Sep 28, 2023
Aditya
Gaur
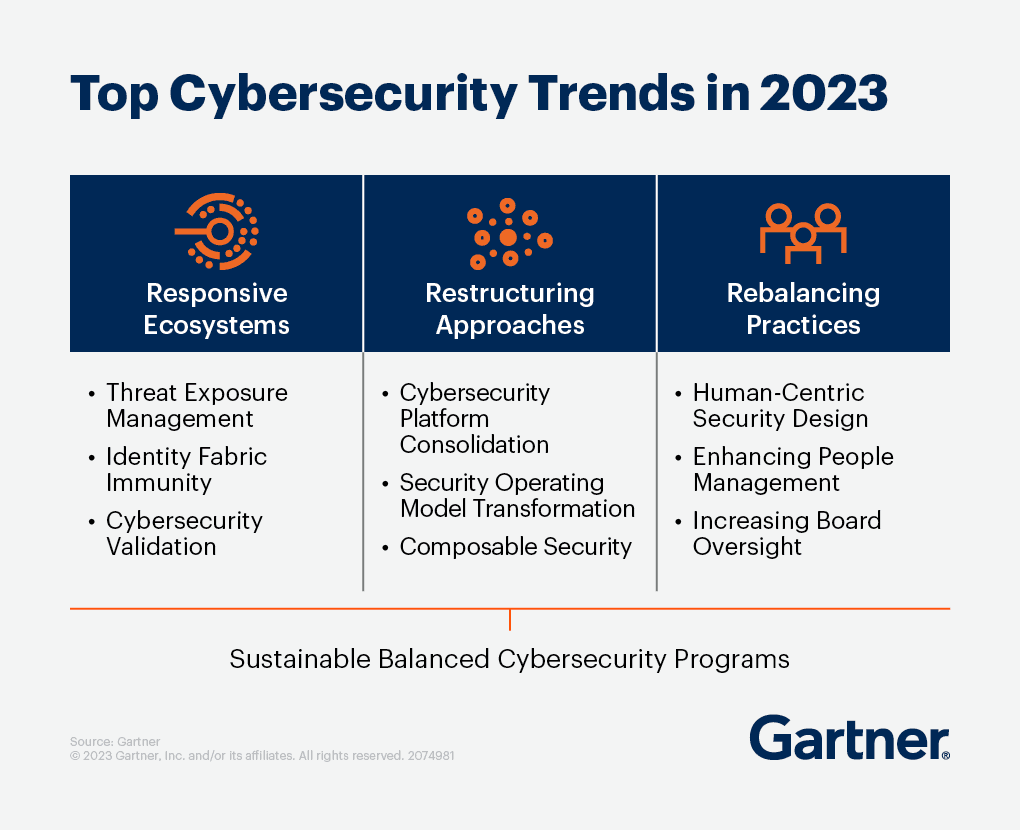
In today's interconnected world, cybersecurity's importance cannot be overstated. As organizations evolve and become more complex, so do the threats they face. Gartner identified the top cybersecurity trends in 2023, underscoring one critical trend—the Human-Centric Security Design. But what does it mean to have a human-centric approach to cybersecurity?
A human-centric approach places the employees and leaders at the heart of an organization's security strategy and posture. It emphasizes reducing cybersecurity-induced friction and enhancing control adoption by considering the needs, behaviors, and preferences of the people involved.
Deep Dive into Human-Centric Security Design
The Human-Centric Security Design trend identified by Gartner emphasizes that cybersecurity strategies should be designed with people in mind. Most cybersecurity programs and systems fail because they're built around tools and metrics instead of people. People make the core of any organization's security posture.
The employees are the first line of defense. In most cases, this first line of defense doesn't even know about its important role in ensuring security for the organization. The human-centric approach argues that when security measures consider user experiences, they're more likely to be adopted and less likely to be ignored.
Strict security controls can often create friction, leading to employee frustration and potential non-compliance with the organization's security guidelines. Human-centric design aims to minimize this friction. This approach can lead to more robust security, improved user experiences, and higher employee retention.
