Today’s security begins with identity and ends with data.
Security strategies implemented numerous technologies and frameworks to keep your data safe, notably Identity Access Management (IAM) and Privileges Access Management (PAM) that are themself part of the broader Zero Trust Architecture. IAM PAM: two essential tools to keep your company safe in this environment.
As the enterprise’s perimeter is changing, access control needs to change. The enterprise is becoming distributed across multiple locations as remote work and cloud hosting are the norm. Thus the former environment and its established controls are gone. Controls must be implemented directly at your endpoints, at the identity level. Should incidents arise, you have to answer near real-time to avoid intrusion. Automation becomes critical to allow you to implement such processes.
However, as good as these solutions are, implementing them across the whole company and leveraging their maximum potential has proven challenging.
Below we’re going to look at how you can solve these issues with the help of a SOAR.
- How does IAM work with SOAR
- How can you leverage the SOAR with PAM
- IAM, PAM, and SOAR for automated and real-time access controls
How does IAM work with SOAR
For most companies today, data is one of the most valuable assets they have, if not the most. The modern organization’s capital relies on immaterial assets, such as R&D processes, that help differentiate the company from its peer competitors. Should initial access be granted to the wrong person and it could lead to the theft or exploitation of these precious data, in the end, leading to a dramatic loss of future revenues.
Being able to safeguard these data is thus critical. In response, information technology (IT) and security teams started to adopt frameworks to manage and control employees’ access to the information system that was in place.
To that end, we could describe the objectives of IAM like so:
- identification and authentication of individuals
- the roles in your information system and their assignation to each of the individuals
- adding, removing, and updating individuals and their roles
In a nutshell, IAM is about validating your identity before you’re authorized to enter a system. It differs from PAM, which is about resources access validation and relies on attributes. PAM and IAM are intrinsically tightened together, and often, solutions that provide IAM provide PAM.
However, they answer two different stages of attacks: initial access and privileges escalation. We need to adopt two different response plans for these two different threats. That’s why we’re choosing to analyze first IAM and then PAM.
Back at IAM. To fulfill the objectives listed above, IAM gathers numerous technologies, such as single-on systems, two-factor authentication, multifactor authentication, and the ability to store all the data used by these technologies securely.
But, as the attack surface grows by the number of users needing access to the information systems and varies according to employees’ whereabouts, there’s the need to close the gaps as fast as possible in an increasingly hostile environment. Manual IAM, relying on human inputs, needs to evolve towards automated processes to achieve real-time protection and reduce the risks induced by variations in the attack surface.
On top of that, tasks such as creating, suspending, or revoking employee access are grunt work taking time and prone to errors and omissions. When it comes to repetitive tasks, the main challenge is consistency. Take the classic example of an employee leaving the company. Depending on the employee, their access needs to be entirely revoked in hours or even minutes. The challenge isn’t about revoking all the access but ensuring that there isn’t any omission. Here, companies have put a controls framework in place to ensure that the human assigned to this mission. Still, automation is a way to conduct the task first and then allow complete auditability of tasks undertaken in minutes.
What’s more, implementing MFA everywhere isn’t sufficient per se. If you’re going to implement MFA everywhere, you need to implement real-time and automated controls; otherwise, end-users could ignore the notif or, worse, accept them to eliminate the disturbance. But real-time controls should not come as a burden to end-users or else. Acceptance on their behalf would be reduced… It has to be user-friendly. Talking about resolving to square the circle!
From a SOC perspective, when an incident arises, you have to be able to react fast to acknowledge the legitimacy of the action or not and act accordingly. Here, we’re talking about incident response capabilities which rely on the ability to rapidly leverage your other tools to gather information about the incident that’s taking place: MFA in place, which user, the scope, the devices affected. Collaboration between tools is crucial.
The SOAR shows its unique ability to be your SOC backbone when discussing collaboration and incident response. Integrating your technologies, it enables real-time collaboration between them. This way, it can gather information across your environment (your SIEM and EDR, or even your Cloud management techs) and beyond (further enriching your alerts with Threat Intelligence) and process it in pre-built playbooks where each response determines further actions taken.
