Apr 20, 2022
Paul-Arthur
Jonville
More than ever, Security Operations (SecOps) are at the center of the cybersecurity field, if not the overall industry. SecOps defends your company at numerous critical entry points. They intervene in the governance, compliance, application, and development cycles, to name a few.
Your SecOps teams are up around the clock daily to ensure the adequate level of security your company needs. This is needed as the threats your company faces are becoming deadlier.
But not only because of the sheer aggressivity of attackers. The pandemic brought several disruptions, dramatically augmenting your company's attack surface. Companies worldwide had to adapt to a unique and unprecedented environment to survive. They turned en masse to the cloud to keep the company running as it became distributed worldwide to employees staying at home and working remotely.
This isn't to say that the cloud migration trend was nonexistent before the pandemic, but the administrative lockdowns dramatically boosted this trend. Attackers rapidly learned how to take advantage of it. Attacks grew sharply in 2020 and 2021, and their consequences as well. Their processes and technologies have evolved, and the cybercriminal economy is becoming more attractive than ever, although the pandemic is starting to be controlled in the North Hemisphere.
SecOps were and are still overly solicited to counter this increasing threat. They need to adapt to new threats instead of constantly evolving existing ones. The threats are becoming deadlier, and SecOps needs to be sharper than ever. To that end, the cybersecurity industry and professionals must consider modernizing their security operations.
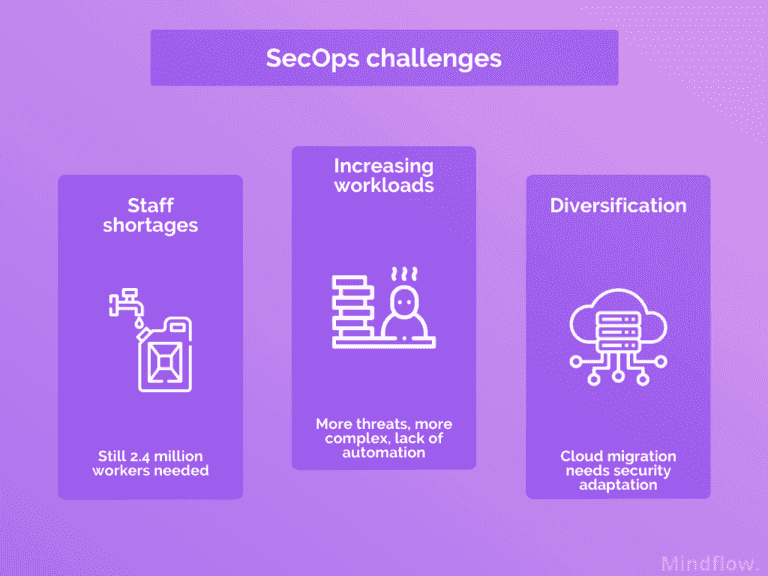
SecOps today are facing numerous challenges (shortages, complexity, technologies)
It requires a new approach powered by a Next-generation SOAR
SecOps today
SecOps relies on three resources: people, processes, and technologies to ensure their mission. According to their criticality, their objectives are to detect and respond to threats arising in their environment as quickly as possible.
To that end, SecOps are prone to evaluating their performance according to selected KPIs and KRIs, sometimes even presented to the board as legitimation factors, even though more and more CISOs try to present their work in a more actionable way.
Still, performance evaluation reflects the dynamics between the three core elements on which SecOps are built: personnel, processes, and technologies.
As the performance of a number of the critical metrics analyzed is deteriorating, answers will be found by examining the three elements.
People: shortage
Processes: complexity
Technologies: plethora of new ones piling up
These three elements are listed among the top 4 SecOps challenges security teams face in SANS's "Modernizing Security Operations" report. The top 3 include cost, a symptom of staffing, and technologies.
SecOps staff shortage
Even though the ISC documented a slight decrease in the cyber professionals' workforce gap, from 3.1 million to 2.4 in 2021, a structural gap still needs to be filled.
As we've documented in previous articles, the pathway to cybersecurity is highly heterogeneous. Most cyber professionals started in IT among older generations and then transitioned to cybersecurity. This isn't the case for younger generations, though. Although there's a higher percentage of cybersecurity education, a more significant part of young cyber professionals explored cybersecurity before being recruited for a job in this domain, meaning two things.
First, there's a structural lack of offering cybersecurity professionals specialists. Second, cybersecurity attracts a wide diversity of candidates, where most don't hold computer science graduation, although they have degrees in STEM fields.
As we've seen above, there have been important inflows of workers in the cybersecurity workforce in the last few years. More precisely, starting in 2019, the global workforce grew from 2,802,700 to 4,192,255 people in 2022, an 85% increase in just two years!
