Web Application Firewall like the ones mentioned above in Azure or GCP.
AWS Secrets Manager is a service that stores and retrieves sensitive information such as database credentials, certificates, and tokens.
As we saw, and it's a non-exhaustive list, CSPs offer quite a long set of services in their ecosystem. Even though CSPs offer so many services, data breaches do still occur. Why? When we look at data breach reports, most of the breaches reported result from a misunderstood responsibility share between the CSP and the customer or customer misconfiguration of the security tools provided.
Besides this, in 2021, the causes of 5,250 confirmed data breaches make virtually no mention of cloud service provider failure. Most of the breaches resulted from stolen credentials.
This circles back to what we were saying at the beginning of this paper. Analysts have a hard time deciphering attacks in this increasingly complex environment. They lack communication and need a way to centralize all these dataflows to create unified processes across the environment, no matter its fragmentation across on-premise, public/private cloud, or multi-cloud. This is where the SOAR comes in as a glue to bring coherence.
Next-gen SOARs are building the bridge between cloud-native controls and traditional security tools
Year on year, the need for automation and orchestration tools has increased. This trend is likely to continue as the need for speed and efficiency is fostered by further (multi) cloud adoption. In this regard, automation and orchestration capabilities help teams keep pace with the changing services offered and a centralized platform to manage tools and services used across different cloud environments.
SOARs are, by essence, the answer to complex and fragmented environments.
SOAR aims to bring together people, processes, and technology to manage incident response proactively, streamline operations, and improve SecOps effectiveness. These capabilities allow security teams to collaborate consistently, automate actions, and build incident response plans.
We've already demonstrated that SOARs are the go-to solution for teams dealing with extensive IT and SecOps solutions stack because of their unique ability to centralize the workflows between these tools. These capabilities are even more flagrant when implemented into broader hybrid, multi-cloud environments.
SOAR is even more essential when you talk about security in the cloud. Either if you consider a unique cloud or a multi-cloud environment, the SOAR shows its ability to support an exponentially growing set of integrations to enable your teams to work seamlessly with traditional security and cloud security services.
By linking cloud security services to their internal security layers, your analysts can pull in information coming from every location and connect the different security and IT layers to create a global and coherent security architecture from a centralized standpoint.
We've seen all of the services that CSPs are providing today. Because more and more companies are choosing to build multi-cloud strategies, you have to consider the potential lack of awareness between your different environments that could result in more fragmented processes, which are already challenging and, ultimately, vulnerable cloud security.
So, you're looking for an agnostic platform, free to integrate services from all of the CSPs on the market to provide an integrated experience, no matter your environment.
From the centralized platform, SecOps and ITOps can leverage orchestration and automation across existing tools, bridging cloud-native CSPs services and your own and helping you alleviate the "pain of glass."
Whatsmore is the unique case management capabilities of the SOAR platform. SecOps and ITOps can create end-to-end incident response plans from a centralized location. Across every environment, your teams can manage incidents simultaneously and store data and artifacts in a standard format. This dramatically simplifies investigations across hybrid, multi-cloud environments and reduces the duplication nightmare for SecOps.
Next-generation SOARs
Facts first, first-generation SOARs lacked practicality. They were tools made by pros for pros. Operating them was as challenging and time-consuming as any other tool. They thus haven't delivered the expected value to the broad industry.
Next-generation SOARs are tackling this by focusing on building actual automation platforms. They embrace the concept of the process-agnostic tool, where integrations capacities and operating-skills barriers are motos. The vision is to build backbones. It is an easy-to-use platform, relying on an extensive catalog of integrated services, where everyone can orchestrate tools and automate their processes, starting with SecOps and ITOps.
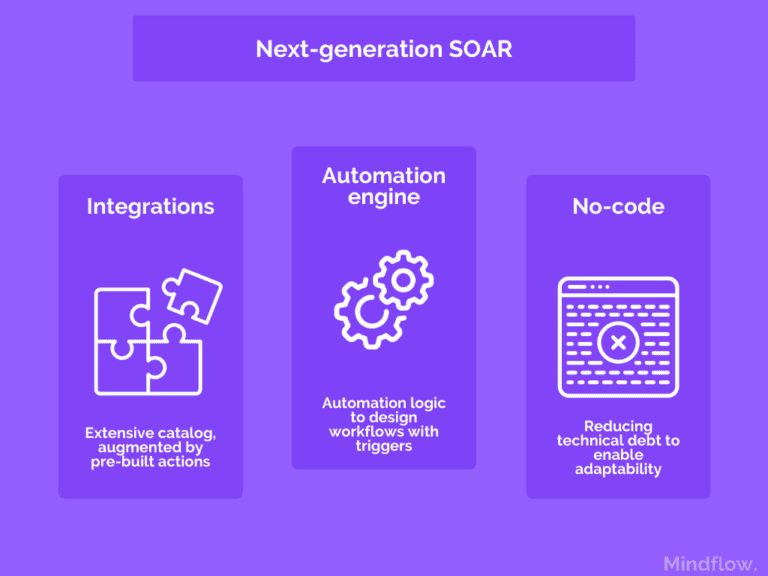
Among these platforms, Mindflow is leading. Today, it's one of the platforms that can provide integrated cloud security services for all the major CSPs on the market, AWS, Azure, and GCP. SecOps and ITOps can manage processes from a unified standpoint that overlaps the fragmented environment. Assing a no-code layer also helps build a hyper-automation enabling tool to continuously and consistently orchestrate and automate processes across public and multi-cloud environments to ensure security in the cloud.