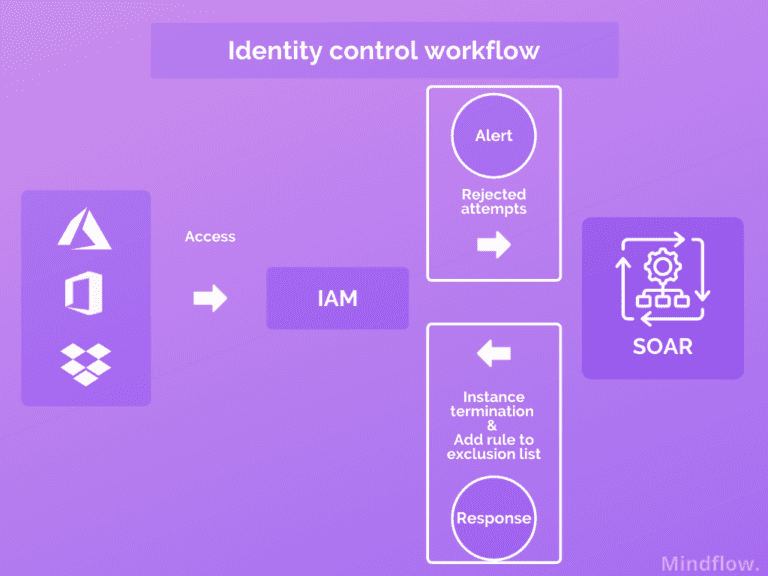
This way alerts received from IAM trigger playbooks that first enrich them to determine whether the alert should be deemed malicious and automatically take action.
As a result, the protection on behalf of the end-user accounts is increased, and your IAM processes are backed by automated incident response plans that secure your attack surface in real-time, proactively, and reactively.
How can you leverage the SOAR with your PAM solution
Attacks reports show an increasing reliance on credentials to access your information system. The recurring stages of these attacks could be described according to three stages: Steal, Escalate, Abuse. We’ve already covered Steal above by talking about IAM and what the SOAR can bring to it.
Here we’ll focus on escalation and abuse, which would resort to PAM, even though, in practice, IAM and PAM are often intertwined, as we said at the beginning of our demonstration.
In practice, PAM needs the integration of diverse technologies, often provided by various solutions. Let’s take a look at a PAM lifecycle representation. We see that, among others, PAM, to be effective, relies on techs such as 2FA or SSO but also ticketing systems, reporting, log monitoring solutions, and AD/LDAP.
These various techs represent different layers of security that your SecOps teams need to articulate together to make PAM genuinely effective. Most of the time, SecOps are doing this manually, navigating from alerts received via their Threat Intelligence feeds or highlighted by their custom queries on their SIEM to pinpoint remediation solutions. As a result, processes take time and leave holes in the security perimeter.
Of course, PAM solutions provide sets of out-of-the-box automation use cases. However, one-size-doesn’t-fits-all. Customers often need to do a lot of manual work to make their PAM efficient in their environment. Resorting to in-house automation is time-consuming and takes a lot of resources, skilled programers for tasks that could be easily automated due to their repetitiveness.
Finally, even though some PAM solutions provide integrations to top-of-the-art pinpoint techs like SIEMs or others, the automation of in and outflows between the two solutions.
Privilege access request workflows
About the highest risk server or application and the means to secure them. Even if I have legitimate permission and want to access these servers, request control is critical whether it’s necessary at that time to do the activity on the server.
With PAM, the processes were dramatically shortened. Login, notification, all via an electronic procedure. But it’s hard to implement and time-consuming you need to wait for a manager for the request approval. Thus customers avoid it or use another means of communication with the IT teams, which may be less secure.
