Nov 17, 2021
Paul-Arthur
Jonville
When you're trying to secure access to your data and resources, passwords are your first line of defense. However, it often has some weak links. You have to create a secure password policy.
You would guess, "Come on, nowadays people are aware of this issue. I've been spending my time telling people to change theirs!". Well, let's talk about Botnet. Mirai is a malware that, at its best, infected almost 400k IoTs around the world. To that end, it scanned the internet for open Telnet ports, then attempted to log in predetermined credentials combinations.
That list must have been gigantic to allow Mirai to grow so big! Only 60 (and the 60th is a kind of "signature"). Yes, 60 were enough to breach almost half a million connected devices to build the most extended botnet network ever.
I know that bringing awareness to employees, particularly regarding their credentials, seems like a Sisyphean task. Still, someone has to do it because it has to be done and done correctly. No tool can replace that first line of defense!
That's why you have to:
First, explain to them what makes a good password, again;
Create a secure password policy in your company to control the enforcement.
A good password is fundamental to create a secure password policy
It's one mean of authentication, among others
There are different ways of authentication relying on different types of factors:
Knowledge factor: "Something I know";
Possessing factor: "Something I own";
Inherent factor: "Something I am."
Passwords falls into the first, the knowledge factor. To improve your security, you can choose to build a multifactor mechanism. In this case, you choose two factors or more. Even if an element of authentication is compromised, the attacker will need to compromise a second one to secure his access to your network.
Reminder: You have to choose two factors that are not of the same category to make it work. Otherwise, your multifactor system is vulnerable to the same kind of threat, making it easier for the attacker to breach since he would only have to take control of one factor to access the information needed.
In any case, adequately incorporated, a double authentication indeed brings benefits.
However, multifactor authentication is not to be mistaken with strong authentication. As we said, multifactor authentication relies on multiple categories of factors. These factors aren't necessarily strong per se (password associated with temporary code received by SMS, for instance).
Strong authentication relies on a cryptographic mechanism based on parameters and security that are deemed strong. For instance, a strong authentication depending on a knowledge factor is Kerberos; one relying on possessing factor is a certificate stored in a smartcard.
Of course, when determining the mean of authentication, you have first to assess the sensitivity of the data or role in question. Authentication segmentation is essential. Otherwise, you'd be going overkill and restraining productivity.
Now that we know that a password is one way of authentication, let's dive into what makes a good one.
How can I measure my password's robustness and improve it?
Having a password isn't sufficient to improve your security. Worse, a weak one can sometimes create false security sentiment. Typically, 1234 or it's variant. It's easily decipherable by any attacker. This is why robustness is crucial.
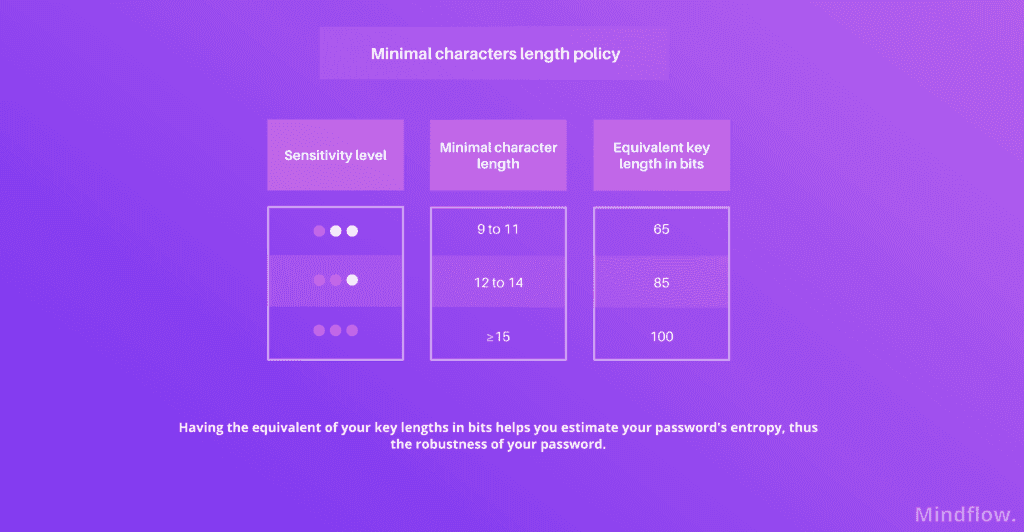
Robustness is calculated thanks to entropy. Entropy, expressed in bits, predicts how difficult it is to guess or brute-force. Two variables are considered when assessing entropy: the length and character set size.
Length is the most known metric to assess entropy. The longer it is, the better. Still, the main obstacle comes when it has to be memorized by a human being. Passwords longer than 20 characters are hard to remember; thus, the concept of passphrases, longer but not necessarily harder to remember.
Let's take an example. Ghuh!oKijjiD&?ddzpOB undeniably looks strong as a password. However, memorizing it would be a challenge, especially if it's the third one you have to memorize unless you're Sheldon Cooper. Hence, the passphrase. You could choose a passphrase that strikes your mind and is thus easier to remember. GameofThronesseason8wasterrible!, for instance. Longer than 20 characters but also quite easy to remember! Plus, no need to write it down to memorize it and end up showing it on TV...