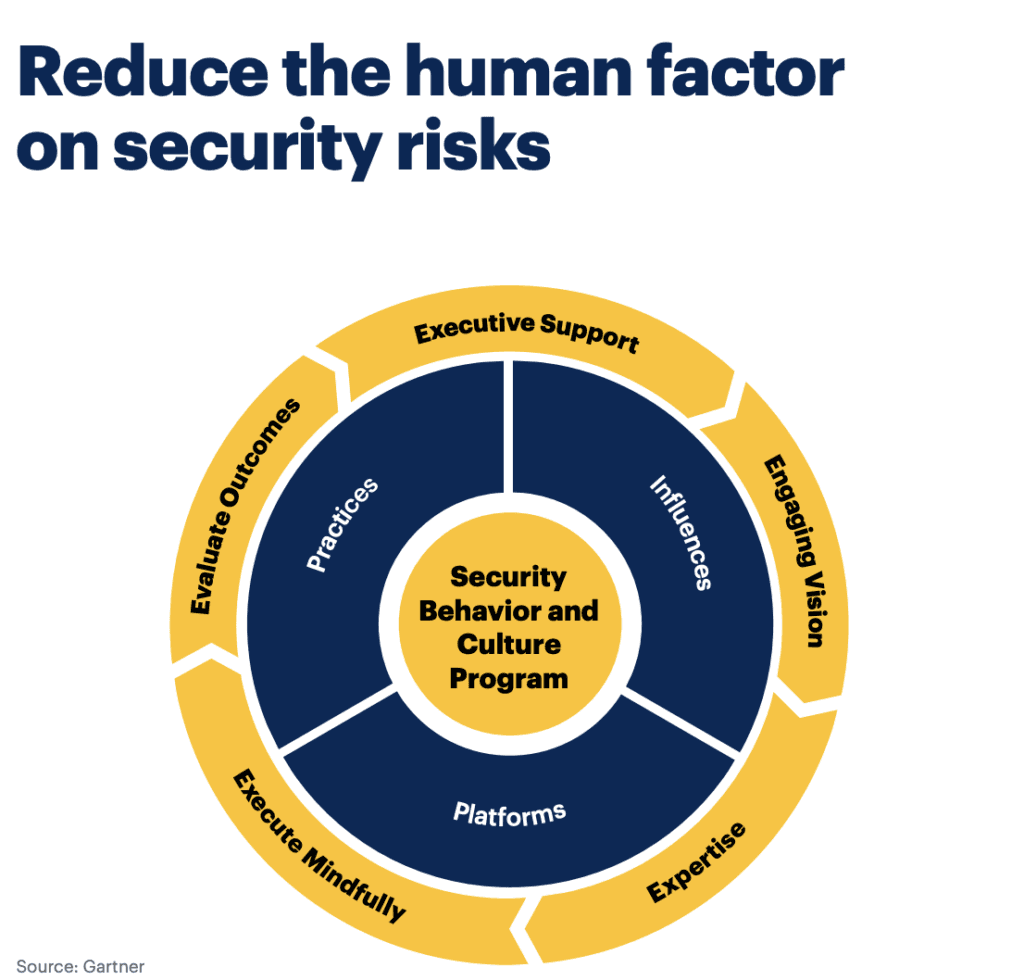
“A human-centered approach to cybersecurity is essential to reduce security failures. Focusing on people in control design and implementation, as well as through business communications and cybersecurity talent management, will help to improve business-risk decisions and cybersecurity staff retention.” —Richard Addiscott, Sr Director Analyst at Gartner.
Current State of Organizations and Security Failures
Today, organizations face significant security challenges, which are expected to become increasingly complex as adversaries integrate AI into their deceptive techniques.
Despite adopting sophisticated solutions from the best vendors, security and data breaches continue exploiting minor loopholes in security postures. Key cybersecurity challenges, such as alert fatigue, workforce shortages, skills gaps, and social engineering, significantly contribute to security failures. None are due to the lack of robust tools—they're all about humans.
Alert Fatigue, for instance, highlights the overload of alerts and inadequate processes to manage them. This can lead to security analysts being desensitized, leading to ignored or missed accurate alerts. Conversely, the same analysts often end up reporting and targeting false positives. This desensitization problem isn't about the unmanageable influx of signs but the faulty design of security systems, which often overlook the human element.
Staffing shortages and skills gaps in cybersecurity are becoming increasingly chronic. Cybersecurity professionals have always been scarce for organizations, but the talent vs. demand gap is widening. Today, understaffed and ill-equipped security and SOC teams face tens of thousands of alerts daily while team sizes continue to shrink. Organizations must address this critical issue by upskilling existing staff and creating a supportive work environment and security strategy.
