Today, we’ll see to what extent we can automate the usage of AWS CloudTrail and specifically help an analyst analyze API calls in AWS CloudTrail.
CloudTrail is one of these ultra-popular AWS services widely used across organizations that run on AWS. Popular because it’s one of the fundamental bricks of your cloud architecture when acquiring visibility about what has been performed.
To summarize what CloudTrail does, the service records AWS API calls on accounts it’s enabled on. These log files are then stored in an Amazon S3 bucket. The logs deliver helpful information such as the identity of the API caller, the time of the call, the source IP address of the caller, the request parameters, and the response elements returned by the AWS service.
As said above, AWS CloudTrail is widely used by organizations running on AWS. You can perform auditing, troubleshooting, security, cost optimization, automation, and compliance tasks with it. Today, we’ll see the basics steps needed to extract the info from CloudTrail and push it to Jira to create a nice and intelligible ticket by orchestrating 3 tools.
Regarding cybersecurity, what are the uses of analyzing API calls in AWS CloudTrail?
Analyzing API calls in AWS CloudTrail is a task often performed by security analysts. Through the service, they can monitor for suspicious API calls, failed login attempts, or changes in security groups, audit and validate compliance with security frameworks or regulations, and identify users according to their activity or accesses. Through CloudTrail, users can gather elements about an API call’s Who, What, When, and Where.
This can be particularly useful for monitoring users’ activity in your organization:
- Identifying inactive users: By analyzing CloudTrail logs, you can identify users who have not made any API calls in a certain period. This can help you identify users who may no longer need access to your resources and can be removed from IAM.
- Detecting users with excessive permissions: through logs, you can see users who have been granted excessive permissions and thus may be a security risk and should be removed or their permissions adjusted.
- Auditing user deletion: CloudTrail logs can be used to audit when a user is deleted from IAM, which can help detect any unauthorized deletion of users.
- Monitoring for unnecessary privilege escalation: CloudTrail logs can also be used to monitor for unnecessary privilege escalation by identifying users frequently making API calls with escalated permissions.
How does it typically work from the analyst’s standpoint?
Now that we’ve seen what purpose can be achieved with CloudTrail let’s see how an analyst would typically use it when investigating a particular user. From the analyst standpoint, the process of analyzing API calls in AWS CloudTrail typically involves the following steps:
- Collecting CloudTrail logs: CloudTrail logs are delivered to an Amazon S3 bucket, where they can be collected and stored for analysis.
- Parsing and filtering the logs: The raw CloudTrail logs are in JSON format and can be parsed and filtered using tools such as AWS Glue, Amazon Athena, or third-party log analysis tools. This allows analysts to focus on specific events or specific users.
- Visualizing the data: The parsed and filtered CloudTrail logs can be visualized using Amazon QuickSight or third-party log analysis tools to gain insights into resource usage patterns and identify areas of concern.
- Investigating and taking action: Based on the insights gained from visualizing the data, analysts can investigate specific events or users and take action as needed. For example, they can identify inactive users and remove them from IAM or identify users with excessive permissions and adjust their permissions accordingly.
- Auditing and compliance: The analysis process should include regular data auditing, with compliance checks and alerts as necessary.
From what we have just seen, the traditional process of analyzing CloudTrail logs involves collecting and analyzing large amounts of log data. It requires technical skills, such as data parsing and filtering, thus the knowledge of a programmatic language, and analytical skills, such as identifying patterns and taking appropriate actions.
Automation of the analysis of API calls in AWS CloudTrail through Mindflow
Integrating AWS Cloudtrail enables Mindflow’s users to jump over technical steps and focus on analytical skills, where human cognition brings the most value to a process. Typically, the user can automate the logs’ gathering, parsing, and filtering to generate clear reports written in clear language instead of JSON.
- The data in the CloudTrail logs can be extracted from the notification through Mindflow’s data picker tool to be formatted into natural language.
- Once formatted, the analyst can use the data to populate a Jira ticket with the relevant fields (date, IP, name, etc.) or a message on the internal communication tool of your choice.
- Doing so enables your analyst to get the report in an understandable language without logging in to AWS CloudTrail and analyzing the logs. This will help in easing the decision-making process.
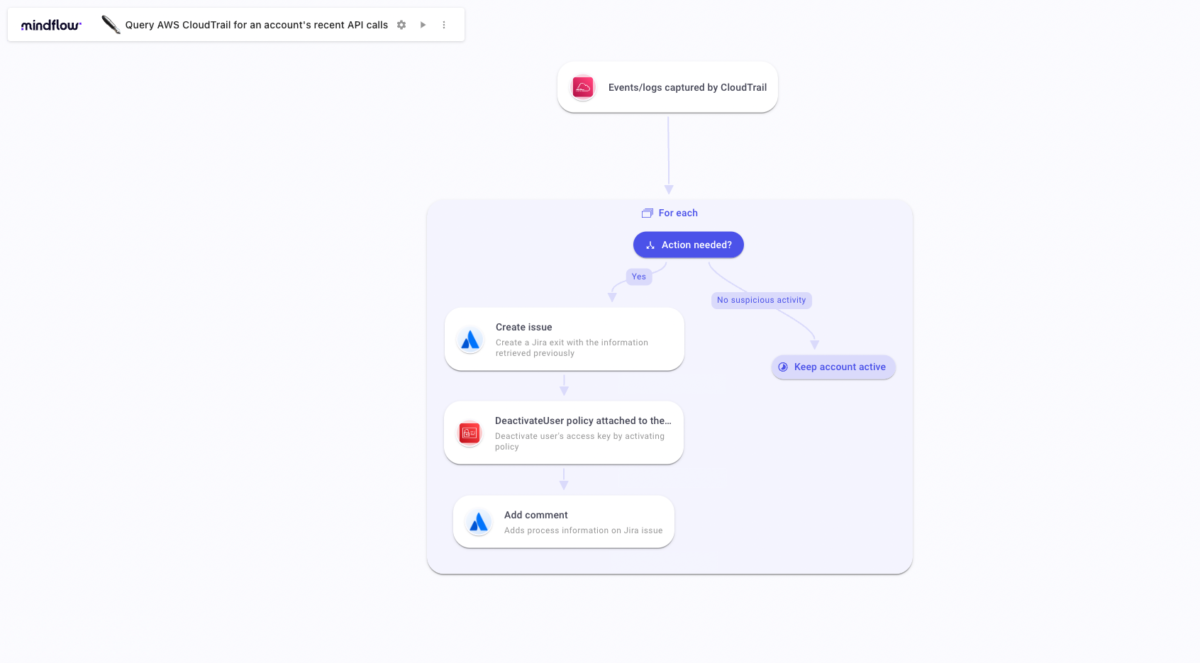
In the following Flow, we can imagine that among the API calls that are returned on a given timeline, one can show an unusual action performed by a user. Having the data gathered in the Jira ticket, the analyst can decide to investigate further by notifying the owner of the API call and deciding to deactivate the user if needed.
This Flow can easily be nested in one another, like one where we look to automate the deactivation of inactive users. Having this Flow nested would help the analyst gather enough information about a particular user (permissions, groups, last API calls, for instance) before acknowledging their deactivation/deletion.