Character set size is the other factor governing the entropy calculation. The wider the set size, the more complex your word/phrase is and the higher its entropy. To widen the character set, you can authorize the use of digits, lower and upper case distinction, and special characters. From 36 (digits and letters without consideration between lower and upper case), your character set size is now 70 and can even go up to 90! For instance:
Choosing a 12 characters length within a 90 character set size results in a password's entropy equivalent to 78-bits;
A 16 characters length within a 36 character set size (digits + alphabetical letters)is the equivalent of an 82-bits key.
However, adding special characters or digits to the character set size often means users replacing some letters with equivalents in numbers or special symbols. Typically, replacing o by 0 or i by 1. If you're encountering an online password attack, such small replacements can be lifesaving since attackers have to interact with the system and its possible limitations (authentication attempts, for example).
However, in an offline password attack, the attacker gets a hash of your password; he goes offline and tries to crack it. Here, the complexity of your password matters the most. Just replacing an o by a 0 in passw0rd is not going to slow the attacker down when he's brute-forcing your hash by trying every combination, variation, and iteration possible.
How can I create a secure password policy in my company?
Creating a secure password policy aims to find the equilibrium adapted to your company between numerous elements:
Category
Length
Complexity
Expiry date
Tries limitation
Robustness control
Means of conservation
Recovery of lost or steal
Password-safe
We've already seen two elements of the strategy : length and complexity, which determine entropy. However, entropy alone isn't enough to create a secure password policy. For instance, high entropy is useless if no attempts limitation is planned. An attacker can brute force it, the only limit being the network speed.
Let's dive into the remaining ones.
Password categories
There are three categories of passwords. Ones that need to be memorized and which cannot be easily managed by a safe. Usually, these are session or password-safe passwords. Just a handful of them, but they have to be memorized and strong enough because of their sensitivity (prone to be combined with a second authentication factor). The ones that are not necessarily memorized and can be created and stored by safes.
Last, you have personal identification numbers (PIN code). They're checked locally on a physical security component.
Expiry date
An expiry date is a good measure but often counterproductive. Users tend to create iterations (credential1 followed by credential2, for instance) or use trivial logic links. Attackers know this; They have dedicated dictionaries to cycle through every iteration/variation possible of this kind of password.
This choice also depends on the user's role and accesses sensitivity. An administrator account has more privileges and is thus more sensitive than a standard account. Imposing an expiry date on less sensible accounts can be counterproductive. However, for sensitive accounts, implementing such a policy can be productive.
Tries limitation
As said above, limiting logins attempts can be lifesaving. Combined with high entropy, it dramatically reduces the risk of successful online attacks.
Without such a mechanism, an attacker can breach using brute force. Keep in mind that secure encryption is theoretical. Any encryption method can be breached at some point. No attempts limitation allows infinite tries to the attacker who's likely to automate the process of trial and error and test at the bare minimum thousands per second. You don't want that. This is why tries limitation is one of the most recommended elements to create a secure password policy.
Robustness control
Being able to control the enforcement of your policy is crucial. You have to know if users can circumvent it. To that end, you need to control their creation according to predetermined rules.
Note that I said the creation. Controlling passwords once they're created implies extracting them and checking them in the clear, which makes an unacceptable vulnerability.
What kind of control should you ask? First, you could think of automated systems checking if passwords respect your policy. You can also create an automated comparison mechanism between the one submitted by the user and a most used password database, leaked data breach bases (haveibeenpwnd), or dictionaries used by attackers, like JohntheRipper.
Any control should also check for repetitive motives such as specific patterns (1234 or qwerty, for instance) or those containing personal information like date of birth or noun. If you choose to incorporate an expiration policy, you should also forbid iterations of old credentials.
Means of conservation
If your database is compromised, passwords stored in the clear are revealed. You thus need to keep the password's footprint instead of the password itself. To that end, you have to create a one-way encryption process. For such, consider using a hashing function (SHA-2 series, for example).
The footprint calculated with the same hashing function will always be the same. Attackers can then try to match passwords with the footprint. To avoid that risk, a hash table attack, you can add salt when calculating the footprint.
However, recommended hashing functions such as SHA-2 are fast to execute. Attackers can test numerous passwords at a rapid pace. When calculating the footprint, you can use memory-hard functions to slow them down to increase execution time and memory use.
Means of recovery of lost or stolen passwords
A user losing his/her credentials is inevitable. The same goes for stolen ones. To overcome this issue, you have to plan a recovery mechanism. The most used ones are sending a temporary password, a temporary link to reinitialize, and contacting IT support.
No method is perfect. Each has its pros and cons: receiving a code on your phone or receiving a link via email, for example. The use of a UEBA tool can bring benefits. A request from a user with an unknown IP address or an unusual location can be subject to further investigation before being granted access.
In any case, never should the password be transmitted in the clear.
Use of a password-safe
When possible, the use of a password-safe is recommended. It allows users to create high entropy passwords without the concern of memorizing them. Of course, the downside is the master password unlocking the password-safe. Since the data stored in the safe is sensitive, the master password has to be robust, thus harder to memorize. In any case, it reduces the credential to memorize down to one.
Final recommandations to create a secure password policy
Let's remind ourselves that we should use different credentials for each service we're using, especially between personal and professional ones. Doing this limits consequences if one of them is compromised.
Finally, password policy adds to the more general authentication policy, where you assess the sensitivity of the data or service accessed. According to this, you're combining the use of passwords or other authentication factors (something I own, something I am).