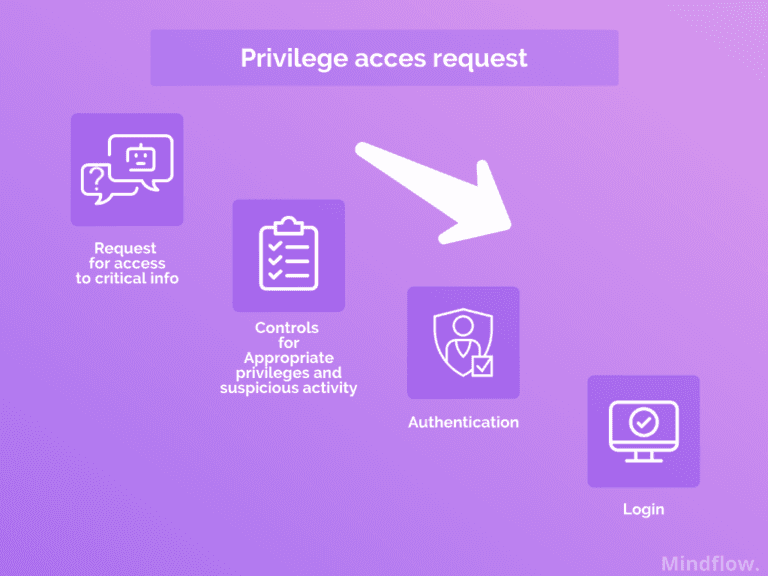
With a SOAR, you can build an automatic workflow where a user would submit a request before a Chatbot to approve the access request on one designed communication system, with the help of an authentication system requiring OTP.
Monitor privileged accounts and threat detection
A Backdoor account is created on the Active Directory. With most modern PAM, you can regularly detect these newly created accounts by scanning to auto-provision and reset credentials. However, you would prefer having a trigger-based workflow, automatically reacting at the exact moment of the account creation.
The event of creating the backdoor account will be detected by PAM tool, but what about other tools? SIEM ingests all the raw data, and what do you do with these? is there collaboration with other solutions?
With the SOAR, you will take advantage of your other solutions, such as the SIEM, which ingests all the logs and, most likely, syslogs attesting the creation of a new user on your Active Directory.
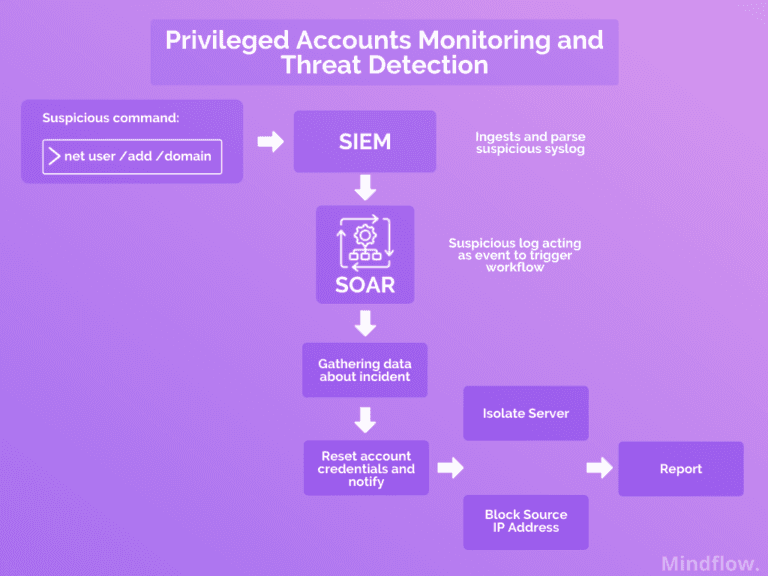
The command executing this creation can be highlighted as the trigger of your workflow to bring remediation actions with the help of other tools such as blocking the Source IP address or resetting associated credentials and notifying the analyst in charge.
IAM PAM and SOAR: Collaboration across all your security layers
Across all these use cases, we’ve seen that the value-added brought by the SOAR is about enabling automated and real-time controls between your security solutions. The SOAR harnesses its ability to integrate your environment and orchestrate the flows between them. This way, it enables you to ingest alerts and automatically apply your incident response workflows.
