Nov 13, 2023
Jean-Baptiste
Joly
Introduction
Today, a code hosting platform for version control and collaboration like GitHub has become a central component for any enterprise. It's where a company's intellectual capital resides. Therefore, it becomes critical for a company and its security team to ensure that the platform is configured correctly and securely, as failure could lead to many potentially damaging consequences. These consequences may include data breaches, unauthorized access to sensitive information, code vulnerabilities, compliance violations, reputational damage, and disruptions to software development workflows. A poorly configured GitHub can expose the organization to significant security risks and hinder its ability to collaborate efficiently and maintain the trust of its stakeholders. To achieve this, they can generate alerts using GitHub WebHooks. However, manually managing these alerts can be time-consuming and error-prone. In this article, we'll explore how to automate the treatment of GitHub WebHook alerts using Slack and Mindflow.
Why Automate GitHub Webhook Alerts
GitHub WebHooks are essential for informing teams about critical events such as code commits, pull requests, and security vulnerabilities. However, as the volume of events increases, manually tracking and responding to alerts can overwhelm even the most skilled security teams. Automation offers several advantages:
Speed and Efficiency: Automation allows for near-instantaneous alert handling, reducing response times and minimizing the risk of delayed actions.
Consistency: Automated workflows ensure that every alert is treated consistently, reducing the likelihood of human error.
Scalability: As the number of GitHub events grows, automation scales effortlessly, adapting to the increasing workload.
Resource Optimization: Security teams can focus on more complex tasks while repetitive and routine actions are handled automatically.
Prerequisites:
To implement this automation, you'll need the following:
A GitHub account with administrative access to the organization you want to monitor.
A Slack workspace with admin privileges to configure integrations. Fill in your workspace ID in this URL
https://api.slack.com/apps/YOUR_WORKSPACE_ID/oauth?and ensure the Bot scopechat:writeis granted.A Mindflow platform.
Steps to Automate GitHub Webhook Alerts Handling:
Step 1: Configure GitHub Webhooks
In your GitHub organization, go to "Settings" > "Webhooks" > "Add webhook."
Set the Payload URL to the endpoint provided by Mindflow. You can find this information in the Triggers tab of your workflow's settings.
Select the events for which you want to trigger alerts, such as "push," "pull_request," or "vulnerability_alert." You can find the GitHub documentation on this subject here
Save the webhook.
Step 2: Set Up Mindflow
Configure the GitHub integration
Create your new credentials for GitHub in the Vault :
Service: GitHub v3 REST API
Credential type: HTTP API Key
Key: Authorization
Value: Paste your private key you retrieved in GitHub
Step 3: Create your playbook
With this first flow, we'll see how we can automate the processing of the alert we receive when a public repository is created or a repository becomes public.
Trigger: When a new repository becomes public, GitHub will send a webhook to our Mindflow workflow.
First, we'll need to know who performed the action. To do this, we can use GitHub integration to retrieve the information. In this case, we'll pick the information we're interested in, the GitHub login in the webhook, and use it on the step Get a user.
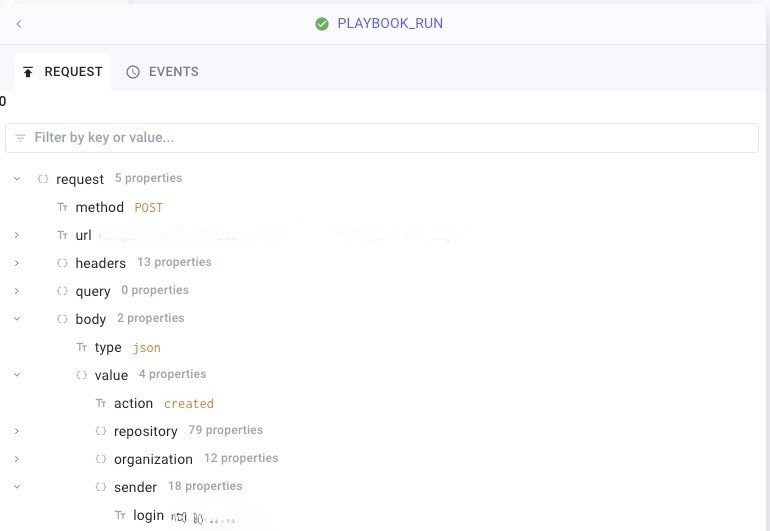
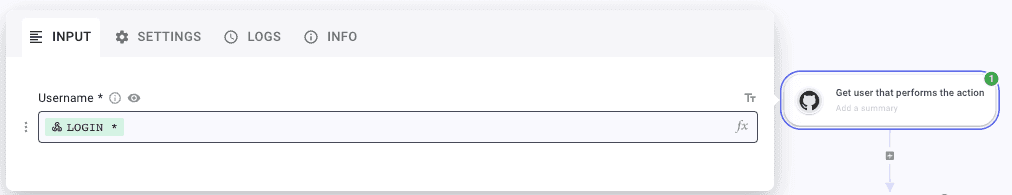
In response, we gathered a lot of interesting information, such as the name, the company they work for, their email address, etc. With this knowledge of the action initiator, we can dispatch a Slack message to the security team, enabling them to address the alert promptly.