As a result, the workforce is relatively young. A significant part has an average experience between junior and mid-level. However, they often end up on the first line of defense. There, they're doing the most repetitive and low-value-added tasks. They also fill the ranks for more complex tasks on reduced frames of time that require extended shifts across nights, weekends, and holidays.
Thus, it induces high levels of stress while doing their jobs. This helps explain why the cybersecurity turnover rate is slightly above global averages, topping 20%. It also explains the reduced percentage of cybersecurity professionals with more than ten years of experience among SecOps teams. It all comes down to the organization's retention capacities, which reflect its ability to ease the stress and workloads burdening its employees' shoulders.
These factors are gathering into the global need for A. more people to join cybersecurity ranks B. better-prepared team members. SecOps members point out a need in surveys when they point at staffing and workforce as the top 1 reason for attacks.
Interestingly, phishing, visibility, and ransomware rely on executing highly repetitive actions by the same analysts. They're also among the most common incidents they've had to face these past couple of years. Still today, they're the biggest threats to their organizations.
SecOps increasing workloads
Even though the staffing shortages hinder SecOps, they still have to deal with increasing workloads, quantitatively and qualitatively.
A growing number of attacks
We've been reading everywhere for a couple of years now; cybersecurity has become a top priority for most companies worldwide. Because of the pandemic and its consequences on labor organizations, companies left critical surfaces uncovered. In most cases, millions of employees had to resort to remote work without any preparation. IT departments were forced to move workloads to the cloud regularly in days instead of months. Traditional cybersecurity architectures weren't ready for such changes.
Vulnerable companies provided an immense opportunity for attackers and criminal organizations, which quickly jumped on the occasion and started inflicting great deals of damage worldwide. Statistics are well known. Year-to-year, cyberattacks exploded in number by two and even threefold. In most cases, companies were first hit by phishing attacks that helped attackers deliver a payload or gain initial access.
You also have to count on the democratization of cyber criminality. Today, almost anybody with some good (wrong) will have their hands on some ransomware kit for less than $100. Of course, some kits are better (cost more, up to the tens of thousands) than others and back you up with more chances of success. Still, the general environment is becoming increasingly hostile, with millions of potential attackers.
Back to the work environment. Given that human interactions were reduced to the bare minimum, employees had to use emails to contact their colleagues, clients, or even personal relationships on their devices (we all know someone who keeps doing this...). Campaigns of indiscriminate and massive phishing emails were reported. Still, we also saw a recrudescence of spear-phishing attacks, where attackers targeted a precise person, which requires more resources, preparation, and determination, resulting in a better chance of success than usual phishing emails.
The number of attacks soared in 2020, and 2021 continued on its track and broke the record. 2022 is already on a solid path to, at the bare minimum, keep up with the precedent for a couple of years. Further, attacks are also complex.
Complexification of attacks
Attacks did not only grow in number but also in complexity for a substantial number of them. Zero-day vulnerabilities tend to be exploited quickly by attackers, but also new Remote Code Execution techniques are an easier way to gain access to a network. For instance, in March 2021, days after the Microsoft Exchange Server vulnerability was revealed and classified by the Mitre Corporation, the Proof-of-Concept was available on GitHub. Several cybersecurity research companies tracked the evolution of attacks using this exploit. They noticed an exponential growth of such attacks in a matter of days. The same goes for Log4j exploits, which we've already reported. Attacks using it grew sharply in a matter of days.
Besides exploiting previously unknown vulnerabilities, such attacks are fileless or malwareless, making it harder for traditional tools to detect. Indeed, such tools traditionally target malicious processes. Meanwhile, these attacks rely on the execution of native binaries. To detect these, SecOps needs to flag specific queries or add a behavioral analytic solution to their technology stack, which must be integrated with their environment to show maximum results.
Furthermore, such attacks pave the way for others. Usually, such exploits are used to gain access and escalate privileges into your networks. Once done, attackers can pursue their attack according to the MITRE ATT&CK framework until Impact, which is usually the stage end-users witness in ransomware attacks when the device gets encrypted and the screen goes scary.
Of course, these attacks are also becoming deadlier, adding to the challenge. Total cost is growing, meaning that organizations suffer more significant data breaches, get more time to return to normal, and face higher fines because of the lack of compliance regarding regulatory obligations. In ransomware attacks, the ransom asked by attackers is also growing because many organizations prefer to pay the ransom.
Lack of automation
We've reported that SecOps faces many attacks and is growing complexified. To the SecOps guy, this is materialized by an ever-increasing number of alerts coming in every day. Each one of these alerts potentially hides an actual incident. The analyst thus has to undergo basic tasks, such as triaging incidents, to distinguish fake alerts and duplicates from real threats. The analyst must also perform basic tasks such as contextualization enrichment to confirm or infirm.
