As organizations increasingly rely on technology to conduct business, the need for robust cybersecurity measures has never been greater. Cyber attacks can be costly and their consequences are constantly increasing, both in terms of financial losses and damage to an organization’s reputation. To combat these threats, many organizations have grown their investments in cybersecurity tools to protect their assets and data.
The number of vendors has also surged. Every day a new platform is created to solve existing or new issues that organizations face. With so many options available, choosing the right tool for your organization can be challenging: does it fit in my current stack? Will I be able to use it properly? Is it safe? And so on.
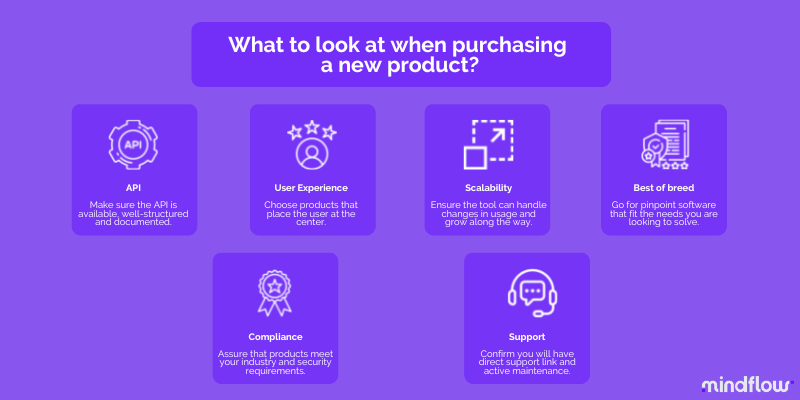
In this article, we’ll explore six things to consider when purchasing a new cybersecurity tool. From API documentation to user experience, we’ll cover the key factors that can help ensure your SecOps teams harness this new tool in the best way possible for them and your organization.
What’s in the API
A well-documented API can be very valuable for organizations that want to integrate their cybersecurity tools into an orchestration and automation platform, such as Mindflow. An API that is clear and easy to use can make it easier for developers to create workflows and automate processes that involve multiple security tools.
This supports our belief that automation is critical to solving structural frictions in cybersecurity, as we have already demonstrated in this blog.
Thus, a clear and well-structured API makes it easier to integrate the cybersecurity tool with other applications or systems in the organization that would otherwise create a tool sprawl phenomenon, where users have to switch between dozen of tools and end up not using all of them in the best manner possible. APIs help to create workflows to improve the overall efficiency of your SecOps.
So, when evaluating cybersecurity tools, looking for a vendor that provides a well-documented API with clear instructions and examples is essential. The API should be easy to access and use, with good documentation that clarifies how to authenticate, make requests, and receive responses.
It’s also important to consider the security implications of using an API to integrate with a cybersecurity tool. Ensure the API is secure and provides the necessary access controls and permissions to protect sensitive data.
Focusing on state-of-the-art User Experience, try before buying
Another essential factor to consider is the User experience. User experience designates the usability and understandability of the tool.
A tool that is user-friendly and easy to navigate can save your SecOps team time and resources. Look for tools with a simple, intuitive interface and helpful documentation or tutorials. This will make it easier for your team to use the tool effectively, resulting in better protection for your business. A user-friendly security tool also makes employees more likely to use it, reducing the risk of human error.
User experience is a critical factor to consider when choosing a cybersecurity tool. A tool with a good UX can make it easier for end-users to understand and use the tool, reducing the risk of errors or mistakes that could compromise security when they have to put their hands in it.
A tool with a good UX should be intuitive, easy to navigate, and well-designed. It should place the end-user at the center of its thinking, focusing on meeting the needs and requirements of the users who will be working with the tool regularly. Another critical aspect of UX is understandability. A good cybersecurity tool should be understandable to dev and non-dev users with various skills and expertise.
One way to ensure the tool you’re considering has a good UX is to ask for a trial and closely monitor this period to collect feedback from the employees that will use it.
Does it scale?
Choosing a tool that can grow with your organization’s needs is essential. You don’t want to invest in a solution that will become obsolete or need to be replaced in a short period.
Scalability refers to the ability of a tool to grow and adapt to the changing needs of your organization over time. This includes handling increased workloads, supporting additional users, and accommodating new features or functionality.
One option for scalability is to choose a cloud-native SaaS (Software as a Service) that typically provides much higher flexibility and scalability, as the tool can be easily scaled up or down to meet changing demands. Cloud-based solutions can also offer lower upfront costs, easier deployment, and automatic updates.
However, it’s important to note that not all cybersecurity tools are available as SaaS. In some cases, organizations may prefer to choose an on-premise solution that they can host themselves, which can provide more control and security. In these cases, scalability will involve adding additional hardware or software components to the existing infrastructure as needed.
To sum up, about the scalability aspect of a considered new tool, it’s essential to consider how it will fit into your organization’s long-term growth and development plans and choose a solution that can adapt and evolve along with your organization.
Going for best-of-breed
When evaluating different options, always have in mind the need you identified and that you want to fulfill and look for the tool that is supposedly the best match.
Choosing a cybersecurity tool that is laser-focused and tailored to the specific needs of an organization is more than often a more effective approach than opting for an all-in-one solution. Pinpoint solutions are usually more cost-effective, as organizations only pay for the features they need rather than a suite of features they may not use.
In addition, pinpoint solutions can be more flexible and adaptable, allowing organizations to choose the best solution for each specific cybersecurity need. All-in-one solutions can be limited in addressing an organization’s unique requirements and may not be the best fit for every company. The integration of such solutions to the broader tech stack, which many fear, can be handled through its orchestration on an Orchestration and Automation platform, such as Mindflow, hence the need to have a clearly documented API.
All-in-one solutions can also lock users into a specific vendor ecosystem, making it difficult to switch to another solution if the organization’s needs change. This can lead to vendor lock-in syndrome, limiting innovation and hindering progress. On the other hand, pinpoint solutions can offer more innovation and faster updates, as vendors can focus on developing and improving specific features rather than trying to manage a complex suite of features.
Check the compliance
First, depending on your industry, you may need to meet specific regulations or compliance standards. You should ensure that the tool you choose complies with these regulations and standards, such as PCI DSS, HIPAA, etc.
Furthermore, since cybersecurity tools require a deeper level of integration within your organization’s infrastructure than ordinary tools, it is all the more necessary to be able to verify the compliance of the vendor and the platform under review with internationally recognized standards such as ISO/IEC 27001 and/or SOC 2 to ensure that core security measures and controls are adequately implemented.
Of course, when it comes to data being processed, you need to ensure that the product you’re considering is handling in a proper manner your data, and all the more your personal data, according to the applicable legislation such as the GDPR or the CCPA.
Level of support provided
Finally, consider the support offered by the vendor. Ensure that the vendor provides direct support through the platform and that the tool is appropriately maintained and updated. This will ensure you can access the latest features and security updates and get help quickly if you encounter any issues.
When purchasing a security tool, it’s thus essential to ensure that you have access to the support you need, so you can ensure that the newly acquired product will be maintained up-to-date by the vendor, run properly, and most of all, know where to ask in case of issues when using it.
Conclusion
In conclusion, when purchasing a new cybersecurity tool, keep in mind the followings:
- API
- User Experience
- Scalability
- Best-of-breed
- Compliance
- Support
By considering these factors, you can make an informed decision to purchase a cybersecurity tool that will help ensure that your business’s sensitive data and assets are well-protected and that your employees will be able to integrate this new cybersecurity tool into your existing tech stack and, ultimately, orchestrate and automate it.