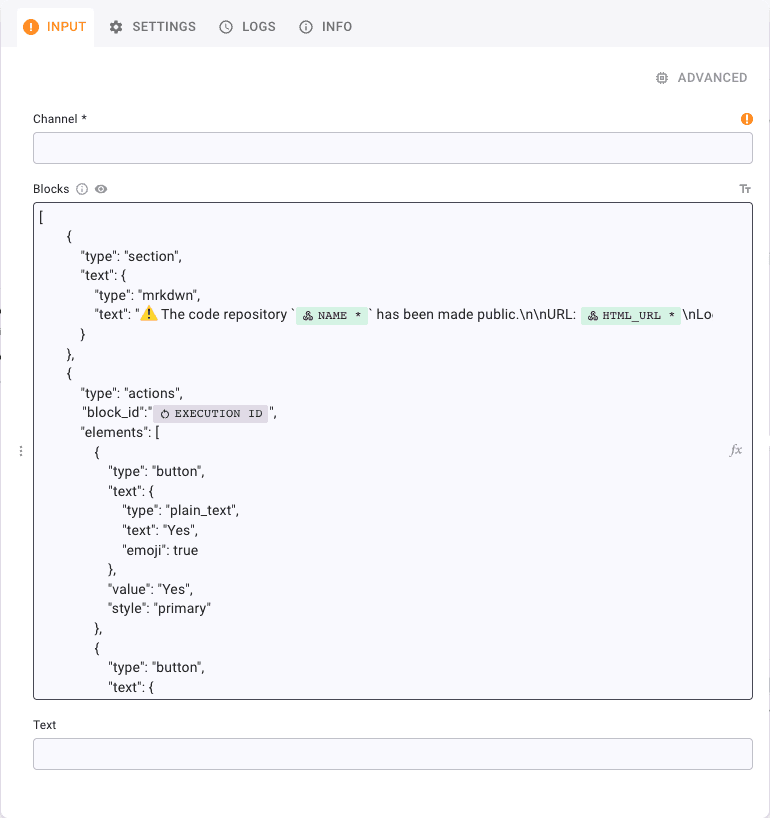
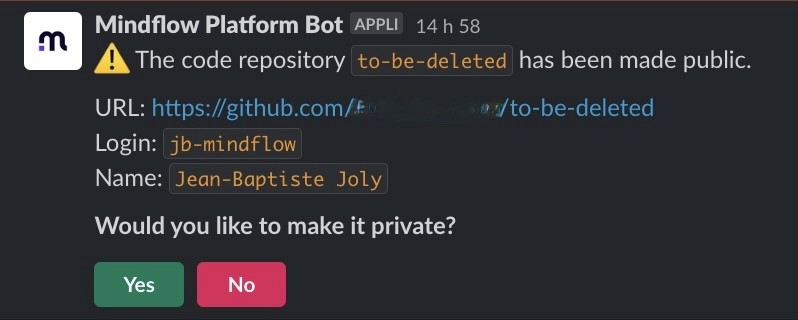
An essential parameter to highlight within the Slack step is "block_id": "EXECUTION ID". This parameter plays a pivotal role in retrieving the user's selection.
This enables us to establish a conditional step and define a branch named Yes, which will initiate the GitHub API call to switch the repository to private. The workflow will go into a waiting state until the user selects which action they want to take.
To accomplish this, we have two options: either utilize the GitHub integration, as demonstrated earlier, or employ an HTTP request. We will opt for the latter to showcase an alternative approach within Mindflow.
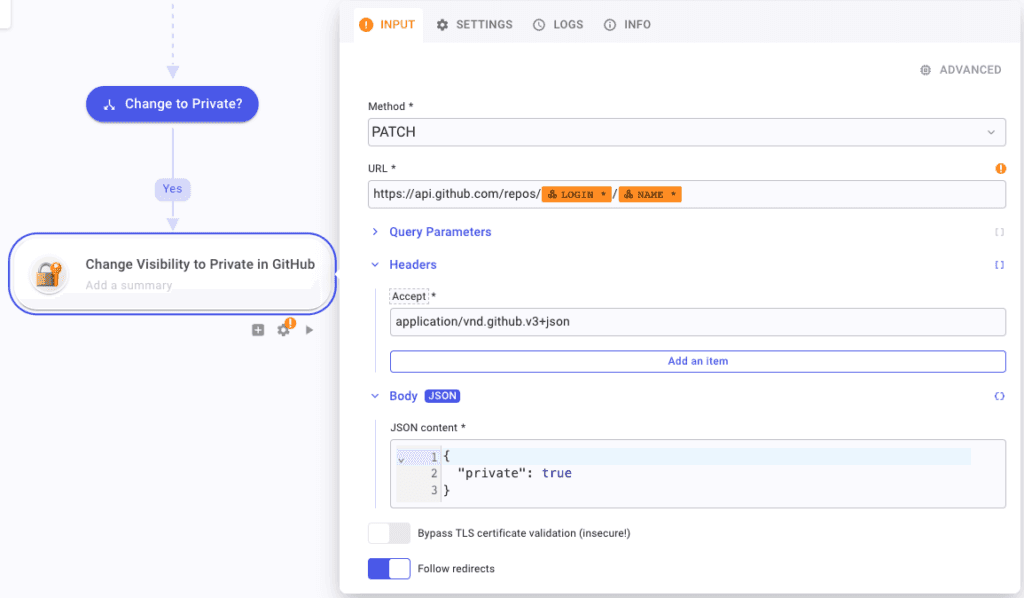
We will create an HTTP Request step, which we'll configure as follows:
Method: Patch
URL:
https://api.github.com/repos/[$LOGIN]/[$NAME]
$LOGINand$NAMEare two parameters to be picked from the GitHub WebHook
In the Headers :
Accept:
application/vnd.github.v3+json
In Body, create a JSON content with the following content :
{
"private": true
}
You can add many other things to suit your needs in the Body. It's always a good idea to check out the API documentation to see what's possible.
Voilà, you have a first workflow to monitor your GitHub repositories and make sure they're private!
Now, you can unleash your creativity to expand this workflow and include any events you wish to capture using webhooks. Consider scenarios such as adding a new member to your organization, deleting or creating a new repository, generating a new security alert, and more.