Still, these tasks require different tools provided by different vendors. Of course, we're not advocating resolving this first issue by purchasing an all-in-one solution. We strongly believe that each one has its solution for solving problems. Suites or "one-size-fits-all" cannot answer a company's particular issue. But, there is a lack of integration of the whole stack, a kind of glue holding every piece together and making the structure coherent. This leads to the known "pain-of-glass issue. As essential as it can be, each task takes time and energy, although it does not bring substantial value. Furthermore, being repetitive, these tasks are prone to errors, impeding the whole security architecture.
This is why SOAR solutions were built in the first place—to help and empower every analyst. A few years after the concept was coined and prominent actors emerged, there's still a critical need for automation, from triaging to incident response. It is still reported as one of the significant challenges SecOps has to face.
SecOps technologies to diversify further, notably in the cloud
Although SecOps already has to compose an extensive set of tools to fulfill core functions such as Monitoring, Vulnerability Management, Incident Response, Threat Intelligence, and Insider Risk, this set of functions is vowed to diversify in the near future.
Indeed, following new usages such as those induced by the increasing movement towards the cloud, SecOps has to adapt. As the migration expands, unknown risks and vulnerabilities emerge. Access and work from anywhere are rebalancing the old security architecture. The fortress isn't sufficient to cover the evolution of risks as the castle becomes accessible from anywhere.
Thus, when surveyed, SecOps teams envision adopting Cloud security functions to adapt their security architecture.
However, besides best-in-class SecOps, many teams struggle to integrate their different solutions. Thus, communication and processes between these different layers are fragmented. As we've demonstrated in previous articles, mainly about IAM and PAM, real-time communication is paramount for modern SecOps because of the sheer amount of alerts to process and the need to maintain constant activity. In that sense, streamlining the communication between your existing tools is a top requirement today. This is why we see that, among their top challenges, SecOps teams list automation and orchestration capacities.
Adding new technologies to this already complex stack will ultimately make their work even more complex, thus increasing the need for more integration and, therefore, Orchestration and Automation.
Next-Generation SOAR to enhance staff capabilities
As of today, integration into your environment is still needed. Achieving this would enable real-time communication, in both ways, between your technologies. This took the old SecOps steps by allowing data collection, analytics, and incident response workflows, thanks to an automation engine based on events, actions, and logic. As a result, the SOAR has been rapidly seen as a backbone of your cybersecurity architecture. It enables your team to orchestrate and automate all their processes from one point.
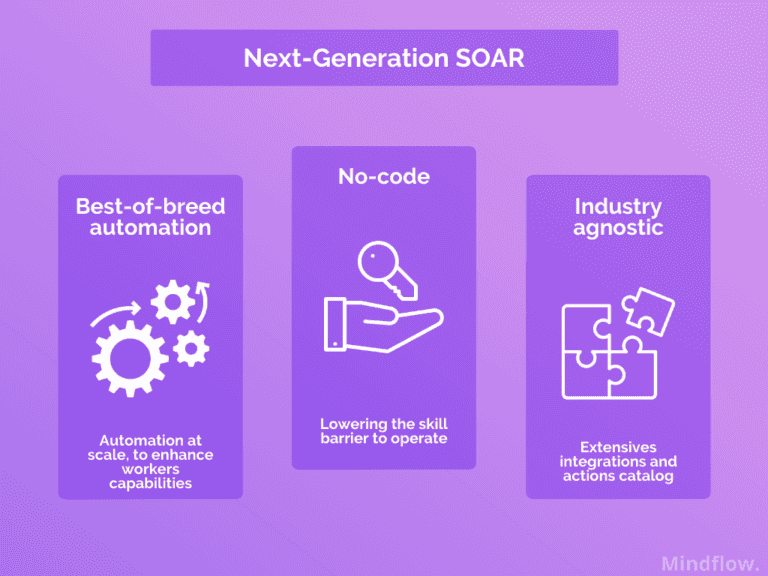
The first generation of SOAR was too complex to operate. Experts designed it for experts. Overall, it was insufficient to tackle SecOps challenges, as noted here. It undeniably saved analysts time and effort and allowed for operations consistency, but the need is still present.
Today, a new generation of SOAR arises. The focus is set on user experience. As a backbone, the SOAR has to be easy to operate to enable automation at scale and prepare your SecOps team for hyperautomation shortly. New and independent actors are developing solutions like Mindflow based on a No-code environment.
Also, the security stack will need further integration capacities when dealing with the increased variety of solutions and the growing need for cloud security solutions. Again, next-generation SOAR enables comprehensive semantic awareness between the whole stack to implement automation and orchestration at all enterprise levels to handle incidents from end to end.