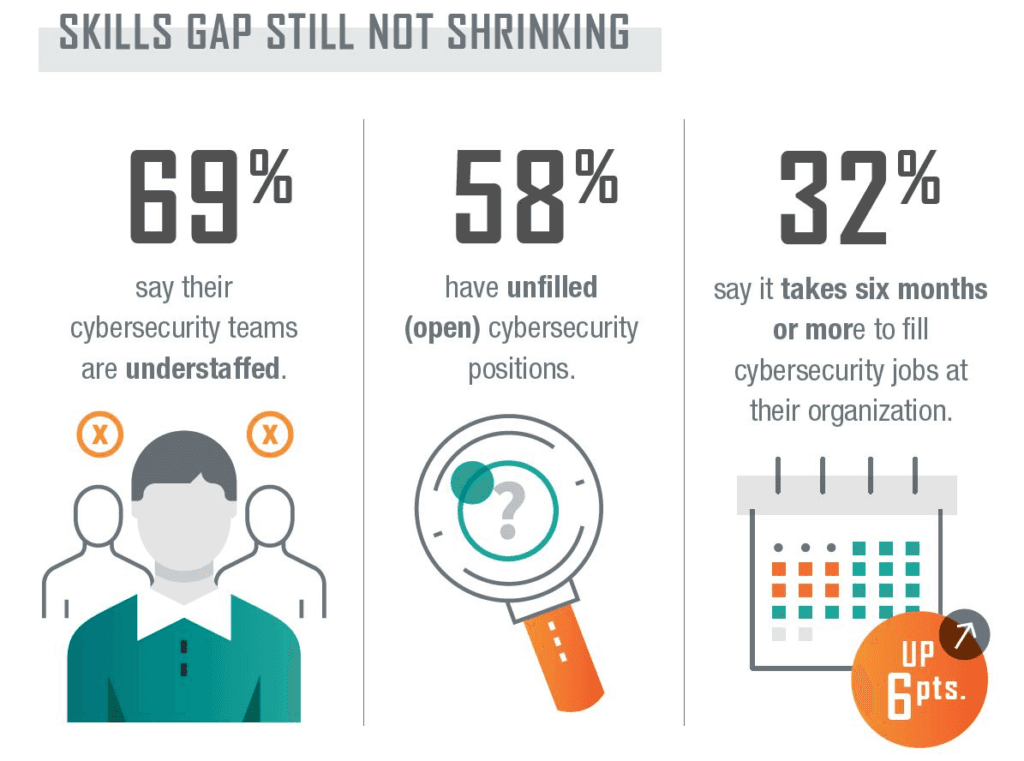
Source: SkillsTx
The retention issue calls for a similar shift towards a human-centric approach. Most cybersecurity professionals cite high workloads as a primary reason for leaving their role. Organizations must design jobs and work environments around humans and objectives or tools.
By ignoring the human aspect, organizations fail to address a fundamental security component - user and employee behavior. The current paradigm of security design can lead to vulnerabilities borne out of human error —both in strategizing and implementation.
It's all about humans.
The Resurgence of the Human-Centric Approach
The notion of a human-centric approach to security isn't a shiny, brand-new idea. The concept has been around for a while, but with the threat landscape changing continuously, the emphasis is back on humans. Over the years, we have conceptualized and established products, tools, frameworks, and ideas to combat any possible cyber threat. Yet, the damage inflicted by these threats continues to rise. The only thing that hasn't changed or adapted to this evolving cybersecurity paradigm is humans.
The human-centric approach not only portrays humans as the primary defense force against cyber threats but also ideates an environment and a framework adapted to work for humans without creating overbearing workloads.
Implementing a Human-Centric Approach to Cybersecurity
According to Gartner's report, there are several key ways that organizations can adopt a human-centric approach to cybersecurity.
To begin with, we need to move towards human-centric security design. This means emphasizing employees' experience interacting with security controls. According to Gartner research, by 2027, more than 50% of CISOs in large enterprises will have embraced this human-focused approach within their teams. So, how can your company prepare to implement human-centric cybersecurity design today?
1. Driving Secure Employee Behaviors
Employees still engage knowingly in recognized risky security practices, such as using the same password across multiple accounts and opening links in emails from unknown sources. This showcases that human behavior is a significant challenge to organizations of any size. It's essential to recognize that raising employee awareness is not the end solution to the human factor in cybersecurity; organizations must go further.
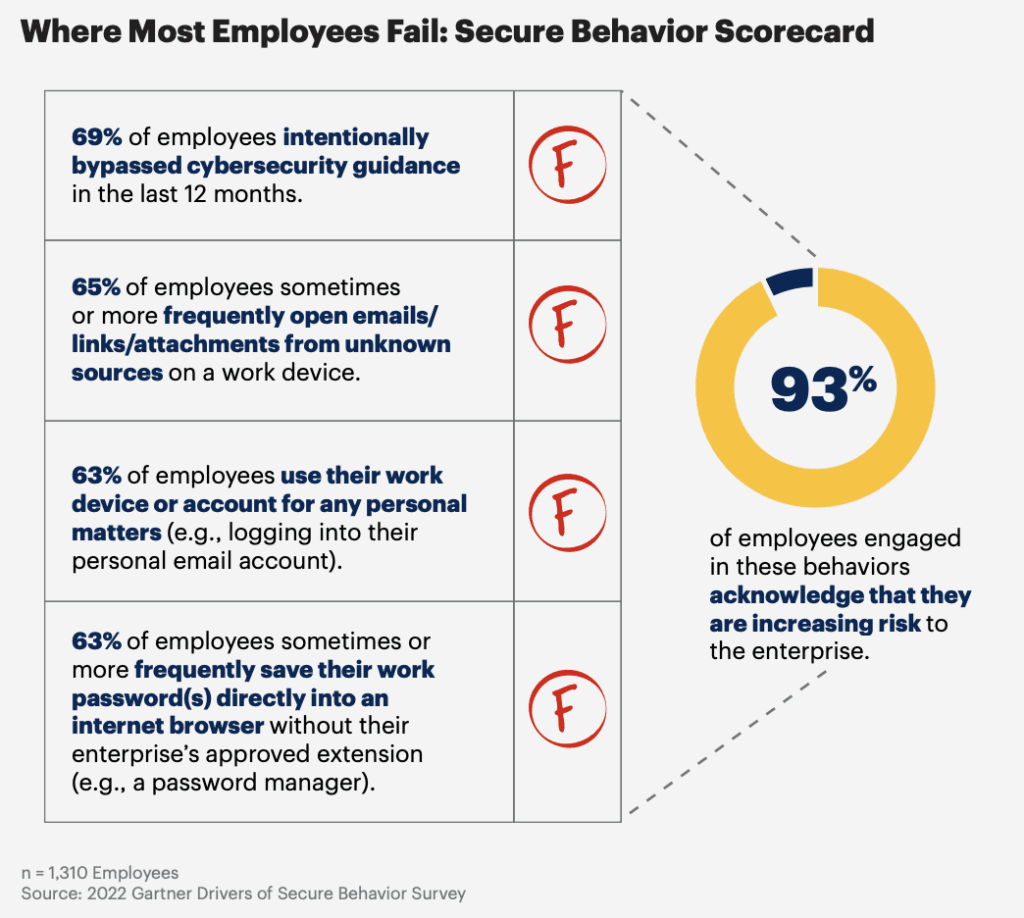
Source: Gartner 2022 Drivers of Secure Behavior Survey
2. Rescope Security Programs:
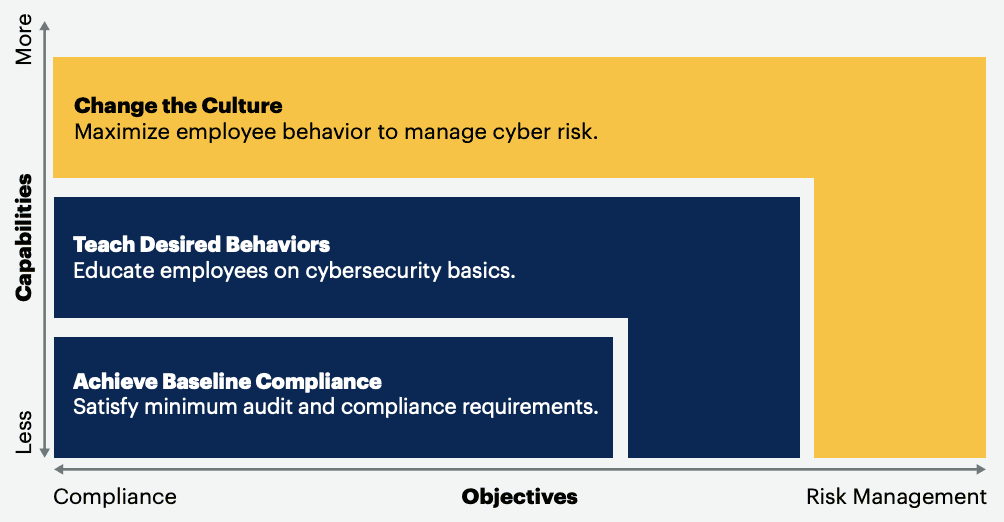
Organizations and security leaders should redesign internal cybersecurity awareness programs instead of focusing on baseline compliance. These new and flexible programs should be optimized for human behaviors instead of solely focusing on technical capabilities and performance metrics.
Here's how organizations can achieve this:
Achieve baseline compliance:
Included capabilities: Training modules and learning management system (LMS) platform integration with tools and practices implemented by the organization.
Sample metrics: Training completion rates, Drop-off points
Teach desired behaviors:
Included capabilities: Mock phishing simulations, human risk scoring, content, and resources to educate on other human-enable cyber threats such as social engineering.
Sample metrics: Click rates, Open rates, Report rates
Change the culture
Included capabilities: Automation and orchestration is a simple yet graceful answer to a majority of security challenges faced by digital organizations
Sample metrics: Actual detected attacks from users, number of workflows automated
3. Cybersecurity Controls-UX Integration:
Cybersecurity tools and platforms are often tricky to use and navigate in their current form, creating friction in implementing the most basic security practices. Security controls should make UX design more functional and intuitive when centered around human behavior. No security tool should require extensive documentation to get started. Instead, it should just make sense to the user.
Here's how organizations can achieve this:
Identify sources of friction by establishing friction-sensing mechanisms to identify the bottlenecks in implementing security practices.
Review and remove controls that no longer add value. For example, if an organization decides to automate its workflows through Mindflow, Mindflow naturally evolves into becoming the central hub of managing all its security workflows. This removes the need to use security controls on individual products.
4. Role and Scenario-relevant Cybersecurity Learning Experiences:
Most organizations today have security awareness and learning paths for all their employees. However, almost all these programs are generalized and built for a general audience. In a world where cyber threats are becoming increasingly targeted and specific, organizations must adopt the same approach by providing learning opportunities for particular scenarios relevant to their jobs. For example, a salesperson often receives more emails than a security analyst, so they should receive more context to help them better identify threats such as phishing and social engineering.
Here's how organizations can achieve this:
Organizations must tailor prompts and scenarios to situations employees experience in their roles to prepare them better to make the right decisions.
Include more than one "right" answer, reflecting real-world scenarios that are rarely binary. Cybersecurity training modules often present binary strategies to employees, which is hardly the case in real life—they should represent ambiguity.
Human-Centric Cybersecurity Automation with Mindflow
Mindflow is built on these principles —keeping humans at the center stage while ensuring seamless integration of systems and frameworks in any organization through its extensive integration library. Security tools aren't designed to work together; they're built to be secure and siloed from external noise, data, and connectors. Mindflow overcomes this hurdle by providing native integration capabilities to any security tool from any vendor.
In the dynamic realm of cybersecurity, the human element is crucial. The ongoing challenges—alert fatigue, staffing shortages, and the like—are fundamentally human issues, not just tool-related problems. Mindflow helps overcome these by automating the most time-intensive stages of security professionals' jobs. Mindflow does it all for detection, analysis, reporting, notification, and remediation.
Not only that, but unlike conventional security systems and tools, Mindflow is built to be intuitive, functional, and easy to use. This reduces the friction that leads to most security failures. Getting started with Mindflow is super easy, enabling enhanced security design that is even easier than existing strategies. The human-centric approach is about making security measures user-friendly and intuitive and fostering a culture where security awareness is integral —Mindflow is here to enable it.
So, let's get started.